---
title: Istio
tags: Istio
---
# workshop
[istio workshop](https://www.istioworkshop.io/)
[安裝istio-snippets](https://marketplace.visualstudio.com/items?itemName=MakeOptim.istio-snippets)
[安裝User-agent Switcher](https://chrome.google.com/webstore/detail/user-agent-switcher-for-c/djflhoibgkdhkhhcedjiklpkjnoahfmg/related)
[what's my user agent](https://www.whatsmyua.info/)
[Kubernetes Ingress controllers comparison](https://docs.google.com/spreadsheets/d/1DnsHtdHbxjvHmxvlu7VhzWcWgLAn_Mc5L1WlhLDA__k/edit#gid=0)
# URL

# Service mesh

# Envoy
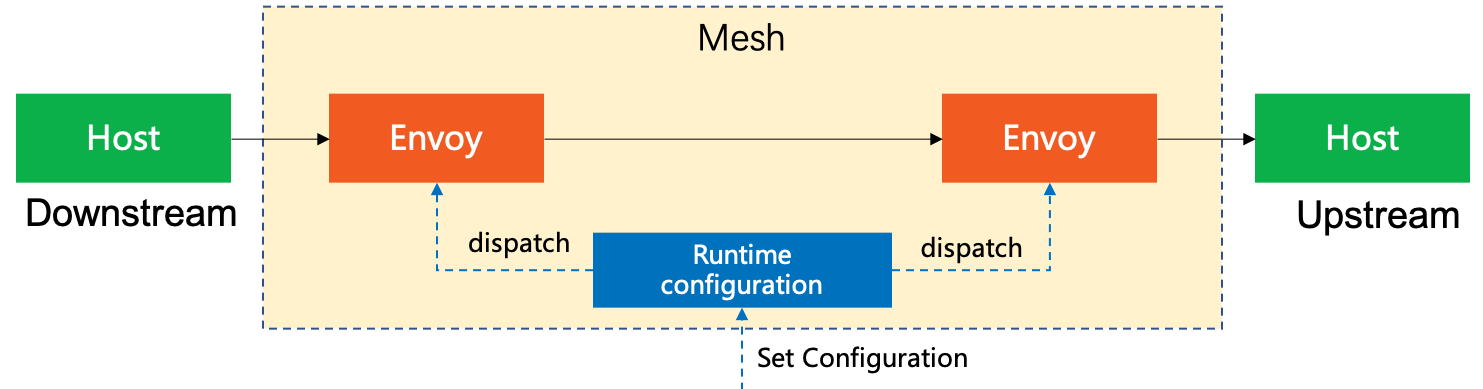
| 術語 | 說明 |
| -------- | -------- |
| Downstream | 前端 |
| Upstream | 後端 |
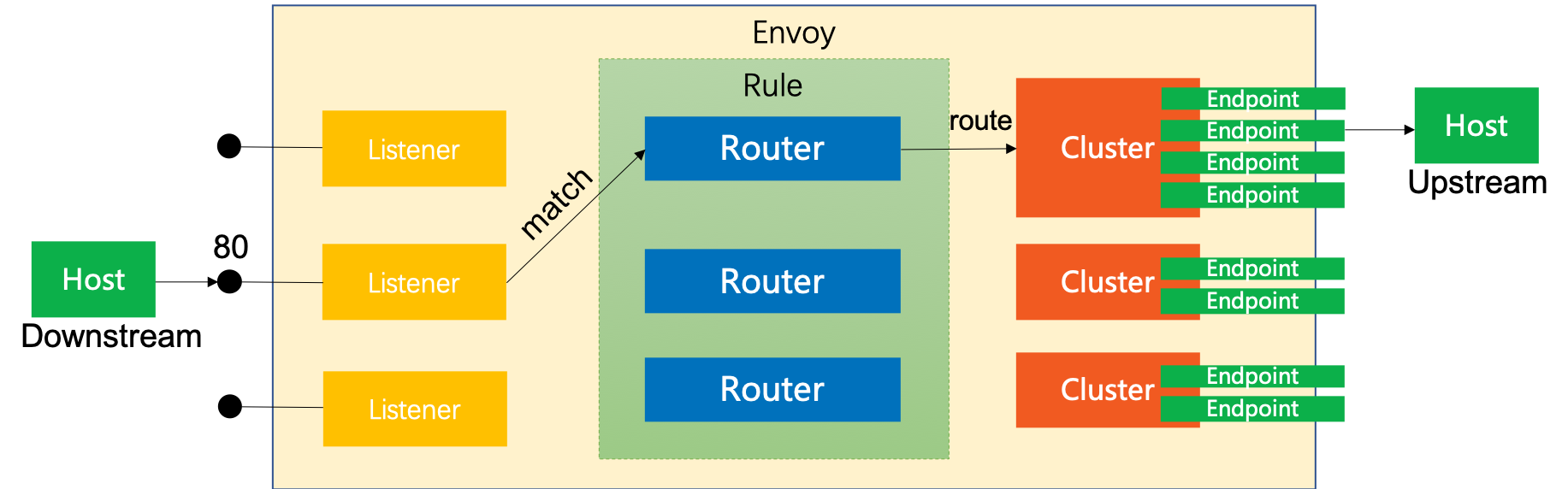
| 術語 | 說明 | ex |
| -------- | -------- | -------- |
| Listener | 前端監聽的位址 | www.example.com, 123.123.123.123 |
| Router | 路由規則 | 443 -> 80, path strip, add/remove header ... |
| Cluster | 後端服務的集合 | web server cluster |
| Endpoint | 後端服務的port | 80 port |
| Host | 服務主體 | web01, web02, web03 |
# Envoy xDS API
* CDS(Cluster Discovery Service)
* EDS(Endpoint Discovery Service)
* HDS(Health Discovery Service)
* LDS(Listener Discovery Service)
* MS(Metric Service)
* RLS(Rate Limit Service)
* RDS(Route Discovery Service)
* SDS(Secret Discovery Service)
* ADS (Aggregated Discovery Service)
# Istio
* Mixer: 負責整個服務網格中的存取控制,使用策略,數據收集
* Pilot: 提供流量控制,路由,超時,重試,斷路器
* Citadel: 負責服務之間認證以及憑證管理等功能

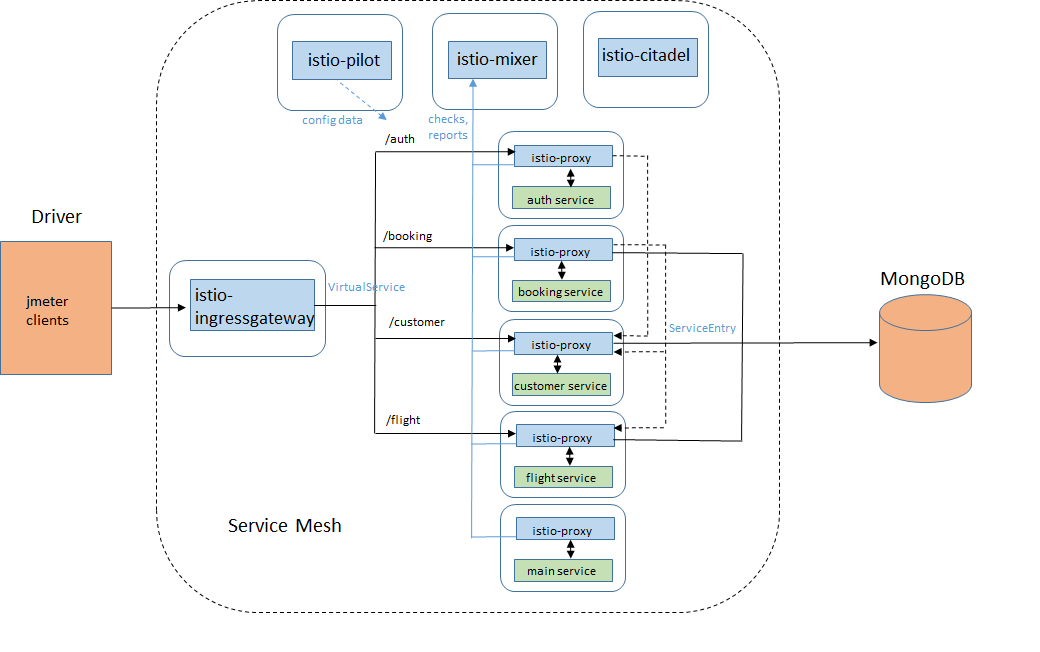
| 術語 | 縮寫 | 說明 |
| -------------------- | -------- | -------- |
| ingress gateway | gw | 前端 |
| VirtualService | vs | 後端 |
| DestinationRule | dr | 路由規則 |
| egress gateway | x | 外部資源 |
| serviceEntry | x | 外部資源 |
---
# Install istio
下載最新版本
```bash=
curl -L https://istio.io/downloadIstio | sh -
```
下載指定版本
```bash=
curl -L https://istio.io/downloadIstio | ISTIO_VERSION=1.6.8 TARGET_ARCH=x86_64 sh -
```
設定環境變數
```bash=
export PATH=$HOME/istio-1.7.3/bin:$PATH
```
istio安裝參數
```bash=
istioctl install \
--set values.global.proxy.holdApplicationUntilProxyStarts=true \
