# Security Engineering on AWS v2.6.30
# Instructors
Heiwad Osman (heiwad@amazon.com)
[Emil Jimenez](https://www.linkedin.com/in/emiljimenez21/) (emjimen@amazon.com)
# Getting Started
1. Sign up for an account at https://aws.qwiklabs.com for access to the lab environment - Please use the same email you used in your registration profile.
2. Sign up for an account at https://online.vitalsource.com to get access to the course ebooks - You may use a personal email if you prefer. You will receive an email from no-reply@gilmore.ca with a license code you can REDEEM in VitalSource.
3. (Recommended) Get the VitalSource Bookshelf app from so you can download your ebooks.
# Agenda & Timing
Class is expected to run from 9:00AM to 5:00PM each day. Will take breaks in morning and afternoon and also plan for 1 hr lunch around 11:45/12:00
# Get Certified
[](https://aws.amazon.com/certification/certified-security-specialty/?ch=tile&tile=getstarted)
# Questions
Ask a question in the chat! We'll record the question with the answer in here.
## Day 1
### Should integration test be done before a security patch is applied?
From an AWS perspective this is under the customer's responsibility to design pipelines to mitigate the risk when applying a security patch. Your organization should have a strategy made on you should handle patching of instances.
## Day 2
### Would there a scenario where all 3 monitoring products "should" be used?
The answer is that it depends. It is recommended to use as many logging and monitoring products as possible as when we use serverless technology we don't get access to the underlying server to see what went wrong. Also, depending on the level of compliance you are looking to achieve you might have to implement all the monitoring products to maintain compliance.
## Day 3
### Can AWS Cognito work together with the existing Active Directory?
Yes! You can achieve this by using an Identity Pool with the Cognito Service
[How to set up Amazon Cognito for federated authentication](https://aws.amazon.com/blogs/security/how-to-set-up-amazon-cognito-for-federated-authentication-using-azure-ad/)
### Can Cognito manage Users outside Organization?
Cognito can't manage users that are from a Federated Identity source using an identity pool, however users that come from a Federated Identity can be used to login to the application.
### If I have web applications that run on AWS, I can use Congnito to manage web users and access?
Yes! You can use the Cognito service to manage the users identity in the application. Cognito provides a bunch of features like account take over protection, MFA, and social login to help your users get secure access to your application.
### Will Cognito allow users to register, add, remove, assign passwords?
Yes! You can manage your registered users using the Cognito service. So being able to delete users can be done by an admin. Users also have features to enable MFA and perform password resets
### Can you please share tips about free AWS?
AWS Offers some services for [free always](https://aws.amazon.com/free/?all-free-tier.sort-by=item.additionalFields.SortRank&all-free-tier.sort-order=asc&awsf.Free%20Tier%20Types=tier%23always-free&awsf.Free%20Tier%20Categories=*all), while other services are offered for [free for 12 months](https://aws.amazon.com/free/?all-free-tier.sort-by=item.additionalFields.SortRank&all-free-tier.sort-order=asc&awsf.Free%20Tier%20Types=tier%2312monthsfree&awsf.Free%20Tier%20Categories=*all), while others are just offered as a [free trial](https://aws.amazon.com/free/?all-free-tier.sort-by=item.additionalFields.SortRank&all-free-tier.sort-order=asc&awsf.Free%20Tier%20Types=tier%23trial&awsf.Free%20Tier%20Categories=*all). Take a look a the different categories of free tier services as well as their limits to stay with-in the free tier usage
# Resources
Links and information to material covered in the course such as services, documentation, and other relevant materials will be shared here.
## Day 1
### Topics Covered
* [Security on AWS](#Module-1-Security-on-AWS)
* [Identifying Entry Points on AWS](#Module-2-Identifing-Entry-Points-on-AWS)
* [Security Considerations: Web Applications](#Module-3-Security-Considerations-Web-Application-Environments)
* [Application Security](#Module-4-Application-Security)
* [Data Security](#Module-5-Data-Security)
### Module 1: Security on AWS
* [AWS Config](https://aws.amazon.com/config/) is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources.
* [AWS CloudTrail](https://aws.amazon.com/cloudtrail/) monitors and records account activity across your AWS infrastructure, giving you control over storage, analysis, and remediation actions.
* [AWS IAM](https://aws.amazon.com/iam/) provides fine-grained access control across all of AWS.
* [AWS Cloudformation](https://aws.amazon.com/cloudformation/) lets you model, provision, and manage AWS and third-party resources by treating infrastructure as code.
* [AWS Shared Responsibility Model](https://aws.amazon.com/compliance/shared-responsibility-model/) highlights the responsibility of you as an AWS Customer and the responsibility of AWS from a security perspective.

