---
tags: vaje, kirv, lfsr, shannon
hackmd: https://hackmd.io/GWYe1z9cQKmIrnD7WsjjLQ
plugins: mathjax
---
# Cryptography and computer security - Tutorial 27.10.2020
---
## Linear feedback shift registers (LFSR)
Example:
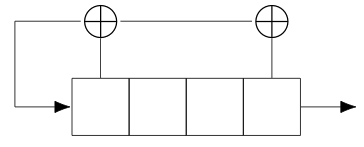
* <i>$z_{i+4} = z_{i+3} + z_i$</i>
* <i>$z_{i+n} = \sum_{j=0}^{n-1} c_j z_{i+j}$</i>
* <i>$0 = -z_{i+n} + \sum_{j=0}^{n-1} c_j z_{i+j}$</i>
* <i>$C(x) = -1 + \sum_{j}^{n-1} c_j x^{n-j}$</i> connection polynomial
### Exercise 1
Check that the polynomial <i>$C(x) = 1 + x + x^4$</i> is irreducible over <i>$\mathbb{Z}_2$</i>. Is it also primitive over <i>$\mathbb{F}_{2^4}$</i>?
----
<i>$C(x) = A(x) B(x)$</i>
* irreducible polynomials of degree <i>$1$</i> over <i>$\mathbb{Z}_2$: $x$, $x+1$</i>
* irreducible polynomials of degree <i>$2$</i> over <i>$\mathbb{Z}_2$: $x^2 + x + 1$</i>
```
(x^4 + x + 1) / (x^2 + x + 1) = x^2 + x
- (x^4 + x^3 + x^2)
x^3 + x^2 + x + 1
- (x^3 + x^2 + x)
1
```
Hence, <i>$C(x)$</i> is **irreducible** over <i>$\mathbb{Z}_2$</i>.
* <i>$2^4 - 1 = 15 = 5 \cdot 3$</i> non-zero elements of <i>$\mathbb{F}_{2^4}$</i>.
* <i>$C(x)$</i> is **primitive** over <i>$\mathbb{F}_q$</i> if the lowest <i>$t$</i> such that <i>$C(x)$</i> divides <i>$x^t - 1$</i> equals <i>$q^d - 1$</i>, where <i>$d$</i> is the degree of <i>$C(x)$</i>.
```
(x^5 + 1) / (x^4 + x + 1) = x
- (x^5 + x^2 + x)
x^2 + x + 1
(x^15 + 1) / (x^4 + x + 1) = ...
```
<i>$C(x)$</i> is **primitive** over <i>$\mathbb{F}_{2^4}$</i>.
---
### Exercise 2
Generate output sequences for an LFSR of degree <i>$4$</i> with connection polynomial <i>$C(x)$</i> and all possible initial states. What are their periods?
----
```
0|0|0|0|0|0|0|0|0|... period 1
000111101011001|0001 period 15
```
---
### Exercise 3
Determine all possible periods of LFSRs defined by the equations
1. <i>$s_{i+3} = (s_i + s_{i+1} + s_{i+2}) \bmod{2}$</i>,
2. <i>$s_{i+4} = (s_i + s_{i+1} + s_{i+2} + s_{i+3}) \bmod{2}$</i>,
3. <i>$s_{i+4} = (s_i + s_{i+1} + s_{i+2} + s_{i+3}) \bmod{5}$</i>,
4. <i>$s_{i+4} = (s_i + s_{i+1} + s_{i+2} + s_{i+3}) \bmod{10}$</i>.
----
1. ```
0|000 period 1
0011|001 period 4
01|010 period 2
1|111 period 1
```
$C_1(x) \equiv 1 + x + x^2 + x^3 \equiv (1 + x) (1 + x^2) \equiv (1 + x)^3 \pmod{2}$
2. ```
0|0000 period 1
00011|0001 period 5
00101|0010 period 5
01111|0111 period 5
```
<i>$C_2(x) \equiv 1 + x + x^2 + x^3 + x^4 \pmod{2}$</i>
```
(x^5 + 1) / (x^4 + x^3 + x^2 + x + 1) = x + 1
- (x^5 + x^4 + x^3 + x^2 + x)
x^4 + x^3 + x^2 + x + 1
- (x^4 + x^3 + x^2 + x + 1)
0
```
<i>$C_2(x)$</i> is **not primitive** over <i>$\mathbb{F}_{2^4}$</i>.
---
### Exercise 4
Determine whether an LFSR of degree <i>$4$</i> can generate sequences
1. <i>$1011010000101\dots$</i> and
2. <i>$(011101110)^*$</i>.
---
### Exercise 5
Find an LFSR of degree <i>$4$</i> that generates the sequence <i>$10101100$</i>.
---
## Shannon theory
### Exercise 6
Prove that a cryptosystem has perfect secrecy if and only if
$$
P(Y = y \mid X = x_1) \ = \ P(Y = y \mid X = x_2)
$$
for all <i>$x_1, x_2 \in \mathcal{P}$</i> and <i>$y \in \mathcal{C}$</i>.
---
### Exercise 7
Consider a cryptosystem in which <i>$\mathcal{P} = \lbrace a, b \rbrace$</i>, <i>$\mathcal{K} = \lbrace k_1, k_2, k_3 \rbrace$</i> and <i>$\mathcal{C} = \lbrace 1, 2, 3 \rbrace$</i>. Suppose that keys are chosen with probabilities <i>$P(K = k_1) = 1/2$</i>, <i>$P(K = k_2) = P(K = k_3) = 1/4$</i>, and plaintexts are chosen with probabilities <i>$P(X = a) = 1/4$, $P(X = b) = 3/4$</i>. The encryption matrix is as follows:
| <i>$E_k$</i> | <i>$a$</i> | <i>$b$</i> |
| ------------ | ---------- | ---------- |
| <i>$k_1$</i> | 1 | 2 |
| <i>$k_2$</i> | 2 | 3 |
| <i>$k_3$</i> | 3 | 1 |
1. Compute the probability measures on the ciphertext, i.e., <i>$P(Y = y)$</i> for all <i>$y \in \mathcal{C}$</i>.
2. Prove that this cryptosystem does not provide perfect secrecy.
3. Modify the plaintext and/or key distributions in such a way that perfect secrecy is obtained.
---
### Exercise 8
Prove that the affine cipher over <i>$\mathbb{Z}_{26}$</i> achieves perfect secrecy if every key is used with equal probability <i>$1/312$</i>.
 Sign in with Wallet
Sign in with Wallet