--set values.gateways.istio-ingressgateway.type=NodePort \
--set meshConfig.accessLogFile=/dev/stdout \
--set meshConfig.accessLogEncoding=JSON
```
| 參數 | 說明 |
| -------- | -------- |
| holdApplicationUntilProxyStarts | 啟動完istio元件後,再啟動app pod |
| istio-ingressgateway.type | ingressgateway type |
| meshConfig.accessLogFile | 啟動envoy log |
| meshConfig.accessLogEncoding | log type |
更新ingress-gateway的nodeport為30080
```bash=
kubectl patch svc istio-ingressgateway --patch '{"spec":{"ports":[{"port": 80, "nodePort":30080}]}}' -n istio-system
```
Addon
```bash=
kubectl apply -f istio-1.7.3/samples/addons
```
# Sidecar injection
```bash=
# 手動注入
istioctl kube-inject -f deployment.yaml | kubectl apply -f -
# 自動注入
kubectl label namespace default istio-injection=enabled
# spec.temeplate.metadata.annotation
sidecar.istio.io/inject: "false"
```
[sidecar injection](https://istio.io/v1.1/help/ops/setup/injection/)
[Istio injector annotations don't work
](https://github.com/istio/istio/issues/6476)
**結論**: 啟用namespace自動注入,再用annotation控制
# Ingress Gateway
```bash=
cd ~/istio-1.7.3/samples/addons
kubectl apply -f prometheus.yaml
kubectl apply -f grafana.yaml
kubectl apply -f jaeger.yaml
kubectl get pod,svc -n istio-system
```
```bash=
NAME READY STATUS RESTARTS AGE
pod/grafana-75b5cddb4d-r4jd6 1/1 Running 0 82s
pod/istio-ingressgateway-78b6cf98f4-5dm5j 1/1 Running 0 2m41s
pod/istiod-fb4fbff6b-v7mcv 1/1 Running 0 2m45s
pod/jaeger-5795c4cf99-8c969 1/1 Running 0 67s
pod/prometheus-9d5676d95-5h2gr 2/2 Running 0 75s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/grafana ClusterIP 10.100.49.43 <none> 3000/TCP 82s
service/istio-ingressgateway LoadBalancer 10.108.59.56 localhost 15021:32386/TCP,80:30018/TCP,443:30012/TCP,15443:31938/TCP 2m41s
service/istiod ClusterIP 10.97.134.135 <none> 15010/TCP,15012/TCP,443/TCP,15014/TCP,853/TCP 2m45s
service/prometheus ClusterIP 10.100.21.203 <none> 9090/TCP 75s
service/tracing ClusterIP 10.98.158.159 <none> 80/TCP 66s