* [AWS Cloud Adoption Framework](https://aws.amazon.com/professional-services/CAF/) leverages AWS experience and best practices to help you digitally transform and accelerate your business outcomes through innovative use of AWS
### Module 2: Identifing Entry Points on AWS
* [AWS Security Best Practices](https://docs.aws.amazon.com/IAM/latest/UserGuide/best-practices.html) use these recommendations to help secure access to your AWS resources
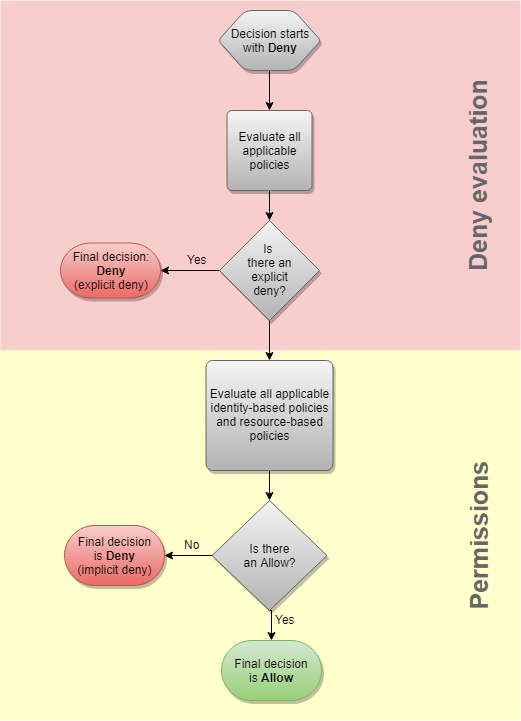
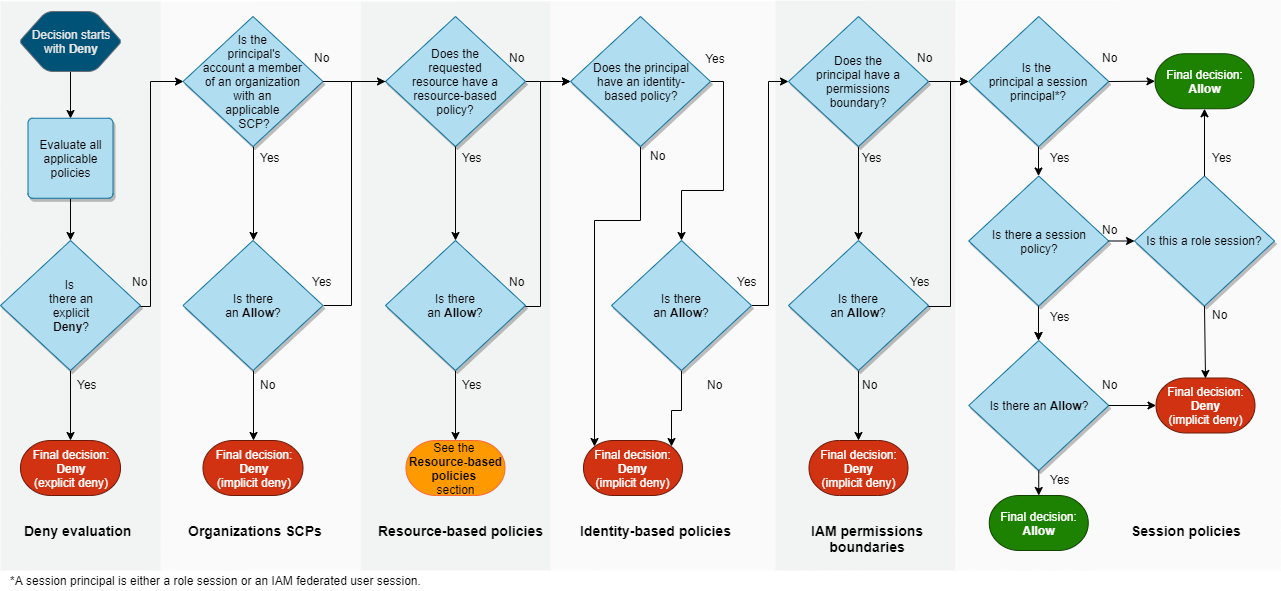
* [IAM Policy Evaluation](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html)
Simplified Diagram
Complex Diagram
* [AWS Security Token Service](https://docs.aws.amazon.com/STS/latest/APIReference/welcome.html) is a web service that enables you to request temporary, limited-privilege credentials for AWS Identity and Access Management (IAM) users or for users you authenticate (federated users).
* [IAM JSON policy reference](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies.html) contains detailed syntax, descriptions, and examples of the elements, variables, and evaluation logic of JSON policies in IAM
### Module 3: Security Considerations: Web Application Environments
* [AWS Trusted Advisor](https://aws.amazon.com/premiumsupport/technology/trusted-advisor/) provides recommendations that help you follow AWS best practices.

