# CodeQL
<!-- Put the link to this slide here so people can follow -->
slide: https://hackmd.io/@atdog/ByfDtmZgT
---
### 身為一個研究員
應該要進入科學的時代
----
### Low-hanging fruits
規模化的撿起來
---
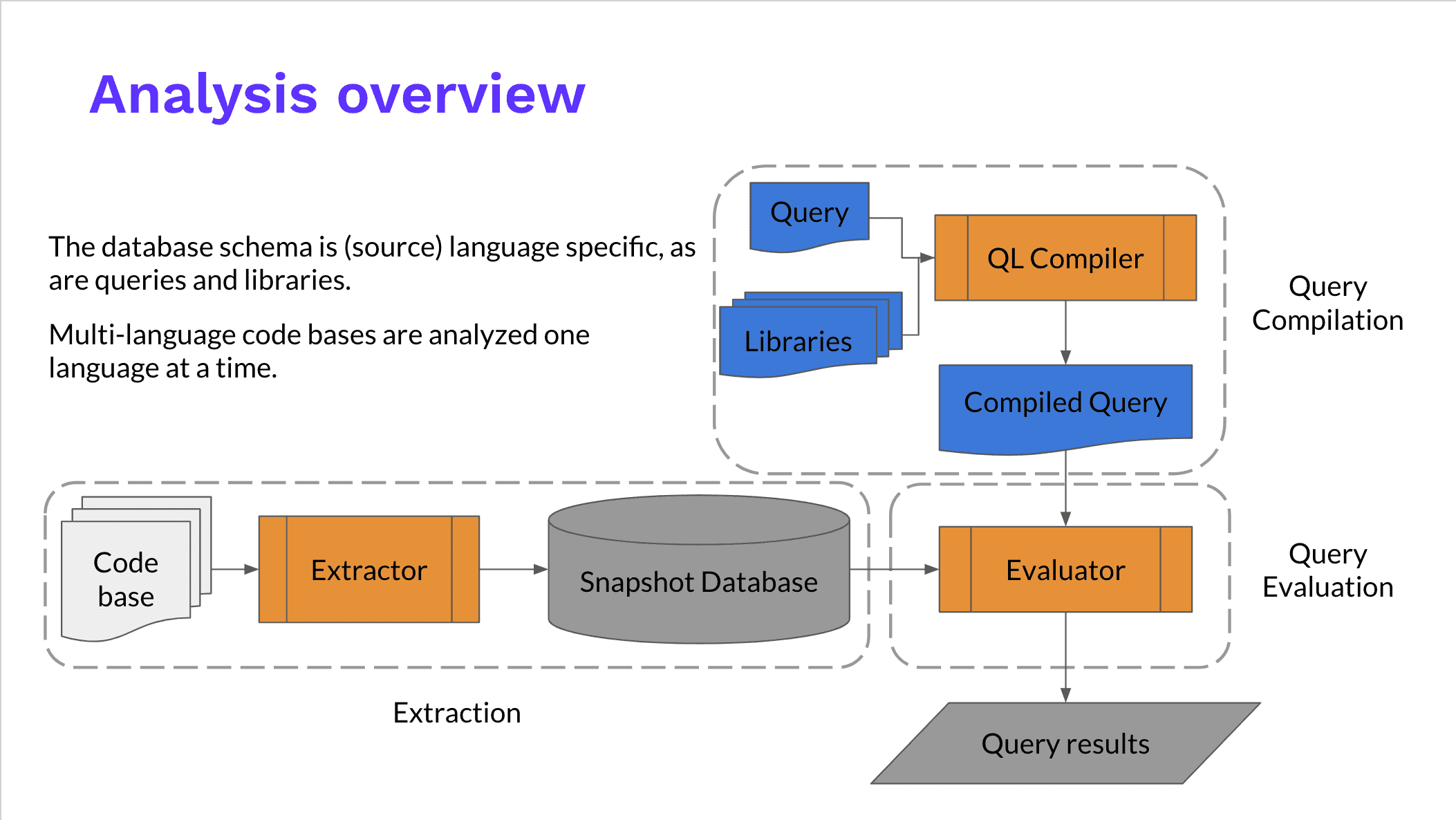
## CodeQL: Variant Analysis
<span>大致上分成兩個東西<!-- .element: class="fragment" data-fragment-index="1" --></span>
<span>Database<!-- .element: class="fragment" data-fragment-index="2" --></span>
<span>Query<!-- .element: class="fragment" data-fragment-index="3" --></span>
----
----
### Supported Language
- C/C++, C#
- Go
- Java / Kotlin
- JavaScript / TypeScript
- Python
- Ruby
- Swift
----
### Query
```
import /* ... CodeQL libraries or modules ... */
/* ... Optional, define CodeQL classes and predicates ... */
from /* ... variable declarations ... */
where /* ... logical formula ... */
select /* ... expressions ... */
```
----
### Predicate
- getAneighbor("Belgium") returns "France" and "Germany"
```java [|2-8|10]
string getANeighbor(string country) {
country = "France" and result = "Belgium"
or
country = "France" and result = "Germany"
or
country = "Germany" and result = "Austria"
or
country = "Germany" and result = "Belgium"
or
country = getANeighbor(result)
}
```
----
### Predicate
- match all subprocess.*
```bash [|2|4-5]
from
DataFlow::Node arg
where
arg = API::moduleImport("subprocess").getMember(_)
.getACall().getArg(_)
select
"test"
```
----
### Dataflow
- local
- global
----
### TaintTracking
- local
- global
```python
temp = x
y = temp + ", " + temp
```
----
### a( p ) -> os.open( p )
```python [|5|7-8|9]
cimport python
import semmle.python.dataflow.new.DataFlow
import semmle.python.ApiGraphs
from DataFlow::CallCfgNode call, DataFlow::ParameterNode p
where
call = API::moduleImport("os").getMember("open")
.getACall() and
DataFlow::localFlow(p, call.getArg(0))
select call, p
```
---
## CodeQL Bounty
- HackerOne
- Launched on 2019
- 寫 Query 換錢

----
## $500

----
一些參考
https://securitylab.github.com/codeql-wall-of-fame/
---
## Use Cases
----
### HITCON 2020: xxx
https://hitcon.org/2020/slides/Discover%20vulnerabilities%20with%20CodeQL.pdf
----
### ZDI 2022: MySQL Cluster
<style>.yellow {color: #ff8}</style>
https://www.zerodayinitiative.com/blog/2022/2/10/mindshare-when-mysql-cluster-encounters-taint-analysis
- isAdditionalTaintStep
- isSanitizer
<span>看著看又發現是<span class="yellow">大學長 Lucas </span>做的</span><!-- .element: class="fragment" data-fragment-index="1" -->
<span>永遠跟不上學長的腳步<!-- .element: class="fragment" data-fragment-index="2" --></span>
----
### ZDI 2022: MySQL Cluster Part2
https://www.zerodayinitiative.com/blog/2022/2/22/clang-checkers-and-codeql-queries-for-detecting-untrusted-pointer-derefs-and-tainted-loop-conditions
htIR
----
### Zer0Con 2023: Mac Kernel
https://github.com/0x3c3e/slides/blob/main/2023/zer0con/slides.pdf
----
#### Zyxel
{"description":"View the slide with \"Slide Mode\".","title":"CodeQL Intro","contributors":"[{\"id\":\"60628c5b-b3b3-4e28-ad05-05960eaf8407\",\"add\":5567,\"del\":2442}]"}