service/zipkin ClusterIP 10.110.33.86 <none> 9411/TCP 66s
```
```yaml=
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: addon-gateway
spec:
selector:
istio: ingressgateway
servers:
- port:
number: 80
name: http
protocol: HTTP
hosts:
- prometheus.127.0.0.1.nip.io
- grafana.127.0.0.1.nip.io
- jaeger.127.0.0.1.nip.io
- whoami.127.0.0.1.nip.io
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: grafana
spec:
hosts:
- grafana.127.0.0.1.nip.io
gateways:
- addon-gateway
http:
- route:
- destination:
host: grafana.istio-system.svc.cluster.local
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: jaeger
spec:
hosts:
- jaeger.127.0.0.1.nip.io
gateways:
- addon-gateway
http:
- name: default
match:
- uri:
prefix: /jaeger
route:
- destination:
host: tracing.istio-system.svc.cluster.local
---
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: prometheus
spec:
hosts:
- prometheus.127.0.0.1.nip.io
gateways:
- addon-gateway
http:
- match:
- headers:
user-agent:
exact: "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10; rv:33.0) Gecko/20100101 Firefox/33.0"
route:
- destination:
host: prometheus.istio-system.svc.cluster.local
```
```bash=
kubectl get gw,vs
```
```bash=
NAME AGE
gateway.networking.istio.io/addon-gateway 2s
NAME GATEWAYS HOSTS AGE
virtualservice.networking.istio.io/grafana [addon-gateway] [grafana.127.0.0.1.nip.io] 2s
virtualservice.networking.istio.io/jaeger [addon-gateway] [jaeger.127.0.0.1.nip.io] 2s
virtualservice.networking.istio.io/prometheus [addon-gateway] [prometheus.127.0.0.1.nip.io] 2s
```
# Traffic Management
[traefik/whoami github](https://github.com/traefik/whoami)
## deployment
* template.metadata.annotations
* labes: app, version
```shell=
apiVersion: apps/v1
kind: Deployment
metadata:
name: whoami-v1
spec:
selector:
matchLabels:
app: whoami
version: v1
template:
metadata:
annotations:
sidecar.istio.io/inject: "true"
labels:
app: whoami
version: v1
spec:
containers:
- name: whoami
image: whoami:v1