* [AWS IQ](https://iq.aws.amazon.com/) allows you to complete projects faster with AWS Certified freelancers and consulting firms. Pay directly through AWS only when work is complete and you are satisfied.
### Module 4: Application Security
* [EC2 Key Pairs](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-key-pairs.html) is a set of security credentials that you use to prove your identity when connecting to an Amazon EC2 instance
* [Retrieving instance metadata](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-data-retrieval.html) This can be helpful when you're writing scripts to run from your instance
* [AWS OpsWorks](https://aws.amazon.com/opsworks/) is a configuration management service that provides managed instances of Chef and Puppet
* [AWS Image Builder](https://aws.amazon.com/image-builder/) simplifies the building, testing, and deployment of Virtual Machine and container images for use on AWS or on-premises

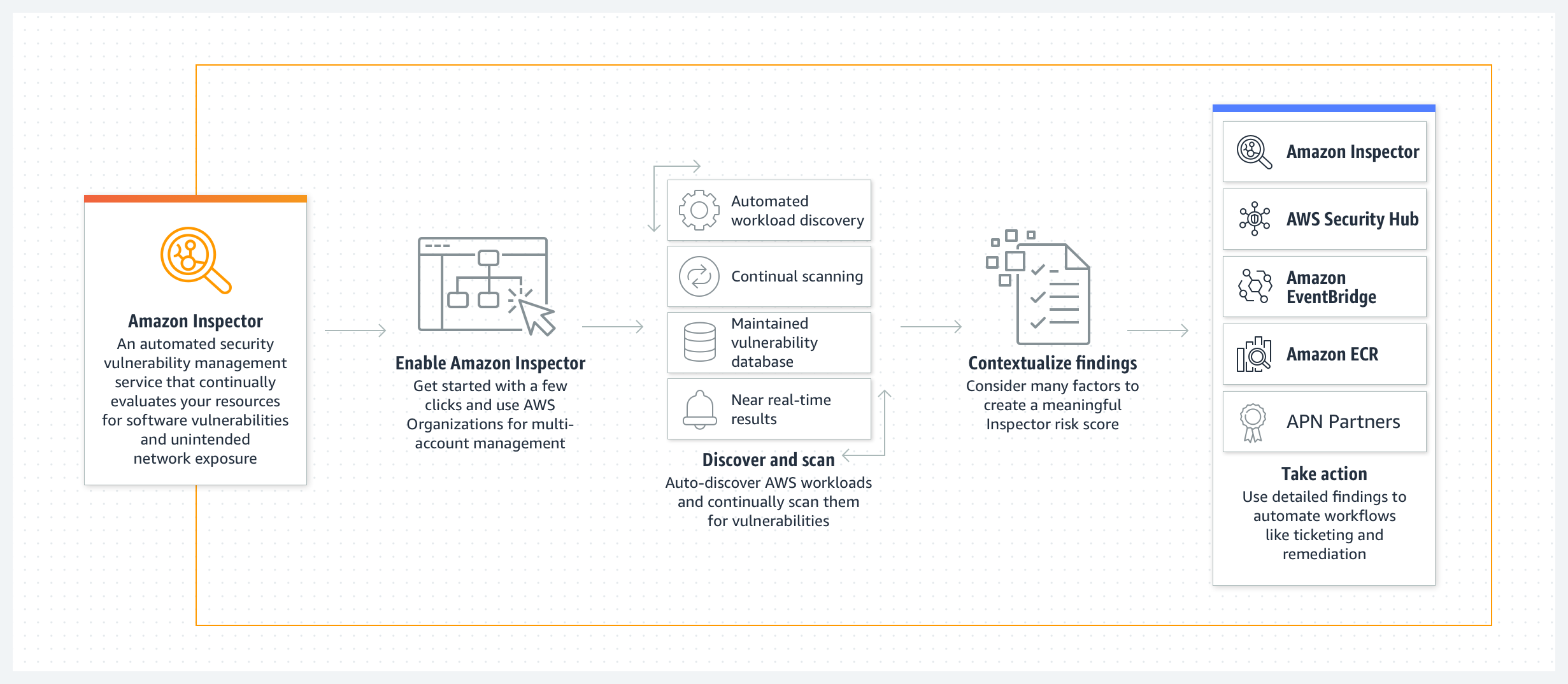
* [Amazon Inspector](https://aws.amazon.com/inspector/) is an automated vulnerability management service that continually scans AWS workloads for software vulnerabilities and unintended network exposure
* [AWS Systems Manager](https://aws.amazon.com/systems-manager/) is a secure end-to-end management solution for hybrid cloud environments

