# Reading Responses *(Set 1)*
- Checklist for a [good reading response](https://reagle.org/joseph/zwiki/Teaching/Best_Practices/Learning/Writing_Responses.html) of 250-350 words
- Begin with a punchy start.
- Mention specific ideas, details, and examples from the text and earlier classes.
- Offer something novel that you can offer towards class participation.
- Check for writing for clarity, concision, cohesion, and coherence.
- Send to professor with **“hackmd”** in the subject, with URL of this page and markdown of today’s response.
<br/>
## 5 out of 5 Responses
### Jan 19 Fri - How the web works
At first glance, the inner workings behind the web may seem daunting and outright unperceivable. But this is not the case. Looking under the hood reveals a rather simple call-and-response system dotted with intermediaries. As mentioned in Hartley Brody’s (2013) blog article: *How HTTPS Secures Connections*, “there are a lot of different organizations who ferry a request along.” From your computer, another device on your network, your routers and switches, all of the way through the network chain to the server, there are several parties that pass along your traffic. The message passed through the parties is called HTTP. As defined in Mozilla article, *How the web works*, “Hypertext Transfer Protocol is an application protocol that defines a language for clients and servers to speak to each other.”
This language in itself is completely unencrypted and relatively easy to snoop in on. This led to the need to develop different security protocols (namely HTTPS) to protect web traffic. As computing power has gotten cheaper and faster, more and more websites have switched to using an encrypted protocol to help protect user data through the often long pipelines to go from client to server, and back again. This is especially important for secure information, such as banking and user credentials. Nowadays, it is free and increasingly ubiquitous. Some sites, however, opt against using it. For a long time, **even W3C’s** [website](https://www.w3.org/blog/2022/redirecting-to-https-on-www-w3-org/) did not automatically redirect to HTTPS, even when most websites at the time had been doing so. Other sites, such as China’s [Xinhua News Agency](http://xinhuanet.com/) remain as unprotected. In a [global context](https://www.comparitech.com/blog/vpn-privacy/cybersecurity-by-country/), the adoption of HTTPS varies significantly, revealing intriguing patterns and considerations. While major websites in technologically advanced regions tend to prioritize user security by widely adopting encrypted protocols, disparities begin to arise when examining websites in different industries or geographic regions.
>I would like to better understand how websites collect and analyze user data, the ethical considerations involved, and the impacts of it on user privacy.
### Jan 26 Fri - Learning
It all finally makes sense. After **years** of trying to overcome diagnosis after diagnosis, my memory can actually be helped. I have always tested quite poorly for my ability to memorize things and have tried just about every trick in the book to do it. However, changing my learning style altogether was not one I had considered.
The book “make it stick” by Brown et al. does a remarkable job suggesting strategies and improvements to efficiently encode and retrieve material from memory. Not only does the book do a great job of offering strategies, but they also follow their own advice in a meta context, utilizing the strategies with different overlying anecdotes (such as Matt’s flight troubles), effectively helping the reader remember what they had learned about learning.
This is what was the most helpful to me in realizing how to improve my learning. I would read something telling me that low-stakes quizzing is important, and then Matt’s anecdote would reiterate it in a real-life way, showing that it can explored outside of text.
Some of the other methods of retrieval that the author suggests practicing are:
1. Low-stakes quizzing
2. Self-testing
3. Spacing out practice
4. Interleaving practice
5. Solving problems before being given the solution
6. Breaking down the underlying concepts
The idea of low-stakes quizzing popped out at me immediately in two lights. First and foremost was the occurrence of it in this class, during the first day of class as a review of the syllabus. This was an excellent exercise and it proved its efficacy to me immediately as the answers I was less sure of, I was more inclined to go back to the syllabus and find the answers that I missed (effectively using spacing).
The other instance where this came to light in multiple dimensions was with the use of [Quizlet](https://quizlet.com). While I haven’t used it this year, I definitely have dedicated heavy utilization in past semesters. The flashcard function (with ability to randomize) helps me learn the majority of the content. However, when it feels like I am repeating things that may not be encoded any further, I switch into using either the learn mode (which changes its questioning method based on how successful you are at recalling the word), and the quiz mode (which offers a quiz in the style you choose).
