### References
- Homepage: https://meltdownattack.com/
- Meltdown (:icecream:): https://arxiv.org/abs/1801.01207
- Spectre (:ghost:): https://arxiv.org/abs/1801.01203
---
### Common traits
- Researchers (Google P0, UniGratz et al.)
- Disclosure Timeline (end of 2017)
- Root causes (HW design decisions, Out-of-Order execution, speculative engine)
- Recent wave of HW design flaw attacks: RowHammer (2014), MDS (2018), TRRespass (2020)
---
### Broken HW assumption
"From a security perspective, speculative execution involves executing a program in possibly incorrect ways.
However, because CPUs are designed to maintain functional correctness by reverting the results of incorrect speculative executions to their prior states, these errors were previously assumed to be safe."
(:ghost: - §1)
---
### Broken security boundary
"Vulnerable out-of-order CPUs allow an unprivileged process to load data from a privileged (kernel or physical) address into a temporary CPU register."
(:icecream: - §1)
---
### Microarchitectural side-channel
"We observed that out-of-order memory lookups influence the cache, which in turn can be detected through the cache side channel.
As a result, an attacker can dump the entire kernel memory by reading privileged memory in an out-of-order execution stream, and transmit the data from this elusive state via a microarchitectural covert channel (e.g., Flush+Reload) to the outside world."
(:icecream: - §1)
---
### Flush+Reload
https://www.usenix.org/system/files/conference/usenixsecurity14/sec14-paper-yarom.pdf
---
### Observing cache side-channels
"The attacker begins by evicting a cache line from the cache that is shared with the victim. After the victim executes for a while, the attacker measures the time it takes to perform a memory read at the address corresponding to the evicted cache line.
If the victim accessed the monitored cache line, the data will be in the cache, and the access will be fast. Otherwise, if the victim has not accessed the line, the read will be slow.
Hence, by measuring the access time, the attacker learns whether the victim accessed the monitored cache line between the eviction and probing steps."
(:ghost: §2.E)
---
### Attack methodology

(:icecream: Fig. 5)
---
### Blast radius
"Speculative execution on modern CPUs can run several hundred instructions ahead.
The limit is typically governed by the size of the reorder buffer in the CPU.
For instance, on the Haswell microarchitecture, the reorder buffer has sufficient space for 192 micro-ops."
(:ghost: §2.B)
---
### Meltdown specific
- User-space to kernel-space attack
- Arbitrary read in kernel memory, useful in an exploit-chain for Local Privilege Escalation (LPE)
- Targets pagefault trapping
- Bypasses virtual memory protection (MMU)
- Can be mitigated by tweaking kernel design
- Affects mostly Intel (but others too)
---
### Page mapping
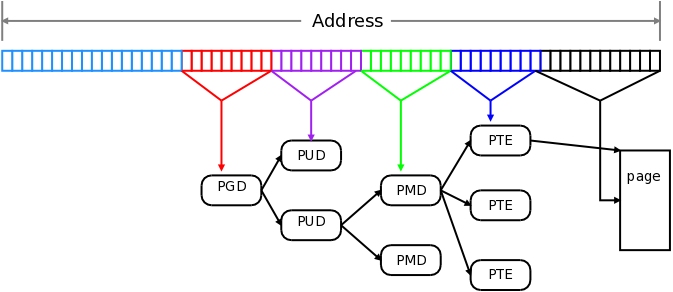
([LWN](https://lwn.net/Articles/717293/))
---
### Kernel mapping (pre-:icecream:)

(:icecream: Fig. 1)
---
### Kernel mapping (post-:icecream:)

([Wikipedia](https://en.wikipedia.org/wiki/Kernel_page-table_isolation))
---
### Spectre specific
- User-space, in-process attack
- Arbitrary read out of sandbox boundary
- Remote secret leakage
- Targets branch-prediction engine
- Bypasses software isolation
- Requires mitigations in compilers/libraries/application
- Affects anything with speculative execution (Intel, AMD, ARMv8)
- Smaller ARM processors are in-order (e.g. RPi ones)
- Many variants (at least 5 CVEs so far)
---
### Spectre variants
1. bounds check bypass store (CVE-2017-5753) and bounds check bypass store (CVE-2018-3693)
2. branch target injection (CVE-2017-5715)
3. using speculative reads of inaccessible data (CVE-2017-5754)
4. using speculative reads of inaccessible data (CVE-2018-3640)
5. speculative bypassing of stores by younger loads despite the presence of a dependency (CVE-2018-3639)
---
### :icecream: mitigation: KPTI
* https://www.kernel.org/doc/html/latest/x86/pti.html
* TLDR: split process and kernel page-mappings.
---
### :ghost: mitigation: retpoline
* Compiler hardening
* https://llvm.org/docs/SpeculativeLoadHardening.html
---
### More micro-architectural issues
* MDS - https://www.kernel.org/doc/html/latest/admin-guide/hw-vuln/mds.html
* L1TF - https://www.kernel.org/doc/html/latest/admin-guide/hw-vuln/l1tf.html
* TAA - https://www.kernel.org/doc/html/latest/admin-guide/hw-vuln/tsx_async_abort.html
---
### In Linux world
* https://coreos.com/os/docs/latest/disabling-smt.html
{"metaMigratedAt":"2023-06-15T08:39:48.644Z","metaMigratedFrom":"YAML","title":"Meltdown and Spectre","breaks":true,"contributors":"[{\"id\":\"c25a92c3-a0fc-44fd-b609-68a77e03625f\",\"add\":7896,\"del\":2647}]"}