### Module 5: Data Security
* [Amazon S3: Server Side Encryption](https://docs.aws.amazon.com/AmazonS3/latest/userguide/bucket-encryption.html) you can set the default encryption behavior for an S3 bucket so that all new objects are encrypted when they are stored in the bucket
* [Amazon S3: Version Enabled Buckets](https://docs.aws.amazon.com/AmazonS3/latest/userguide/Versioning.html) is a feature to preserve, retrieve, and restore every version of every object stored in your buckets
* [Amazon S3: Object Lock](https://docs.aws.amazon.com/AmazonS3/latest/userguide/object-lock.html) is a feature that can help prevent objects from being deleted or overwritten for a fixed amount of time or indefinitely
* [Amazon S3: Replication](https://docs.aws.amazon.com/AmazonS3/latest/userguide/replication.html) enables automatic, asynchronous copying of objects across Amazon S3 buckets
* [Consistent Point-in-time restore for Amazon S3 buckets](https://aws.amazon.com/blogs/storage/consistent-point-in-time-restore-for-amazon-s3-buckets/)

* [Amazon S3: Pre-signed URLS](https://docs.aws.amazon.com/AmazonS3/latest/userguide/ShareObjectPreSignedURL.html) allows you to generate presigned URLs are valid only for the specified duration which allows an object in a private bucket to be accessed over the internet
* [Encrypting RDS Resources](https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/Overview.Encryption.html) enables you to encrypt your DB instances using AES-256 encryption to encrypt your data on the server that hosts your Amazon RDS DB instances
* [AWS Key Management Service](https://aws.amazon.com/kms/) makes it easy for you to create and manage cryptographic keys and control their use across a wide range of AWS services and in your applications
* [Amazon S3: Vault Locks](https://docs.aws.amazon.com/amazonglacier/latest/dev/vault-lock.html) allows you to easily deploy and enforce compliance controls for individual S3 Glacier vaults with a vault lock policy
## Day 2
### Topics Covered
* [Securing Network Communications](#Module-6-Securing-Network-Communications)
* [Monitoring and Collecting Logs on AWS](#Module-7-Monitoring-and-Collecting-Logs-on-AWS)
* [Processing Logs on AWS](#Module-8-Processing-Logs-on-AWS)
* [Hybrid Environments](#Module-9-Security-Considerations-Hybrid-Environments)
* [Out-of-Region Protection](#Module-10-Out-Of-Region-Protection)
### Module 6: Securing Network Communications
* [NAT Gateway](https://docs.aws.amazon.com/vpc/latest/userguide/vpc-nat-gateway.html) allow instances in a private subnet initiate a connection to services outside your VPC, but external services cannot initiate a connection with those instances
* [Security Groups](https://docs.aws.amazon.com/vpc/latest/userguide/VPC_SecurityGroups.html) acts as a virtual firewall, controlling the traffic that is allowed to reach and leave the resources that it is associated with. For example, after you associate a security group with an EC2 instance, it controls the inbound and outbound traffic for the instance
* [Network Access Control Lists](https://docs.aws.amazon.com/vpc/latest/userguide/vpc-network-acls.html) are an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets
* [Traffic Mirroring](https://docs.aws.amazon.com/vpc/latest/mirroring/what-is-traffic-mirroring.html) a feature that you can use to copy network traffic from an elastic network interface of Amazon EC2 instances
* [EC2 Auto Clean Room Forensics](https://github.com/awslabs/aws-security-automation/blob/master/EC2%20Auto%20Clean%20Room%20Forensics/README.md)

* [VPC Peering](https://docs.aws.amazon.com/vpc/latest/peering/what-is-vpc-peering.html) is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses
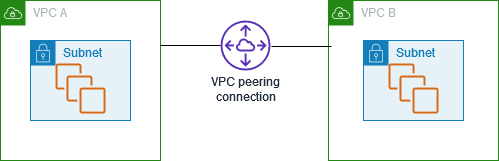
* [VPC Endpoint](https://docs.aws.amazon.com/vpc/latest/privatelink/vpc-endpoints.html) enables connections between a virtual private cloud (VPC) and supported services, without requiring that you use an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection
* [Interface Endpoint](https://docs.aws.amazon.com/vpc/latest/privatelink/vpce-interface.html) allows you to connect to services powered by AWS PrivateLink
* [Gateway Endpoints](https://docs.aws.amazon.com/vpc/latest/privatelink/vpce-gateway.html) provide reliable connectivity to Amazon S3 and DynamoDB without requiring an internet gateway or a NAT device for your VPC
* [Elastic Load Balancing](https://aws.amazon.com/elasticloadbalancing/) automatically distributes incoming application traffic across multiple targets and virtual appliances in one or more Availability Zones (AZs)
* [AWS Certificate Manager](https://aws.amazon.com/certificate-manager/) is a service that lets you easily provision, manage, and deploy public and private Secure Sockets Layer/Transport Layer Security (SSL/TLS) certificates for use with AWS services and your internal connected resources

### Module 7: Monitoring and Collecting Logs on AWS
* [Amazon Cloudwatch](https://aws.amazon.com/cloudwatch/) is a monitoring and observability service built for DevOps engineers, developers, site reliability engineers (SREs), IT managers, and product owners

