# [MetaCTF](https://ctftime.org/event/1476)
###### tags: `ctf` `2021`
{%hackmd theme-dark %}
[TL;DR Just jump to the conclusion at last part if you think this write-up is too lengthy](https://hackmd.io/gT5hyOIJQhWGqQ_nBQw0TQ?view#FeedBack-for-this-semester-ASU-CSE-466)
# Cryptography
## `Thnks fr th Pwds`
### Description:
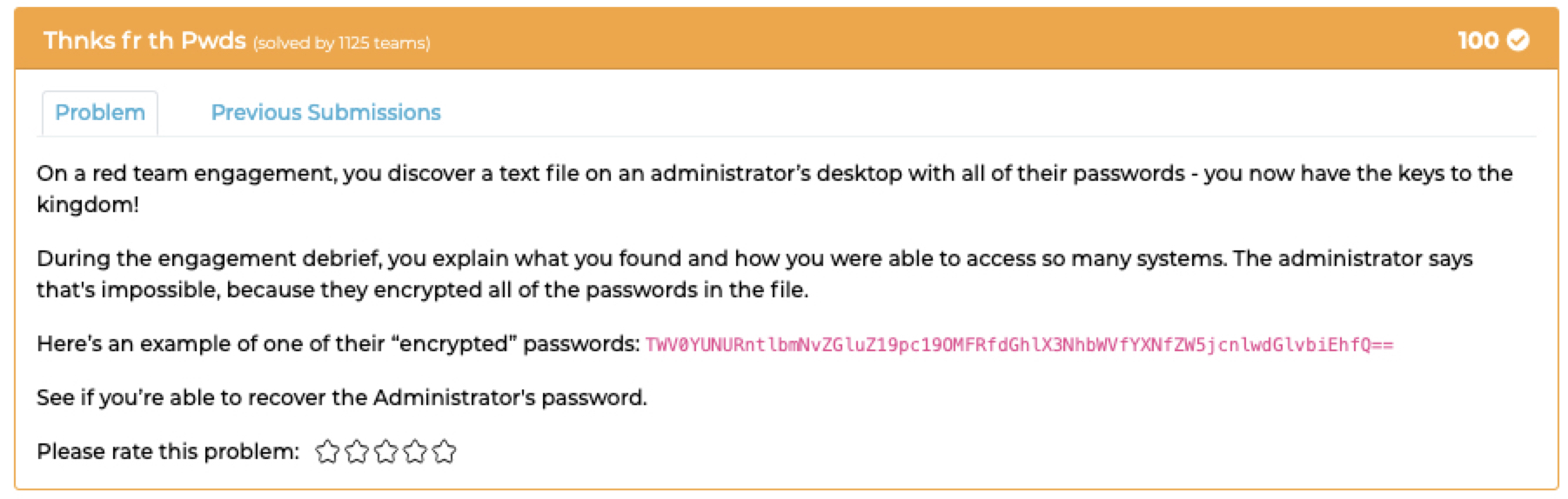
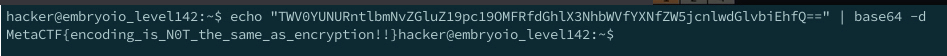
- It seems to be encoded as base64, so I decoded it in the following command
- `echo "TWV0YUNURntlbmNvZGluZ19pc19OMFRfdGhlX3NhbWVfYXNfZW5jcnlwdGlvbiEhfQ==" | base64 -d`
- 
### Got flag:
- `MetaCTF{encoding_is_N0T_the_same_as_encryption!!}`