### Feb 02 Fri - Cooperation
Cooperation is a vital principle for the well-being of humanity, as emphasized by Martin Nowak in his book "Super Cooperators.” Nowak delves into game theory, starting with a breakdown of one of the most famous game theory examples: The Prisoner’s Dilemma. Devised in 1950 by Merrill Flood and Melvin Dresher, the dilemma highlights a scenario where you and an accomplice are both captured by police, and you need to both give the optimal response to get the shortest punishment. Humans are inherently selfish and always seek the best outcome for themselves (as evidenced by the Prisoner’s Dilemma and the Punish & Perish experiments).
The conclusion the Prisoner’s Dilemma reaches reflects the same: “No matter what the other person does, it is better for you to defect.” But this is the selfish conclusion that both parties will come to. Thinking rationally and both thinking what the other would do, would actually yield both choosing to remain silent and enjoy the second-best outcome.
At the end of the day, humans will cooperate when they have a **clear** reason to do so. The tit-for-tat mentality stood out to me the most when it comes to an online presence from a negative lens. For instance, in a social media thread, if one person makes a negative comment about someone's opinion, the other person may respond with a counter-insult or escalate the conflict by attacking the original commenter's character. This cycle of tit-for-tat can continue, with each party retaliating in a similar manner, leading to an increasingly hostile and unproductive exchange. This type of behavior is often counterproductive, as it contributes to a toxic online environment and hinders meaningful communication.
[Reagle's analysis](https://readingthecomments.mitpress.mit.edu/pub/dtys4tyk/release/2#gossip), exploring the origins of online platforms and the role of gossip, adds another layer to the discussion. It introduces the concept of Dunbar's number, suggesting that as online communities grow, the cognitive limit of around 150 relationships comes into play. This limit poses challenges to the quality of online interactions, mirroring the individual-centered approach discussed by Nowak in the context of the Prisoner's Dilemma.
### Feb 06 Tue - Social networks
According to [The Oracle of Bacon](https://oracleofbacon.org/). Elon Musk has a Bacon number of 2 – with the only degree of separation throughout all movies being Johnny Depp. While it may not sound all that impressive that two actors have that close of a connection with each other, how about the consideration that you could be just a few connections away from Elon Musk or Paul Rudd? This is more likely than not, according to research from Rheingold in his 2012 book **Net Smart: How to Thrive Online**, pointing to most social connections having an average path length between nodes of about 5 or 6 relationships.
To define the total value of a network, different network pioneers have attempted to model how the growth of a network increases its value. David Sarnoff (president of RCA who founded NBC) observed that the value of his network increased “in *direct proportion* to the size of the network.” While this was accurate for networks consisting of a few central nodes broadcasting to many marginal nodes, it was inaccurate and underestimating when compared to the concept brought forth by Robert Metcalfe. His law suggests that the value of a network increases in proportion to the number of users on the network squared. For group-forming networks, Reed’s Law says the value of the network isn’t just determined by the number of nodes it can connect to “but also by the potential number of groups it can communicate with” (p. 199).