* [AWS Config](https://aws.amazon.com/config/) is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources
* [How to stream AWS Cloudwatch logs to Splunk](https://www.splunk.com/en_us/blog/tips-and-tricks/how-to-easily-stream-aws-cloudwatch-logs-to-splunk.html)

* [Elastic Load Balancing: Access Logs](https://docs.aws.amazon.com/elasticloadbalancing/latest/application/load-balancer-access-logs.html) provides access logs that capture detailed information about requests sent to your load balancer
### Module 8: Processing Logs on AWS
* [Amazon Kinesis](https://aws.amazon.com/kinesis/) makes it easy to collect, process, and analyze real-time, streaming data so you can get timely insights and react quickly to new information
* [Amazon Kinesis Data Streams](https://aws.amazon.com/kinesis/data-streams/?nc=sn&loc=2&dn=2) is an extract, transform, and load (ETL) service that reliably captures, transforms, and delivers streaming data to data lakes, data stores, and analytics services
* [Amazon Kinesis Data Firehose](https://aws.amazon.com/kinesis/data-firehose/?nc=sn&loc=2&dn=3) is an extract, transform, and load (ETL) service that reliably captures, transforms, and delivers streaming data to data lakes, data stores, and analytics services
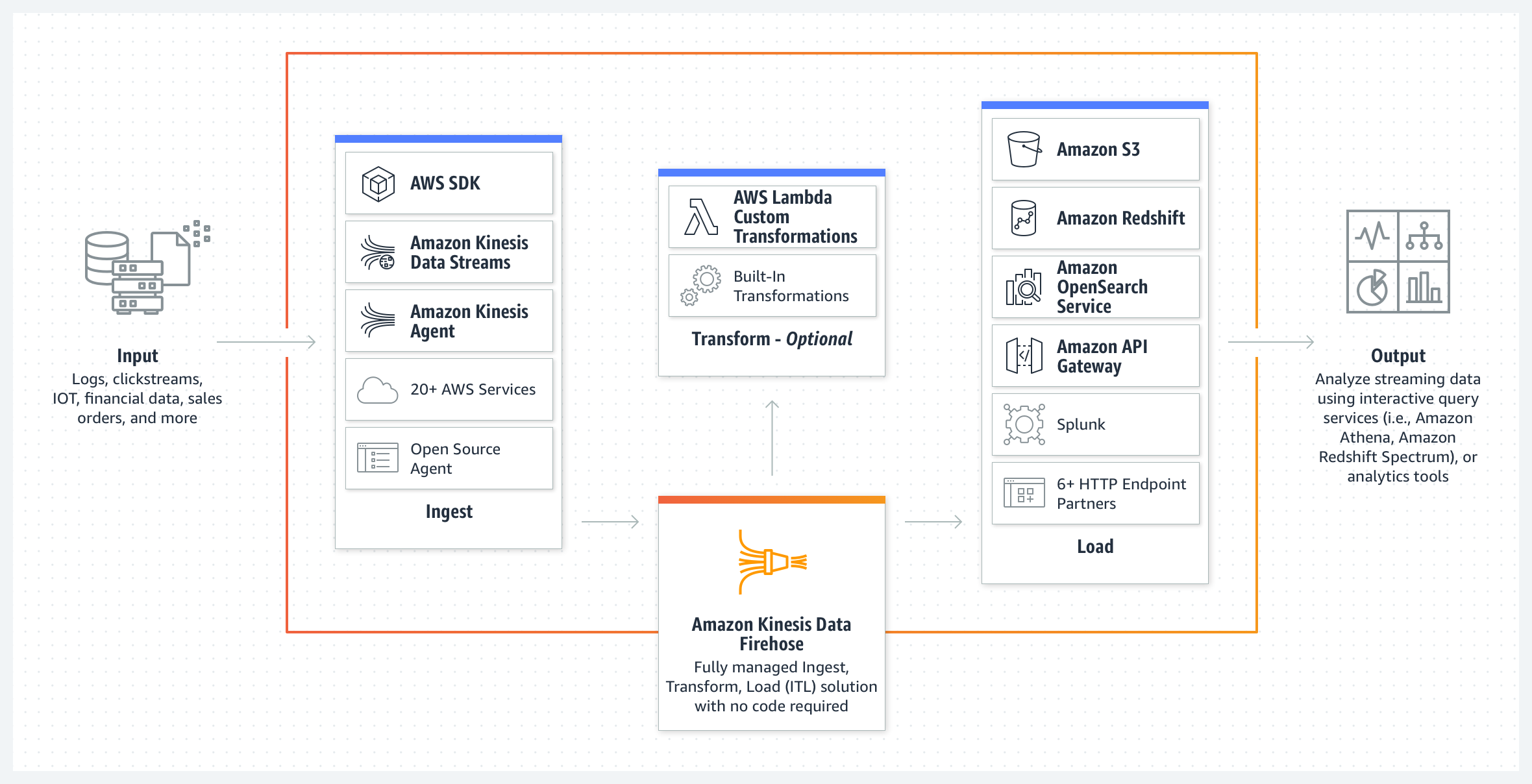