## `Wrong Way on a One Way Street`
### Description:
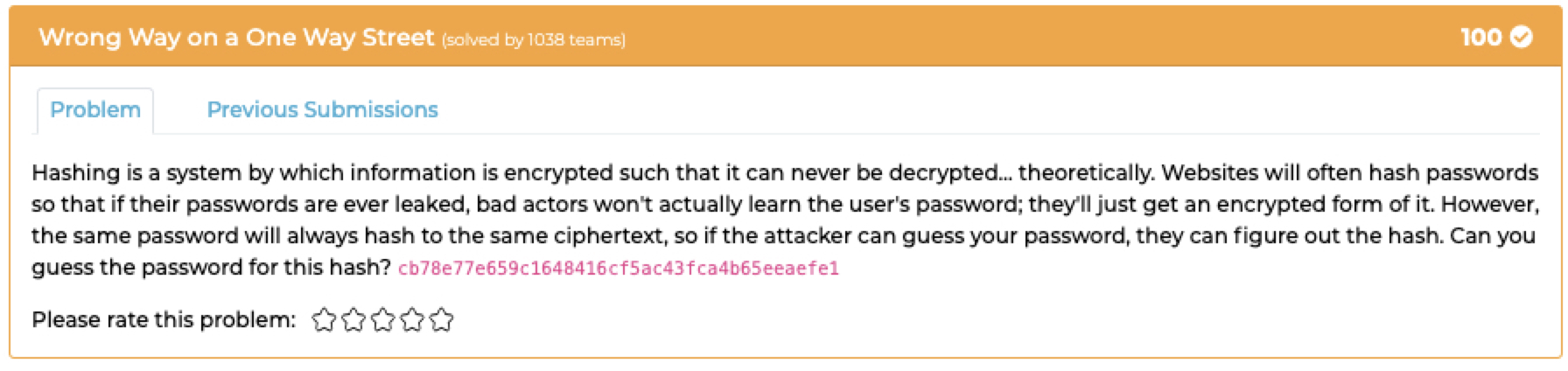
- Find the hash with online [cracking tools](https://crackstation.net/) and get:
- 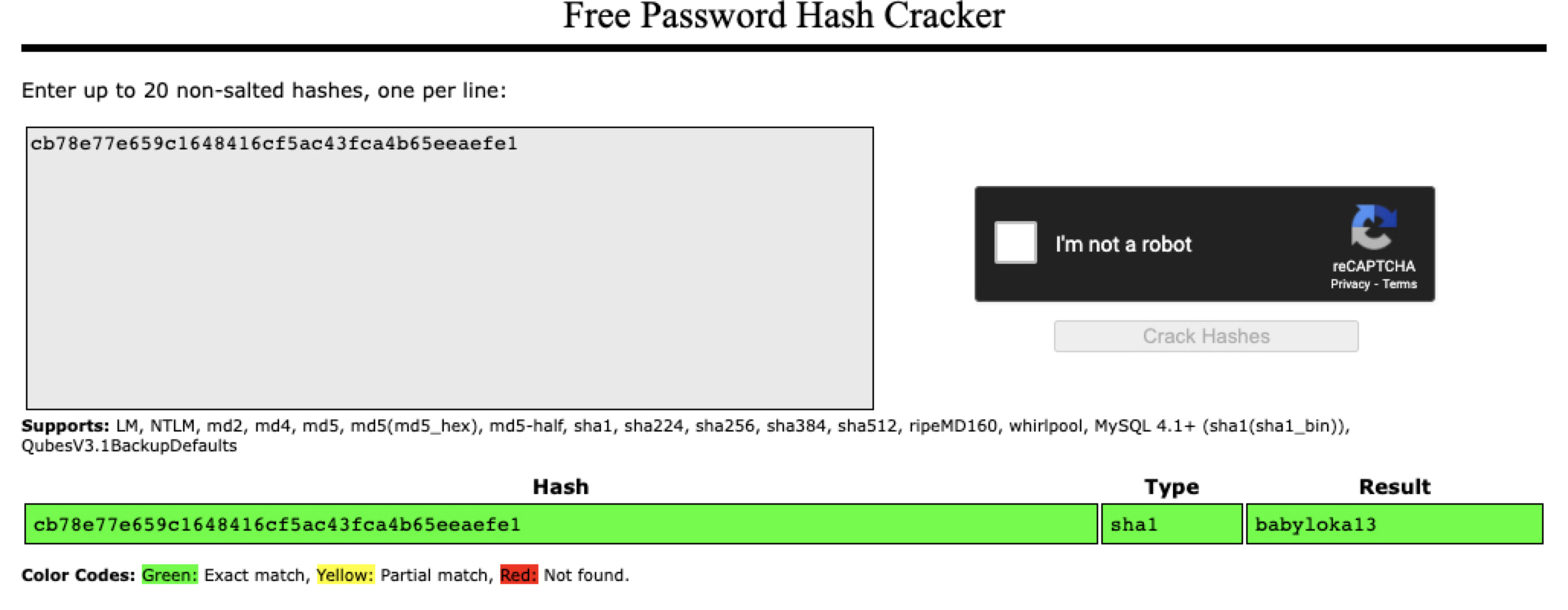
### Got flag:
- `MetaCTF{babyloka13}`
## `Size Matters`
### Description:
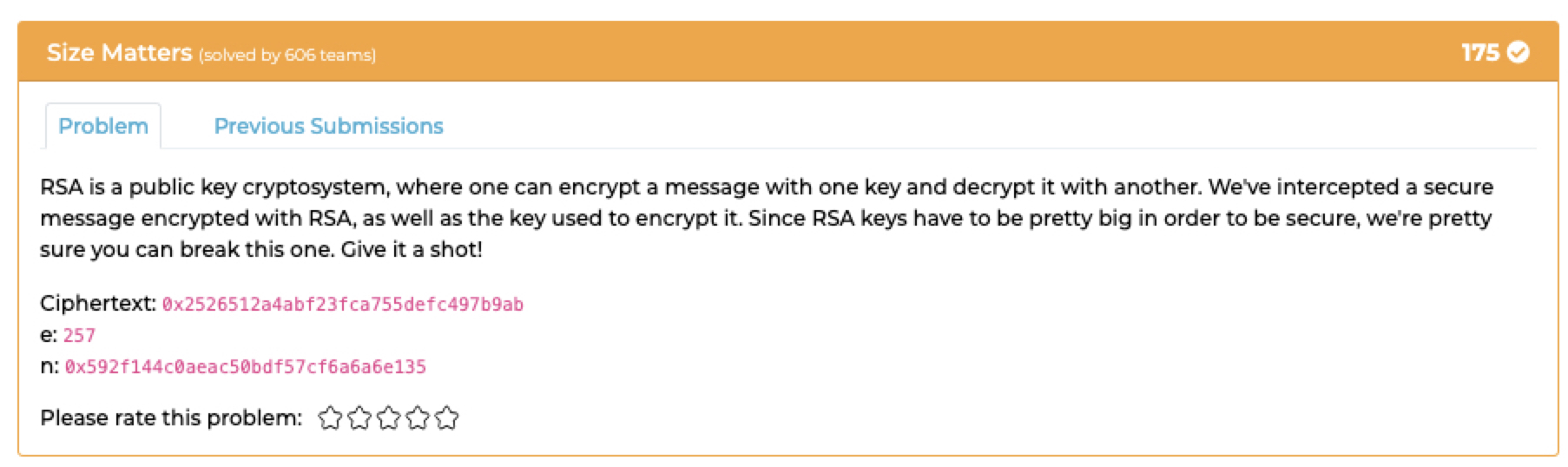
- Find the RSA with online [cracking tools](https://www.dcode.fr/rsa-cipher) and get:
- 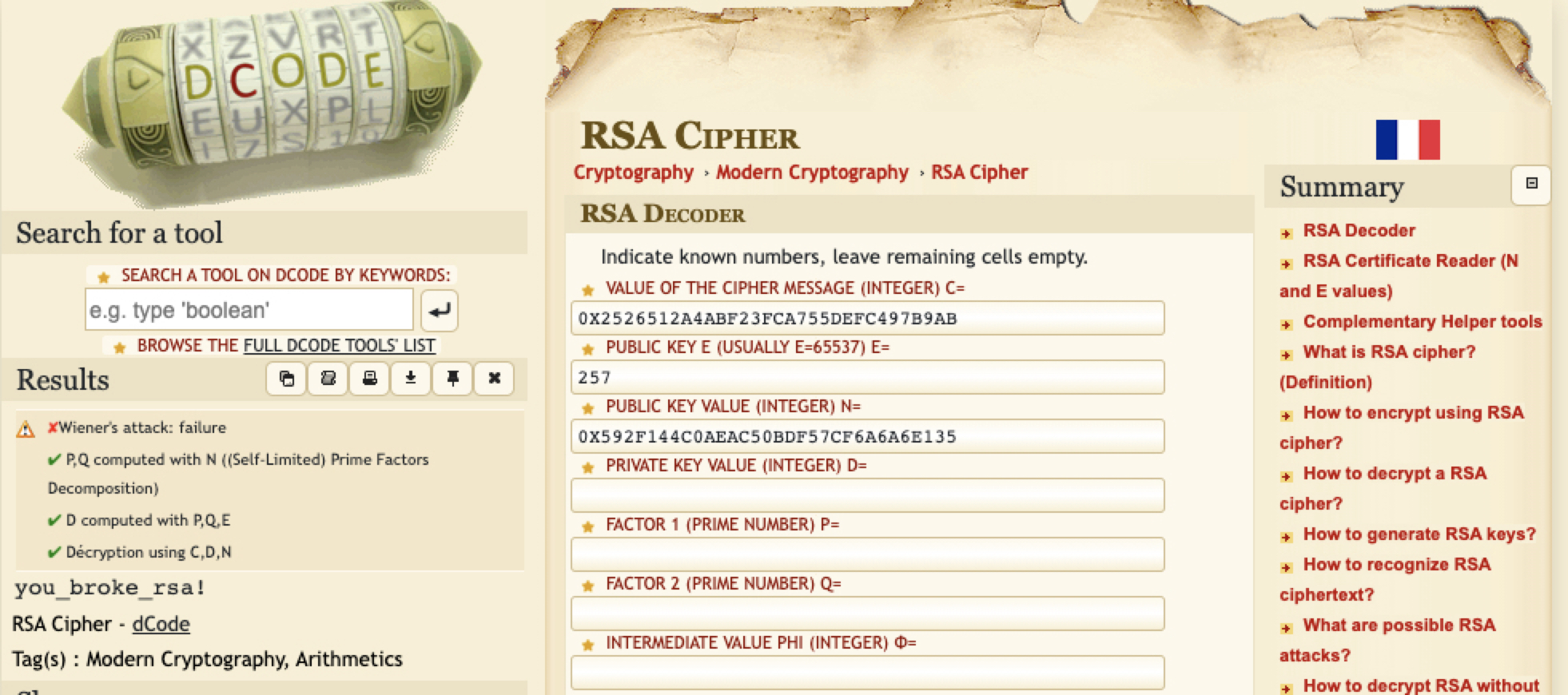
### Got flag:
- `MetaCTF{you_broke_rsa!}`
# Forensics
## `Magic in the Hex`
### Description:
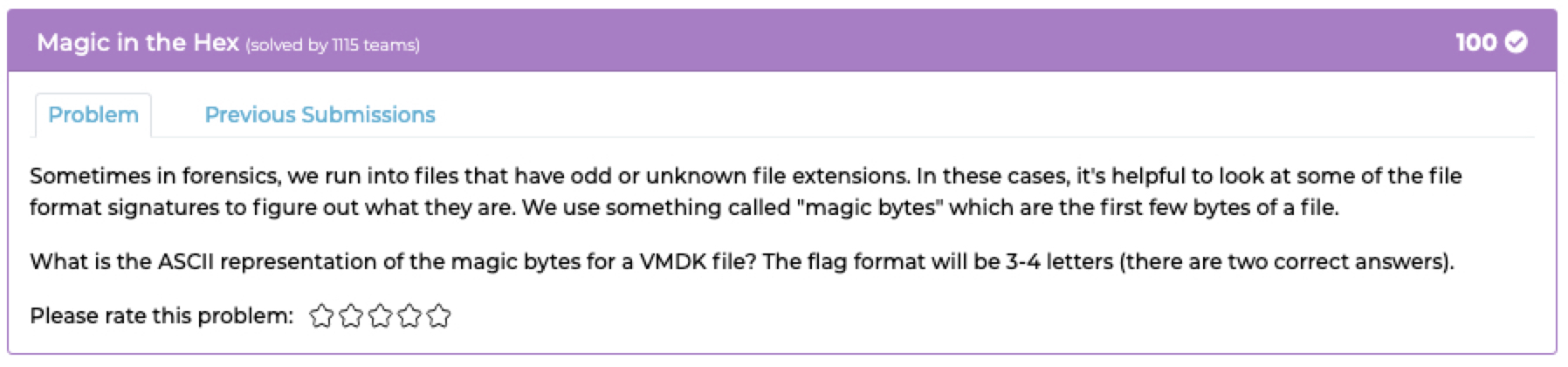
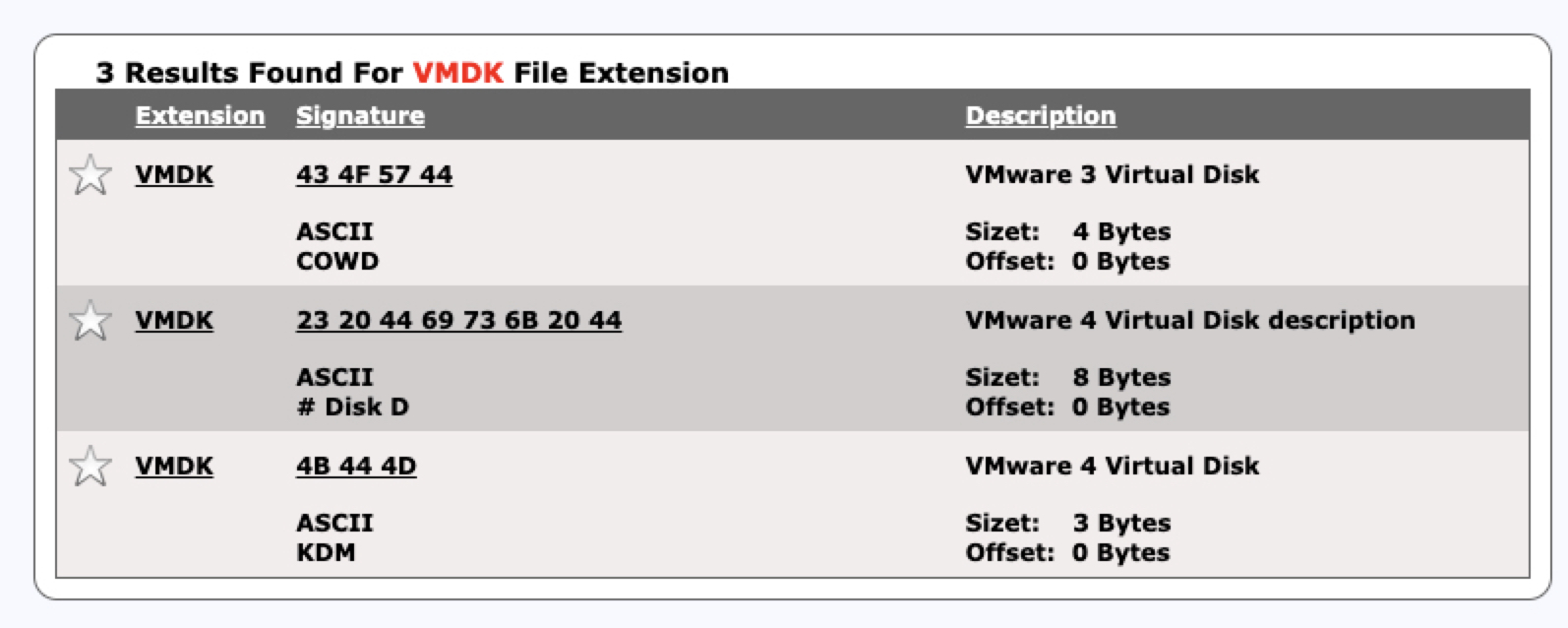
