# Inctfj Writeups
## hi_dora!
Author :[Pavani](https://twitter.com/Paavani21)
### Description
My friend send me some symbols as message , can you help in finding the message ?
### Difficuilty level:
Beginner
**Note**:
* separate each word with with underscores
* Make sure flag is in UPPERCASE
Given symbols
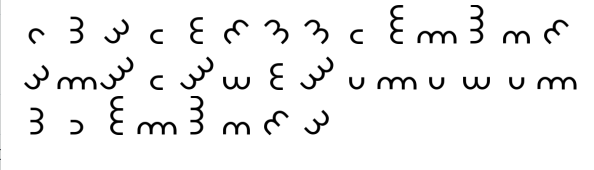
### flag format :
`inctfj{}`
### writeup:
This challenge requried some googling.
This is dorabella cipher encryption

#### flag
inctfj{DORABELLA_CIPHER_IS_A_SUBSTITUTION_CIPHER}
## Robin_Messup
### Description
My friend Robin messed up his RSA implementation. Can you recover his flag?
### Difficuilty level:
Easy
### challenge file :
```python=
from Crypto.Util.number import *
from gmpy2 import next_prime
from sec import flag
pt=bytes_to_long(flag)
def gen(bits,x=4):
while x%4!=3 and next_prime(x)%4!=3:
x=getPrime(bits)
return x,next_prime(x)
p,q=gen(512)
n=int(p*q)
e=2
ct=pow(pt,e,n)
print(f"{ct=}\n{n=}")
```
```out.py
ct=97164848935823065521135599772159530380646470462425129406694351200300719639554216388931686974833039404371267194789570395859750057120009115257307882729661147834730677444686091945619846724604887089301953951580298260093584196923514906571256422842532159844807478497230257915521137217779726510365556765891785240070
n=115501763520199504267863278867231366791243066415923062085068452551070578902742421438216148508603747484683326089179274060544643962245756203673763625399020828126506136917556657586116664207969450417763794906690080814941797412370270554563445645724404887075419468014077334785807019855546639240753158255429453132869
```
#### Short writeup
If you see challenge file script,public exponent is even. In rsa e is always odd in RSA. Here it is even. It is [Rabin cryptosystem](https://en.wikipedia.org/wiki/Rabin_cryptosystem).
`e = 2` in Rabin cryptosystem.
**Script:**
```python=
from sympy import gcdex,factorint
for f in open("out.txt").readlines():
exec(f)
e=2
p,q=factorint(n)
yp,yq,_=gcdex(p,q)
mp,mq=[pow(ct,(i+1)//4,i) for i in (p,q)]
r1=(yp*p*mq+yq*q*mp)%n
r3=(yp*p*mq-yq*q*mp)%n
r2,r4=-r1%n,-r3%n
print(*[bytes.fromhex(hex(i)[2:]).decode('latin-1') for i in[r1,r2]],sep='\n')
```
#### flag:
``inctfj{65c651eafa22718c09d424c7dd2c42ebcce76147a3d47e05fd24d4ae984b6129}``
## RSAsign
### Description
find the message from signature
###
### Challenge file:
```out.py
p = 141425761750882434366113656037465528064446934590747547591913071247558071478523067775424339379902549140682388121246592146755332109704901386671558886860468710289573558030527361687830155654271762079747974119304854799444200892494664030121777764817864236066664814388946471337642691402213002167546534086524889151493
q = 157006051551554749447948461154166069280741233539909038877122296628155250472027778739586210291284924672264398178997704838753197073588553771894828080321619242495586214068036432855351448569359716239160693646942321157830455018125670551341322931414201893347339591241482474678282700265976542303742266087201779118319
e = 65537
signature = 2112725697240595792338701104840001143105965314009156886758430753729193280917949645949820751211929763090437984980301037272483245987121865425732864547619608106734040120161884684992084596683982376255405798908194228334042557434837256225901893398809467675789217016362545151175974485530888560500121637059987930493557119933717786703106790019551747187242238955973359471090349554986964676080526448248540408943974798265451208246715054141505165525705935485755789725530105006544991426436628768665983658789316761905500686591386455067164175303618412422630098909099013374440591654272123046548115834893961071864282501944948618397178
```
### Short writeup:
We have p,q,e,signature.Now we have to find the original equation from n,e,signature
We know that,
$s = m^d$ mod n
signature = pow(bytes_to_long(message),d,n)
m = $s^e$ % n
calculate n => n = p*q
```python=
from Crypto.Util.number import *
msg = pow(signature,e,(p*q))
msg = long_to_bytes(msg)
print(msg)
```
##### flag:
``inctfj{bob_was_authenticated_by_alice}``
 Sign in with Wallet
Sign in with Wallet