* [Amazon Kinesis Data Analytics](https://aws.amazon.com/kinesis/data-analytics/?nc=sn&loc=2&dn=4) is the easiest way to transform and analyze streaming data in real time using Apache Flink
* [**VPC Flowlogs lab**](https://amazon-es-vpc-flowlogs.workshop.aws/en/) In this workshop, you will enable an Amazon Virtual Private Cloud (VPC) flow logs ingest pipeline served from within your VPC using S3 bucket notifications, Amazon SQS and AWS Lambda to provide events to the Amazon Elasticsearch Service and with real-time monitoring using Kibana
* [Amazon Kinesis: Encryption](https://docs.aws.amazon.com/streams/latest/dev/server-side-encryption.html) server-side encryption using AWS Key Management Service (AWS KMS) keys makes it easy for you to meet strict data management requirements by encrypting your data at rest within Amazon Kinesis Data Streams
### Module 9: Security Considerations: Hybrid Environments
* [AWS Direct Connect](https://docs.aws.amazon.com/directconnect/latest/UserGuide/Welcome.html) links your internal network to an AWS Direct Connect location over a standard Ethernet fiber-optic cable
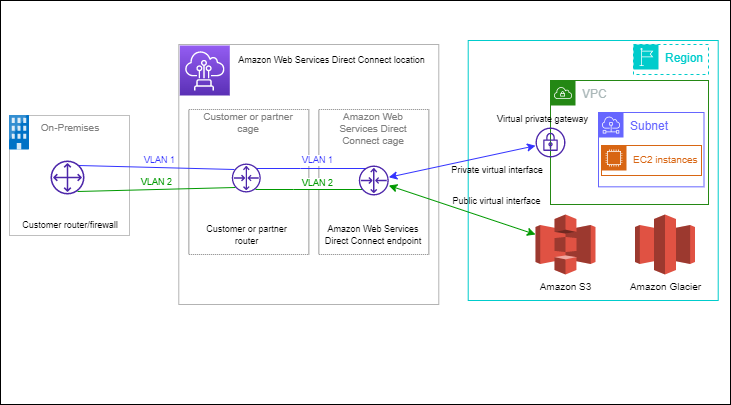
* [AWS Transit Gateway](https://aws.amazon.com/transit-gateway/?whats-new-cards.sort-by=item.additionalFields.postDateTime&whats-new-cards.sort-order=desc) allows you to easily connect Amazon VPCs, AWS accounts, and on-premises networks to a single gateway