- Found the magic number of the `VMDK` file by [googling](https://filesignatures.net/index.php?page=search&search=VMDK&mode=EXT)
- 
### Got flag:
- `KDM`
## `Sharing Files and Passwords`
### Description:
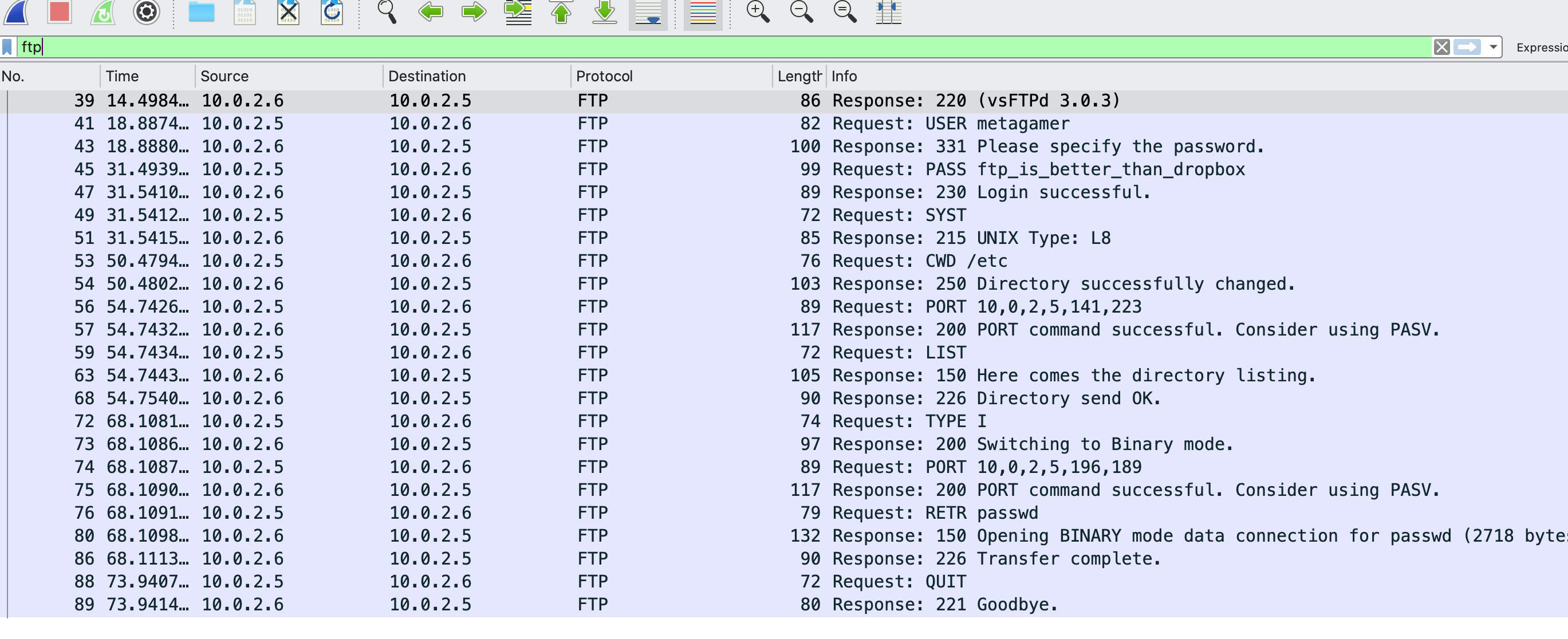
- Download the `pcap` file and filter the FTP protocol and the password revealed
- 
### Got flag:
- ` METACTF{ftp_is_better_than_dropbox}`
## `Still Believe in Magic?`
### Description:
- Got a file, and when `file magic.tar.gz`, We got:
```bash=
magic.tar.gz: gzip compressed data, last modified: Fri Dec 3 16:51:29 2021, from Unix, original size modulo 2^32 10240
```
- It seems the flag is compressed in two kinds of methods (`.tar` and `.gz`), so we have to decompress it.