ports:
- containerPort: 80
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: whoami-v2
spec:
selector:
matchLabels:
app: whoami
version: v2
template:
metadata:
labels:
app: whoami
version: v2
annotations:
sidecar.istio.io/inject: "true"
spec:
containers:
- name: whoami
image: whoami:v2
ports:
- containerPort: 80
```
## service
```shell=
apiVersion: v1
kind: Service
metadata:
name: whoami
spec:
selector:
app: whoami
ports:
- port: 80
targetPort: 80
```
## virtual service
```shell=
# See more at https://istio.io/docs/reference/config/networking/virtual-service/
apiVersion: networking.istio.io/v1alpha3
kind: VirtualService
metadata:
name: whoami
spec:
hosts:
- whoami.127.0.0.1.nip.io
gateways:
- addon-gateway
http:
- name: v1
timeout: 2s
route:
- destination:
host: whoami
subset: v1
weight: 90
- destination:
host: whoami
subset: v2
weight: 10
```
## destination rule
```shell=
# See more at https://istio.io/docs/reference/config/networking/destination-rule/
apiVersion: networking.istio.io/v1alpha3
kind: DestinationRule
metadata:
name: whoami
spec:
host: whoami
subsets:
- name: v1
labels:
version: v1
- name: v2
labels:
version: v2
```
## kubectl get pod,svc,vs,dr
```shell=
NAME READY STATUS RESTARTS AGE
pod/whoami-v1-79f555c9bf-xlxcw 2/2 Running 0 62s
pod/whoami-v2-5d4956f4c7-cnb9j 2/2 Running 0 62s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 6d1h
service/whoami ClusterIP 10.109.26.84 <none> 80/TCP 62s
NAME GATEWAYS HOSTS AGE
virtualservice.networking.istio.io/grafana [addon-gateway] [grafana.127.0.0.1.nip.io] 31m
virtualservice.networking.istio.io/jaeger [addon-gateway] [jaeger.127.0.0.1.nip.io] 31m
virtualservice.networking.istio.io/prometheus [addon-gateway] [prometheus.127.0.0.1.nip.io] 31m
virtualservice.networking.istio.io/whoami [addon-gateway] [whoami.127.0.0.1.nip.io] 62s
NAME HOST AGE
destinationrule.networking.istio.io/whoami whoami 62s
```
 Sign in with Wallet
Sign in with Wallet
 Sign in with Wallet
Sign in with Wallet