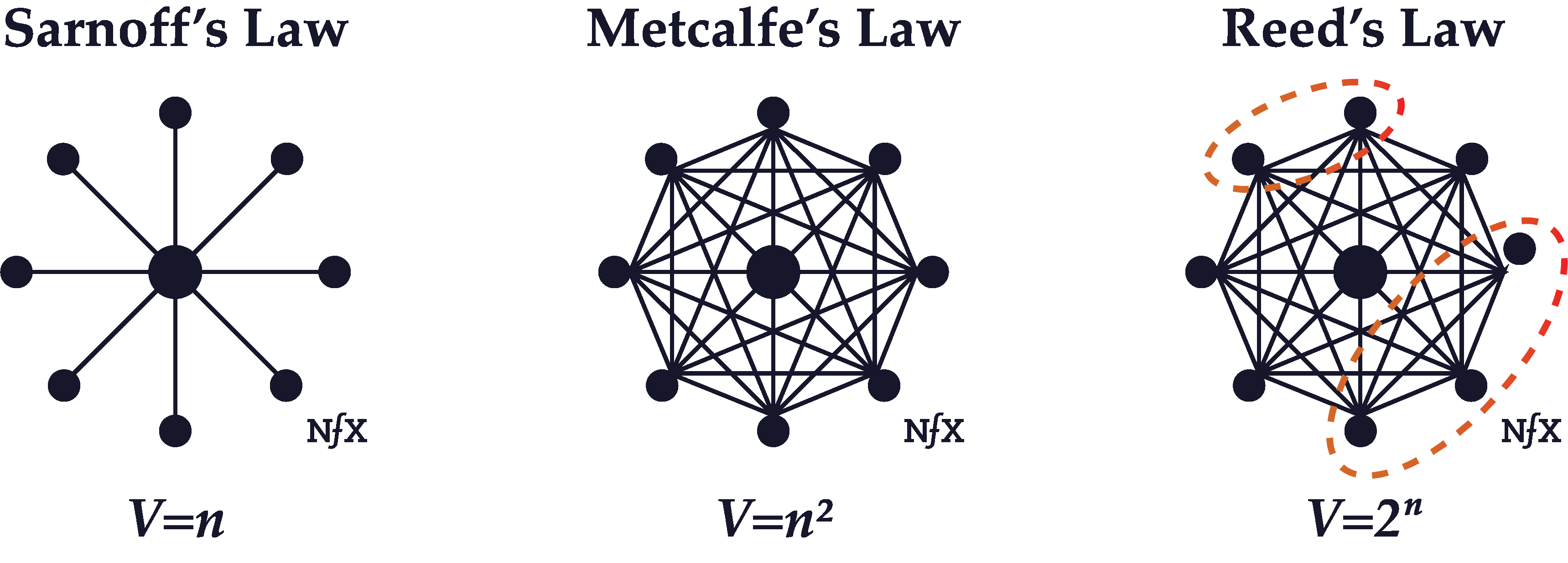
> [Source for above image](https://guides.co/g/the-network-effects-bible/121725)
The chapter also makes the crucial argument that social networks eliminate distance relationships. Even when we relocate, we may maintain connections with the people in a community even after we leave through social media (p. 206). This allows us the opportunity to grow our social networks over time. This sounds great, except for its potential tie back to the concept of “filter bubbles.” Companies like Facebook can easily mediate the ways you see data or the amount of nodes in your network. As found by Granovetter, “highly clustered networks do not exhibit the small-world feature; you need the random distant connections beyond your closest networks” (p. 206).
### Feb 16 Fri - The darknet
As defined by [The European Monitoring Centre for Drugs and Drug Addiction]( https://www.emcdda.europa.eu/publications/posters/2018/darknet-markets-ecosystem_en), the darknet is an online marketplace that aims to “provide a largely anonymous platform for trading in a range of illicit goods and services.” The biggest and most well-known site on the darknet was the Silk Road. Created by Ross Ulbricht, the Silk Road aimed to provide a professional approach to the sale of illicit substances/services. As a way of maintaining anonymity and avoiding credit card companies cooperating with the government, the Silk Road relied on Tor to obfuscate their identity and Bitcoin as the major currency. And this worked very well and enabled a ton of business. According to Kozhipatt, “the website had over 100,000 users and had…tens of millions of dollars exchanged, every day.”
Tor’s presence as a high anonymity option has been bolstered by its great concept and even more impressive network of volunteers. The 6,000 potential relays within the network that could each act as a guard node, middle node, or exit node, make it extremely difficult to track or intercept information (aside from the exit node). Each step is encrypted from one node to another, making intercepting data useless.
Bitcoin operates in mostly the same way. Securing a complicated network of nodes bolsters the security of transactions, just as having more potential nodes in Tor decreases the possibility of interception. Having a public ledger makes it so you cannot fraudulently create more Bitcoin, and the fundamental rules behind the currency are also set and not changeable.
However, as pointed out in the [Time Magazine](https://time.com/6239364/crypto-criminals-andy-greenberg/) article, this vast public ledger is the very thing that leads to Bitcoin being a public and not at all an anonymous financial solution. Because every transaction has to be thoroughly verified, it is relatively easy to watch transactions flow through the network.
<br/>
This prompts my wondering:
>Is there a solution to cracking down on the types of crimes that Tor/Bitcoin enabled in the Silk Road without damaging the benefits of both tools that are used for non-illicit activities?