- So first, I used `gzip -d magic.tar.gz` to get `magic.tar.`
- And then, I used `tar -xf magic.tar` to get `magic.`
- from `file magic`, we can know `magic: Zip archive data, at least v2.0 to extract.`
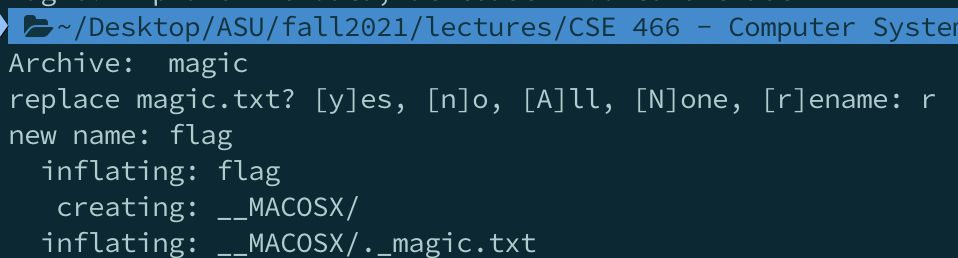
- Lastly, I used `unzip magic` to get the magic file
- 
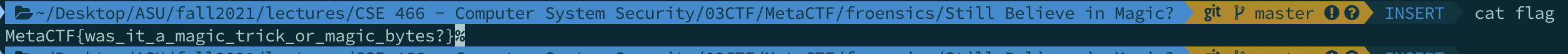
- `cat flag`
- 
### Got flag:
- `MetaCTF{was_it_a_magic_trick_or_magic_bytes?}`
### Referece
- [How to decompress files in gzip](https://help.nexcess.net/77285-other/how-to-decompress-files-in-gzip)
- [How to decompress files in tar](https://linuxize.com/post/how-to-extract-unzip-tar-gz-file/)