* [AWS Site-to-Site VPN](https://docs.aws.amazon.com/vpn/latest/s2svpn/VPC_VPN.html) you can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection, and configuring routing to pass traffic through the connection
* [Transit gateway attachments to a VPC](https://docs.aws.amazon.com/vpc/latest/tgw/tgw-vpc-attachments.html) When you attach a VPC to a transit gateway, you must specify one subnet from each Availability Zone to be used by the transit gateway to route traffic
### Module 10: Out-Of-Region Protection
* [How to Help Protect Dynamic Web Applications Against DDoS Attacks by Using Amazon CloudFront and Amazon Route 53](https://aws.amazon.com/blogs/security/how-to-protect-dynamic-web-applications-against-ddos-attacks-by-using-amazon-cloudfront-and-amazon-route-53/#:~:text=AWS%20WAF%20is%20a%20web,block%20by%20defining%20security%20rules.)
* [Amazon Route 53](https://aws.amazon.com/route53/) is a highly available and scalable cloud Domain Name System (DNS) web service.
* [AWS Web Application Firewall](https://aws.amazon.com/waf/) is a web application firewall that helps protect your web applications or APIs against common web exploits and bots that may affect availability, compromise security, or consume excessive resources

* [AWS for the Edge](https://aws.amazon.com/edge/services/) Comprehensive list of available edge services on AWS
* [AWS Shield](https://aws.amazon.com/shield/) is a managed Distributed Denial of Service (DDoS) protection service that safeguards applications running on AWS
* [AWS Firewall Manager](https://aws.amazon.com/firewall-manager/) is a security management service which allows you to centrally configure and manage firewall rules across your accounts and applications in AWS Organizations
## Day 3
### Topics Covered
* [Serverless Environments](#Module-11-Security-Considerations-Serverless-Environments)
* [Threat Detection and Investigation](#Module-12-Threat-Detection-and-Investigation)
* [Secrets Management on AWS](#Module-13-Secrets-Management-on-AWS)
* [Automation and Security by Design](#Module-14-Automation-and-Security-by-Design)
* [Account Management and Provisioning on AWS](#Module-15-Account-Management-and-Provisioning-on-AWS)
### Module 11: Security Considerations: Serverless Environments
* [Amazon Cognito](https://aws.amazon.com/cognito/) lets you add user sign-up, sign-in, and access control to your web and mobile apps quickly and easily. Amazon Cognito scales to millions of users and supports sign-in with social identity providers, such as Apple, Facebook, Google, and Amazon, and enterprise identity providers via SAML 2.0 and OpenID Connect
* [Amazon Cognito: Identity Pools](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-identity.html) enables you to create unique identities for your users and federate them with identity providers
* [Amazon Cognito: User Pools](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-identity-pools.html) with this your users can sign in to your web or mobile app through Amazon Cognito
* [Amazon API Gateway](https://aws.amazon.com/api-gateway/) is a fully managed service that makes it easy for developers to create, publish, maintain, monitor, and secure APIs at any scale
* [AWS Lambda](https://aws.amazon.com/lambda/) is a serverless, event-driven compute service that lets you run code for virtually any type of application or backend service without provisioning or managing servers
* [AWS Lambda permissions](https://docs.aws.amazon.com/lambda/latest/dg/lambda-permissions.html)
### Module 12: Threat Detection and Investigation
* [Amazon GuardDuty](https://aws.amazon.com/guardduty/) is an intelligent threat detection service that provides customers with a way to continuously monitor and protect their AWS accounts and workloads

* [AWS Security Hub](https://aws.amazon.com/security-hub/) is a cloud security posture management service that performs security best practice checks, aggregates alerts, and enables automated remediation

* [Amazon Detective](https://aws.amazon.com/detective/) makes it easy to analyze, investigate, and quickly identify the root cause of potential security issues or suspicious activities
### Module 13: Secrets Management on AWS
* [AWS Key Management Service](https://aws.amazon.com/kms/) makes it easy for you to create and manage cryptographic keys and control their use across a wide range of AWS services and in your applications
* [AWS CloudHSM](https://aws.amazon.com/cloudhsm/) is a cloud-based hardware security module (HSM) that enables you to easily generate and use your own encryption keys on the AWS Cloud

* [AWS Secrets Manager](https://aws.amazon.com/secrets-manager/) helps you protect secrets needed to access your applications, services, and IT resources
### Module 14: Automation and Security by Design
* [AWS CloudFormation](https://aws.amazon.com/cloudformation/) lets you model, provision, and manage AWS and third-party resources by treating infrastructure as code.
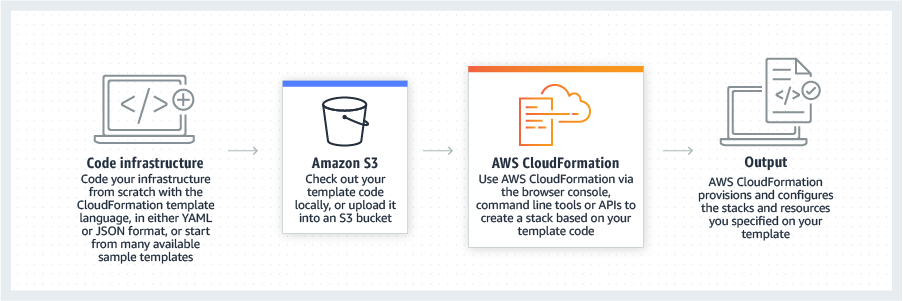
* [AWS Service Catalog](https://aws.amazon.com/servicecatalog/?aws-service-catalog.sort-by=item.additionalFields.createdDate&aws-service-catalog.sort-order=desc) allows organizations to create and manage catalogs of IT services that are approved for use on AWS
* [AWS CloudTrail](https://aws.amazon.com/cloudtrail/) monitors and records account activity across your AWS infrastructure, giving you control over storage, analysis, and remediation actions

* [AWS Config](https://aws.amazon.com/config/) is a service that enables you to assess, audit, and evaluate the configurations of your AWS resources

* [Amazon CloudWatch](https://aws.amazon.com/cloudwatch/) provides you with data and actionable insights to monitor your applications, respond to system-wide performance changes, and optimize resource utilization

