# Start Integrating Security Tools in Your Software Development Lifecycle

Photo by [Darya Jum](https://unsplash.com/@darya_jumelya?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText) on [Unsplash](https://unsplash.com/s/photos/pipeline?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText)
Consumers focus on functionality, not underlying security. But on analyzing the damage caused by previous data breaches and hacks, it is easy to see that security flaws can be more catastrophic than errors in functionality, having a direct impact on both customers and sellers.
Keeping an application secure and up to date each time you do a deployment can be overwhelming, especially if you have daily or even weekly release cycles.
Then how can you ensure the integrity of the delivered application without putting an excessive burden on the budget or cutting spending on required functionalities? One effective solution is to integrate application security testing into the software development lifecycle and have it run automatically for each deployment.
## What is DevSecOps?
In the past, application security was an isolated, different from the rest of the development lifecycle, and was assigned to a specific team that tested the application's security at the final stage before it was released or updated. This was not a problem back in the days when development cycles lasted several months. But this is not how software development works these days.
A DevOps approach ensures rapid software implementation along with quick and frequent release. But this must not come at the cost of security. To make the best of an agile initiative like DevOps, IT security must also be integrated and play an active role in the life cycle of your apps.
Such an approach is known as [DevSecOps](https://www.devsecops.org/), a term that emphasizes the need to introduce security as a first approach in software development.

[Image Source](https://phoenixnap.com/blog/what-is-devsecops-best-practices)
## How to Integrate it in your Application Lifecycle
The first step of following a DevSecOps approach is to start thinking about all three---development, deployment and security---as an integral part of the application lifecycle from the very start.
The application is developed by following the best practices in terms of security---issues found during the security testing phase are addressed by the development team before the deployment, outdated packages that have been reported to include vulnerabilities are patched right away and so on.
At the same time, DevSecOps can be visualized as an automated process where you integrate certain tools in your development lifecycle, tools that will perform security audits.
## What Tools to Use?
Most security auditing tools out there can be split into two categories: SAST (static application security testing) and DAST (dynamic application security testing).
### SAST
A tool that fits in the first category, [SAST](https://www.gartner.com/en/information-technology/glossary/static-application-security-testing-sast), will perform a white-box type of testing by analyzing the source code. The advantage of such a tool is that it is easy to integrate and helps developers engage in application security testing in the early stages of development, eliminating the negative consequences of delayed detection of security vulnerabilities.
These tools are easy to integrate and easy to automate so that they can perform audits exactly at the moment of your choosing.
One issue of this type of tool is that the scan can become slow based on the amount of code that needs to be checked and it has a high rate of false positives.
### DAST
A tool that belongs to the second category, [DAST](https://en.wikipedia.org/wiki/Dynamic_application_security_testing), performs a black-box type of testing by testing the application in a test or QA environment. In DAST tools, testing is not done from early stages, but rather once the application is built and up and running.
The benefit of these tools is that they can provide great insights through simulation external attacks on an application that try to penetrate the system. They can highlight memory usage errors, performance issues, injection vulnerabilities and so on.
One issue with this type of tool is that it can be hard to automate and maintain.
### IAST
Another type of tool, more new, is called interactive application security testing (IAST). It is more or less a combination of SAST and DAST tools, taking the best of both.
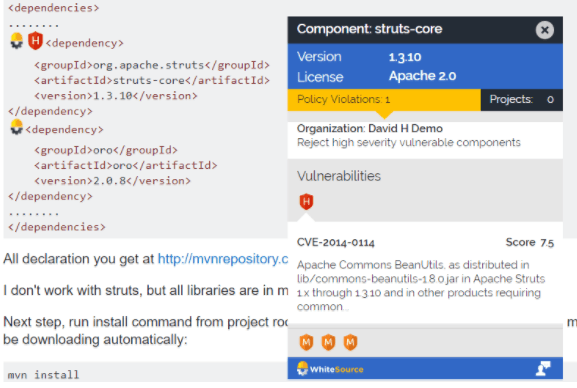
[WhiteSource](https://www.whitesourcesoftware.com/repo-integration/), for example, provides such tools that can be easily integrated in your development lifecycle. WhiteSourcehas a [repository integration](https://www.whitesourcesoftware.com/repo-integration/) feature. Therefore, it can be linked to your favorite GIT platform and can perform automated security audits each time you push or commit some code.
## Should I Integrate It In My App?
Adding new components to your application comes with a cost, even if these tools are automated. So, before adding them,you should consider the need for these applications. These decisions should be made based on the level of your application and on the type of data that your are using.
For simple projects that do not deal with sensitive data from third parties or users, following best security practices when developing the application and even having a simple tool to check for dependencies for updates should suffice. On the other hand, for large applications or for enterprise applications, the cost of adding these tools is much lower than the cost of not having them and dealing with security issues that can escalate.
## Conclusion
Security is an issue that all applications face sooner or later. The only difference is in the type of attacks and vulnerabilities, which are related to the size of your application and the benefits someone can get through these attacks.Therefore, these points of consideration should factor into the steps you take to combat these possible attacks and the complexity of the tools you use.