# Other
## `This Ain't a Scene, It's an Encryption Race`
### Description:
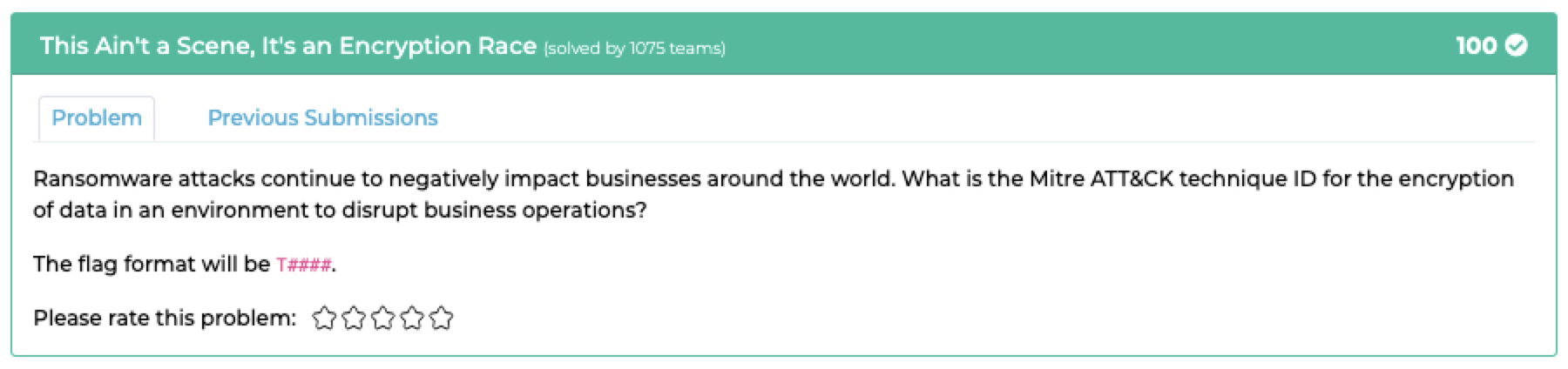
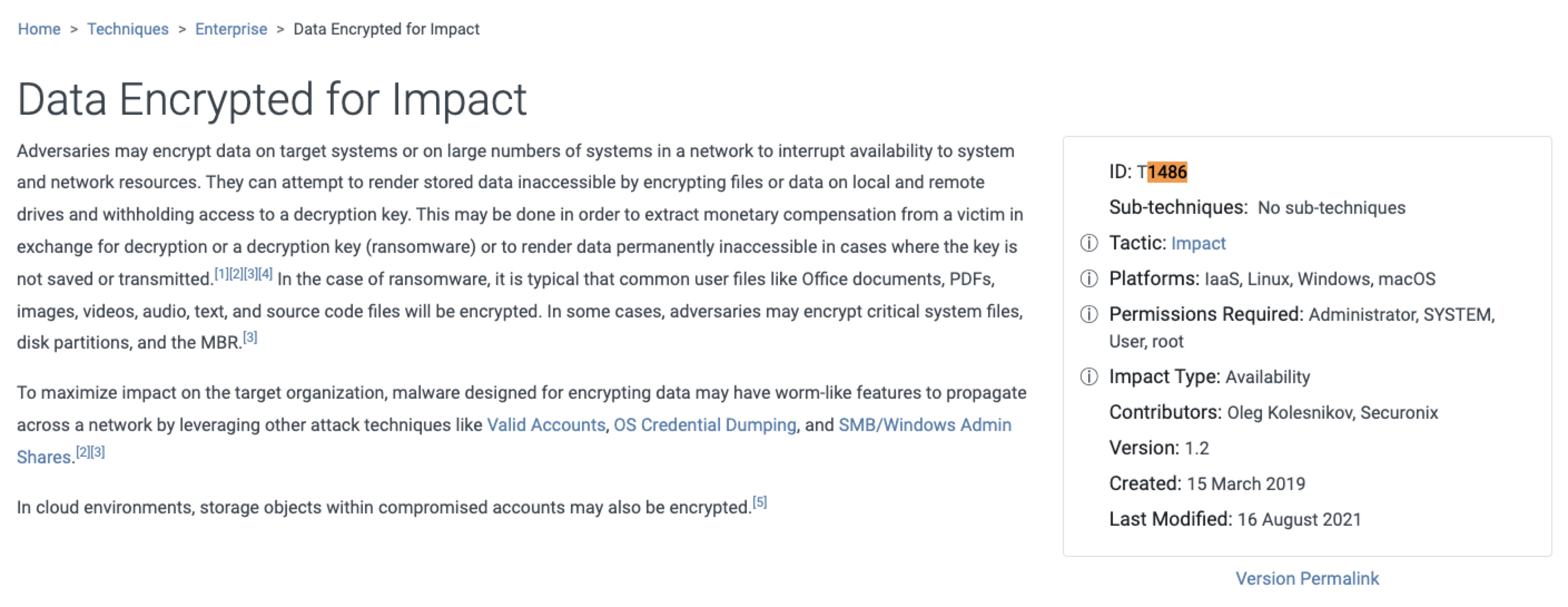
- Find the Mitre ATT&CK technique ID for the encryption of data by [googling](https://attack.mitre.org/techniques/T1486/)
- 
### Got flag:
- `T1486`
# Reconnaissance
## `Sugar, We're Goin Up`
### Description:
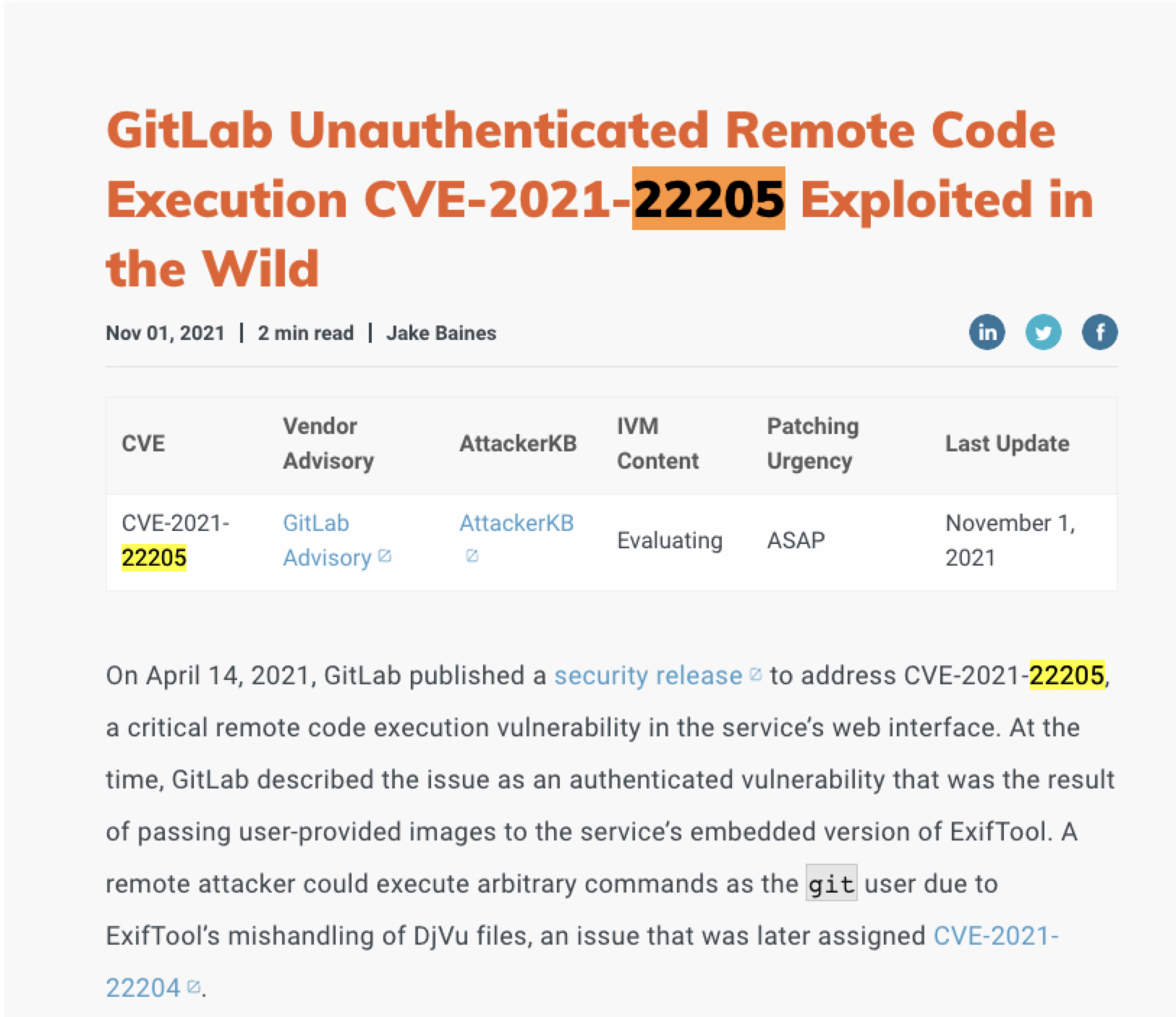
- Found that by [googling](https://www.rapid7.com/blog/post/2021/11/01/gitlab-unauthenticated-remote-code-execution-cve-2021-22205-exploited-in-the-wild/)
- 
### Got flag:
- `CVE-2021-22205`
## `The Best Laid Plans...`
### Description:
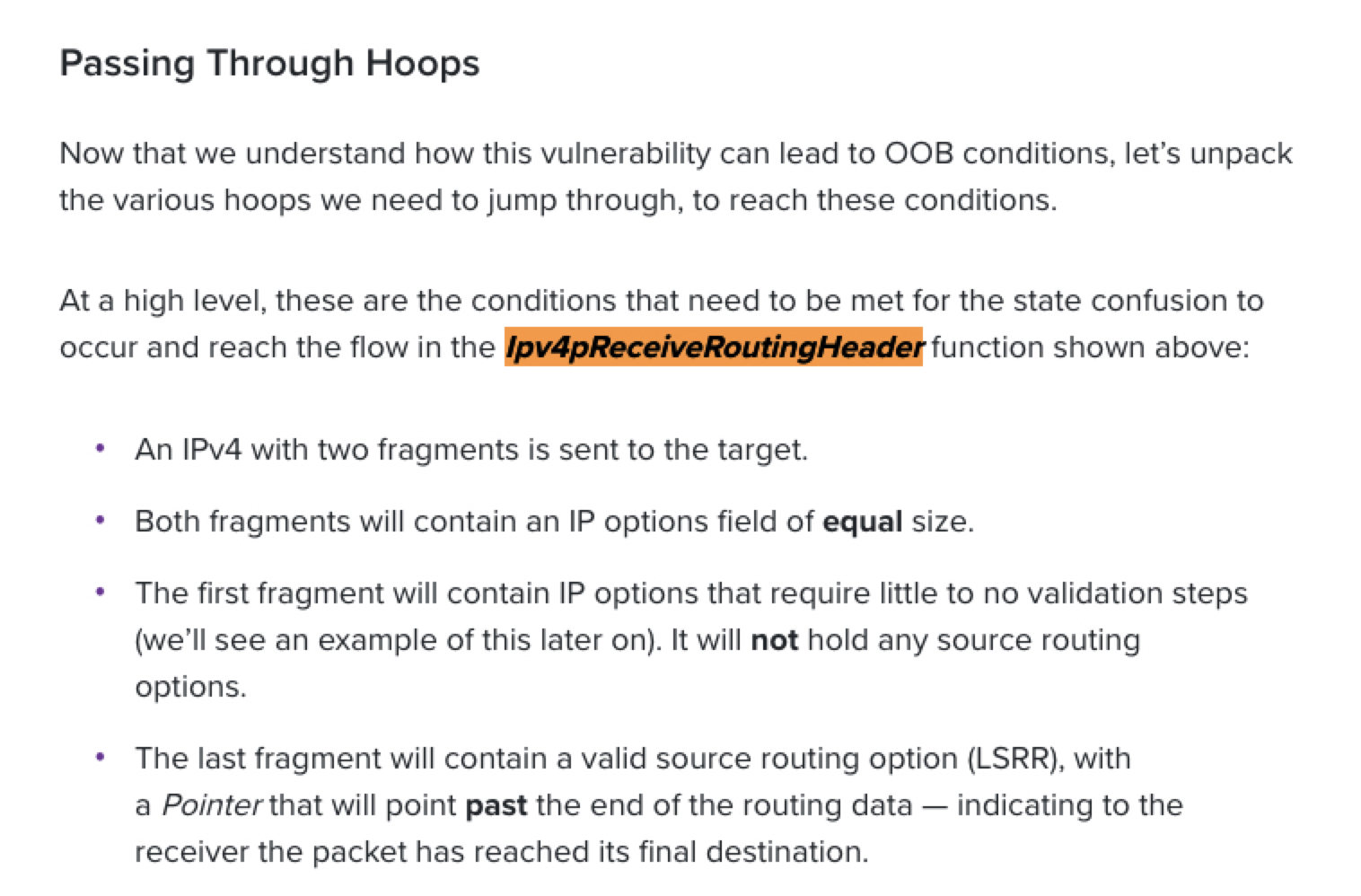
