# Cyber Security </br>and</br>Ethical Hacking
A talk by Rahul Varale
27/11/2021
---
## Who am I?
- Security Analyst 👨💻
- Independant Bug Hunter
- Former Club Head @InfoSec Club IIT Goa
---
## What is Cyber Security?
----
### Cyber Security is ...
----
### Everything is smart!
----
### Nothing is secure!!!
<!-- .slide: data-transition="zoom" -->
----
### Large no. of attacks happen everyday
----
- #### Network Security
- #### Application Security
- #### Information Security
- #### Cloud Security
- #### Internet of Things Security
---
## Cyber Security in news
----
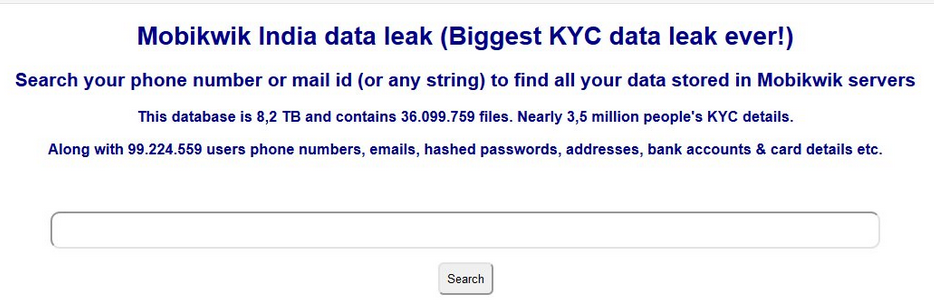
### MobiKwik Data Breach
> “MobiKwik database of 10 crore users leaked on dark web; company denies data breach.”
###### _Source : The Indian Express [Read more](https://indianexpress.com/article/technology/tech-news-technology/mobikwik-database-leaked-on-dark-web-company-denies-any-data-breach-7251448/)_
----
----
### Air India Data Breach
> “A cyber-attack that compromised the data of millions of passengers from across the world involved personal data registered between August 26, 2011 and February 20, 2021.”
###### _Source : The Indian Express [Read more](https://indianexpress.com/article/explained/air-india-sita-data-breach-explained-7325501/)_
----
### Domino's india Data Breach
> “Domino’s India data breach allegedly exposes 1 million credit card details, 180 million order details.”
###### _Source : Business Insider [Read more](https://www.businessinsider.in/tech/news/dominos-india-data-breach-allegedly-exposes-1-million-credit-card-details-180-million-order-details/articleshow/82144019.cms)_
----

----
### Unacademy data breach
----
### BigBasket data breach
----
### Kudankulam nuclear power plant data breach
----
### Justdial data breach
----
### and many more...
----
### See if you’ve been part of an online data breach
#### https://haveibeenpwned.com/
#### https://monitor.firefox.com/
---
## What is Hacking?
----

----
### What is **Ethical** Hacking?
> an **authorized** attempt to gain unauthorized access to a computer system, application, or data. Carrying out an ethical hack involves duplicating strategies and actions of malicious attackers.
----
### You should be aware of cyber attacks otherwise you can also be a victim!
---
## Types of most common cyber attacks
----
1. Malware - Virus, Ransomeware, Spyware
2. Phishing
3. Man-in-the-middle attack (MITM)
4. Distributed Denial-of-Service (DDoS) attack
5. Web Application Attacks
----
### OWASP: Top 10 Web Application Security Risks
----

---
## How do I start my cyber security journey?
----
### Follow the InfoSec community on social media
----
### Capture the flag
----
### Few sites for challenges
- https://ctftime.org/
- https://overthewire.org/
- https://portswigger.net/web-security - This is a very nice lab with a good explanation.
----
The very first skill you need to be a good hacker is to be able to find things by yourself.
----
Be good at **searching** for info & **analyzing** it so you can get the best resources on any subject.
----
### OSINT - Open Source Intelligence
- OSINT is information collected from public sources such as those available on the Internet.
- It doesn't matter if it is located inside newspapers, blogs, web pages, tweets, social media cards, images, podcasts, or videos as long as it is **public, free and legal**.
- **Google Dorks / Google Hacking** https://en.wikipedia.org/wiki/Google_hacking
----
> "Your mind is like an axe to chop a tree: the sharper it is, the faster it gets the job done."
Rodolfo Assis @rodoassis
---
## Its game time!
----
https://easywebctf.vercel.app/
---
# Thank you
# 🙏
---
## Any doubts?
---
## Connect with me
[<span class="fa fa-linkedin-square" style="font-size:40px;color:gray;margin-right:20px;">/rahulvarale</span>](https://www.linkedin.com/in/rahulvarale/)
[<span class="fa fa-facebook-square" style="font-size:40px;color:gray;margin-right:20px;">/VaraleRahul</span>](https://www.facebook.com/VaraleRahul)
[<span class="fa fa-telegram" style="font-size:40px;color:gray;margin-right:20px;">/RahulVarale</span>](https://t.me/RahulVarale)
{"metaMigratedAt":"2023-06-16T15:06:05.212Z","metaMigratedFrom":"YAML","title":"Cyber Security and Ethical Hacking","breaks":true,"slideOptions":"{\"transition\":\"slide\"}","contributors":"[{\"id\":\"e3da85a3-fb39-44fb-872c-cb445f89c8c9\",\"add\":5738,\"del\":3331}]"}