- Found that by [googling](https://www.armis.com/blog/from-urgent11-to-frag44-microsoft-patches-critical-vulnerabilities-in-windows-tcpip-stack/)
- 
### Got flag:
- ` MetaCTF{Ipv4pReceiveRoutingHeader}`
## `Who Broke the Printer This Time?`
### Description:
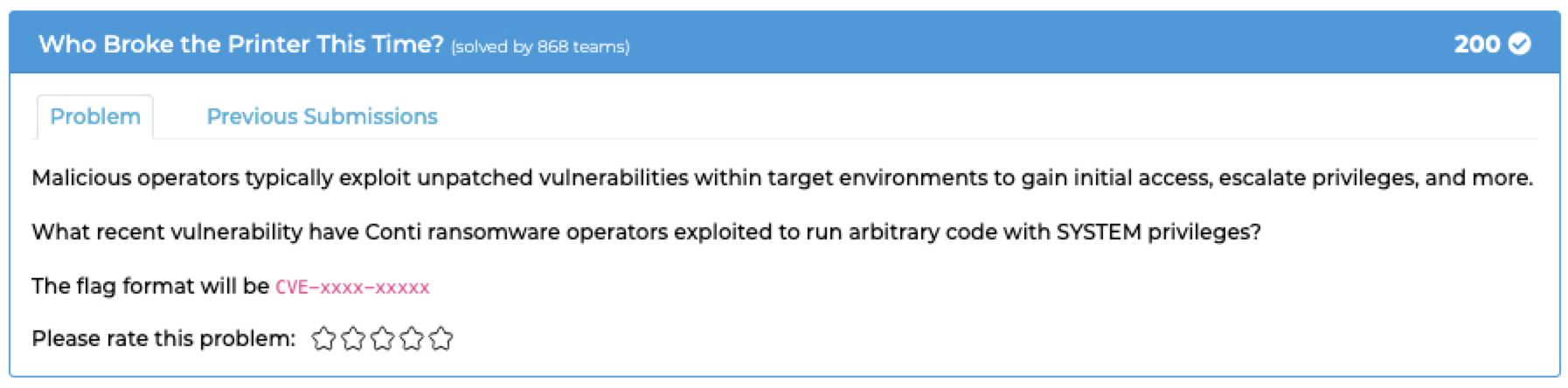
- Found that by [googling](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-34527)
- 
### Got flag:
- `CVE-2021-34527`
# Web Exploitation
## `Under Inspection`
### Description:
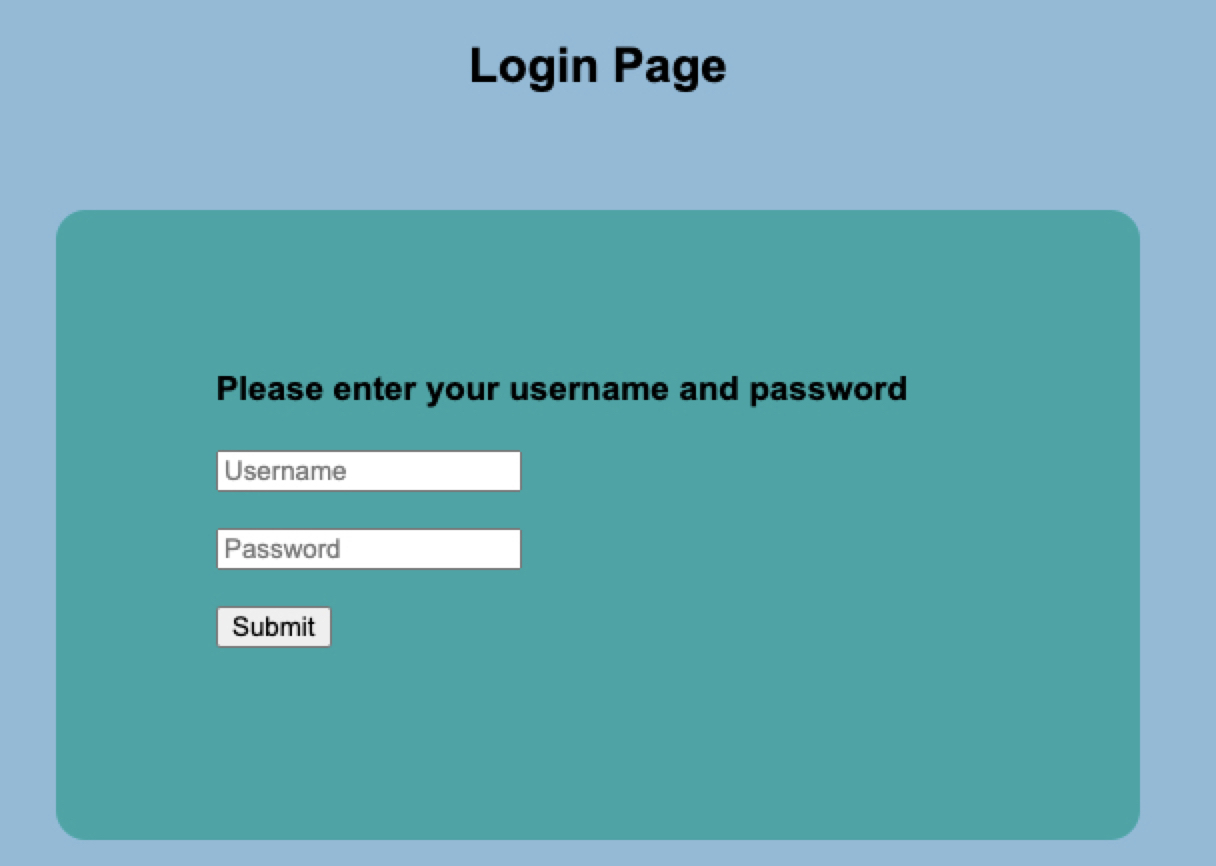
- There is an easy login-page
- 
- I try to look around the `Network` by Developer's tools and find something interesting:
- 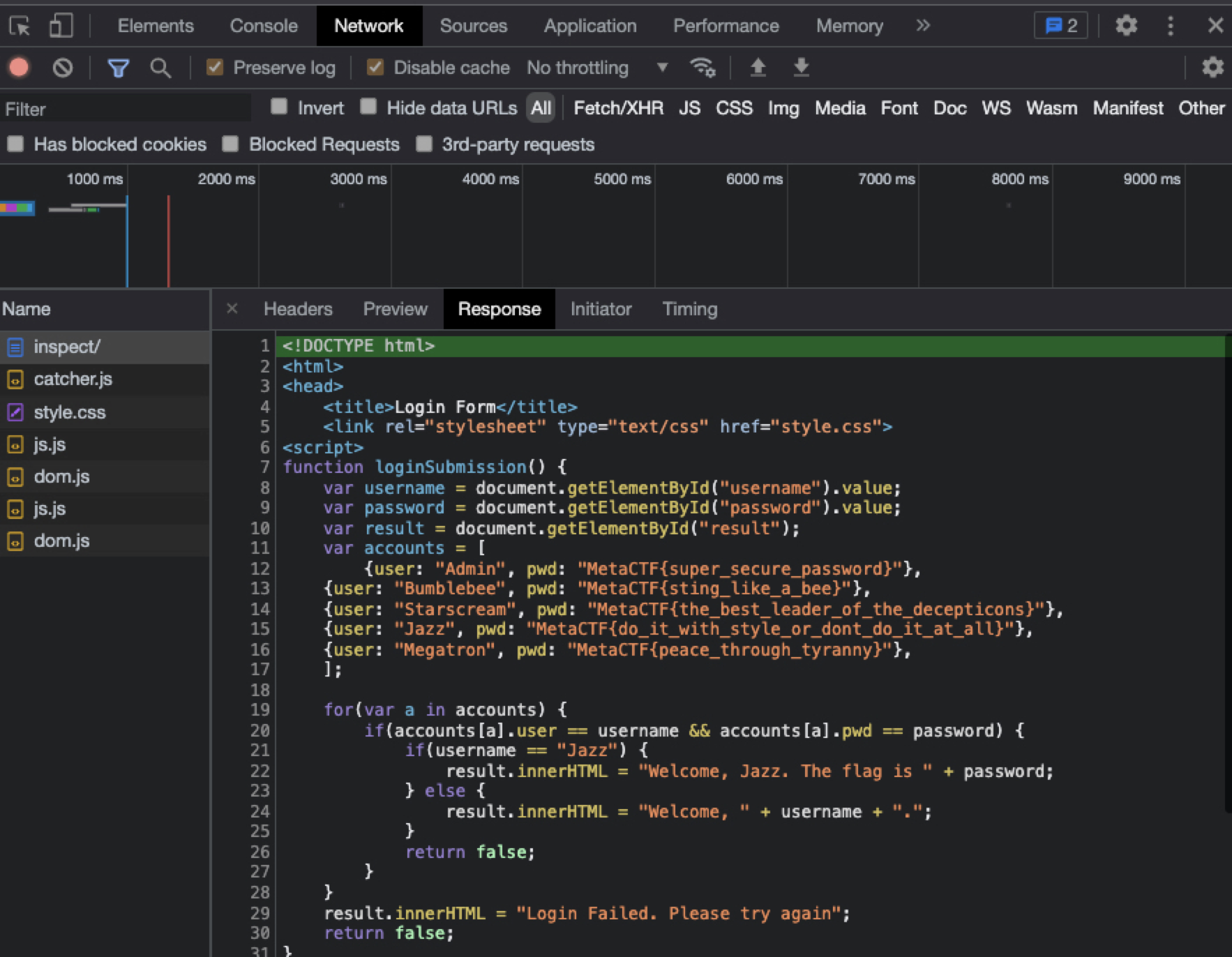
- From the code, you can tell that if `username == "Jazz"`, the flag will return, so I did.
- Actually, the password is the flag
### Got flag:
- `MetaCTF{do_it_with_style_or_dont_do_it_at_all} `
# Conclusion for this semester (ASU CSE 466)
### Fun
- Although this is the last CTF game playing with the team [`ToInfinityAndBeYANd`](https://ctftime.org/team/162814), I had a lot of fun. Thank you all for playing CTF with me this semester. Plus, thank you Yan for providing this great opportunity for us to play CTF this whole semester. Have a lot of fun. Thanks! I'll keep pushing until I get the yellow belt (even the blue belt)! LOL
### Shout out to all the teammates!
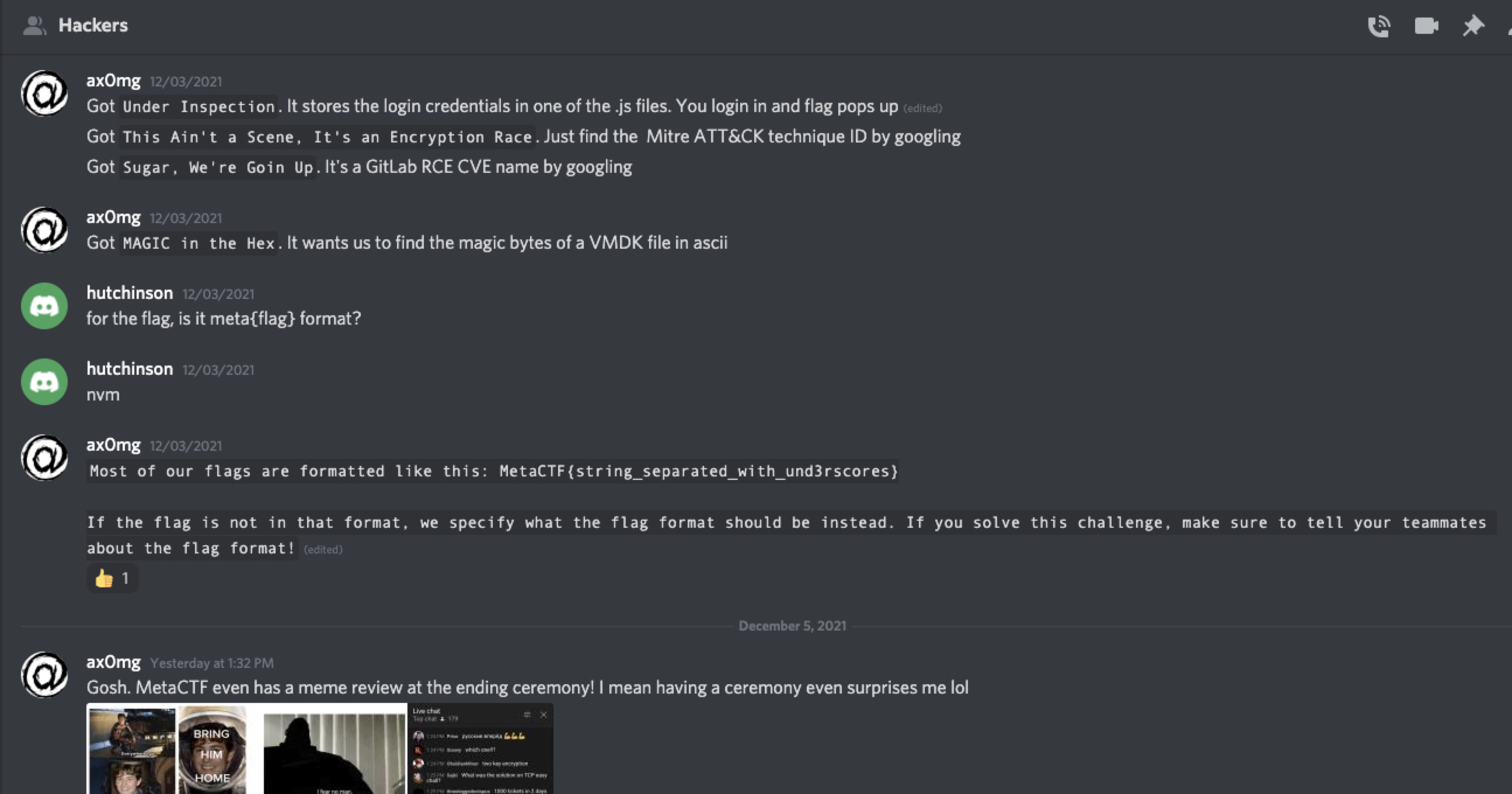
### We had a team called `Hacker` in discord
- 
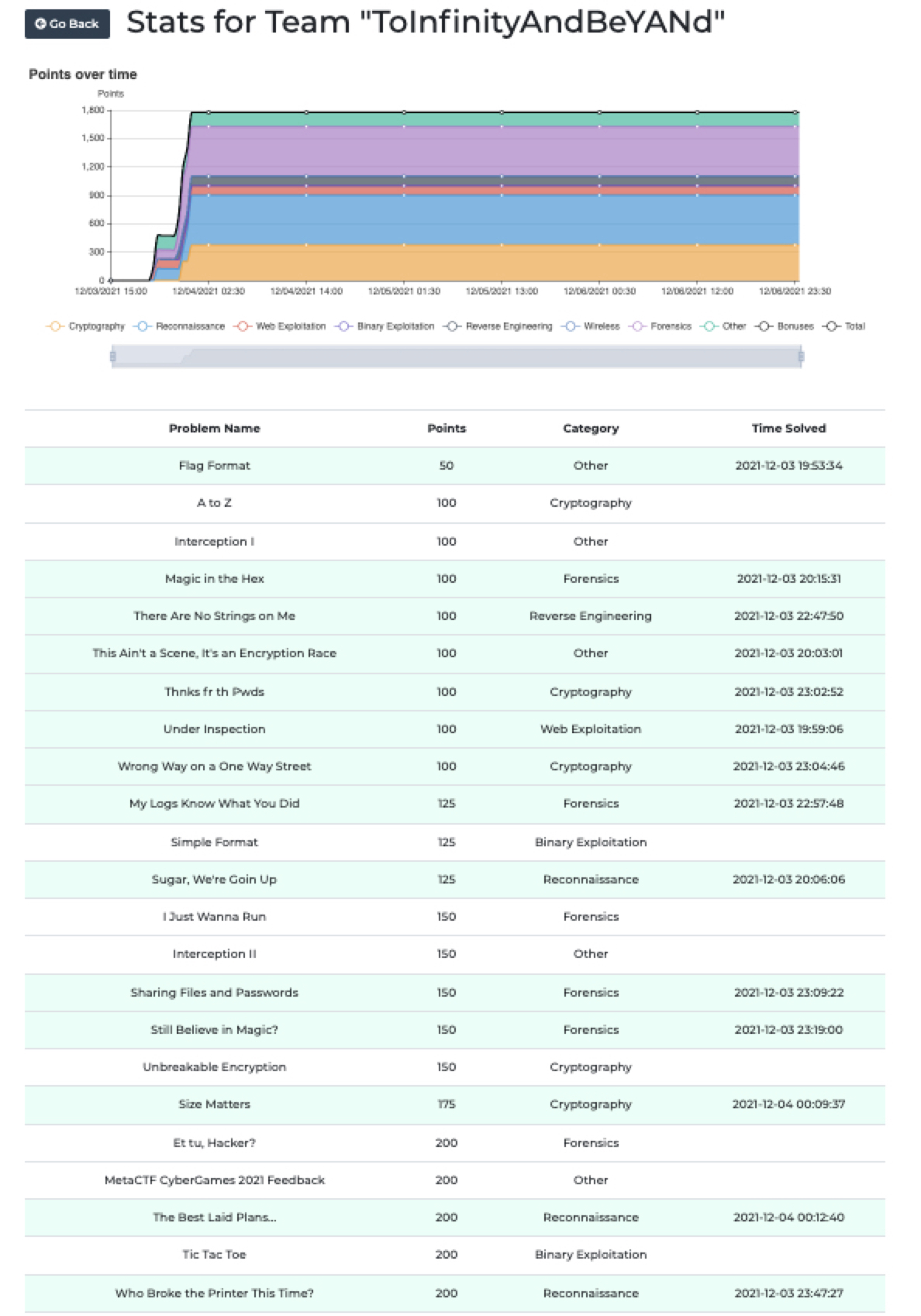
### I solved 11 challenges, quite a fun one
-