### Module 15: Account Management and Provisioning on AWS
* [AWS Organizations](https://aws.amazon.com/organizations/) helps you centrally manage and govern your environment as you grow and scale your AWS resources
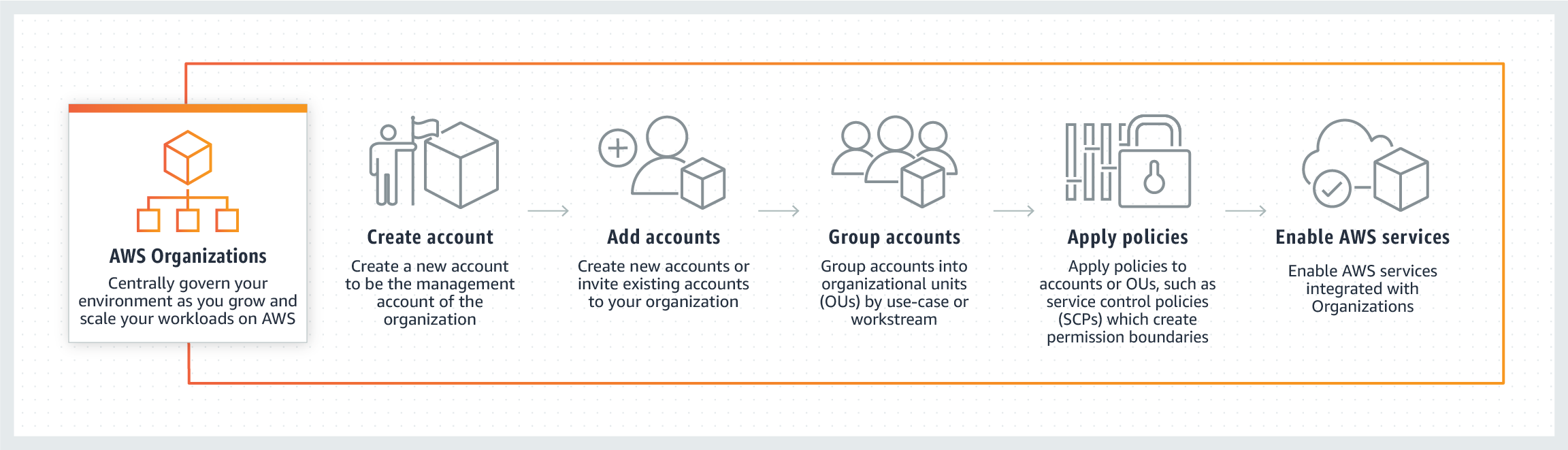
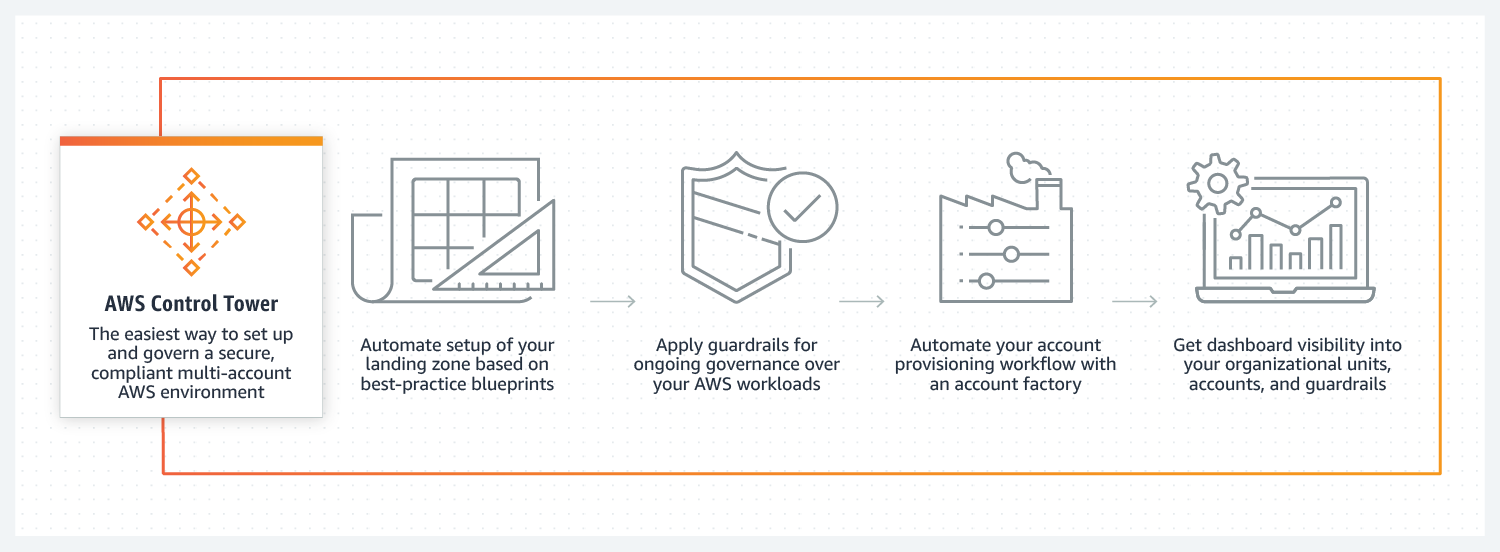
* [AWS Control Tower](https://aws.amazon.com/controltower) provides you with a single location to set up a well-architected multi-account environment to govern your AWS workloads with rules
* [AWS Single Sign-On](https://aws.amazon.com/single-sign-on/) is where you create, or connect, your workforce identities in AWS once and manage access centrally across your AWS organization

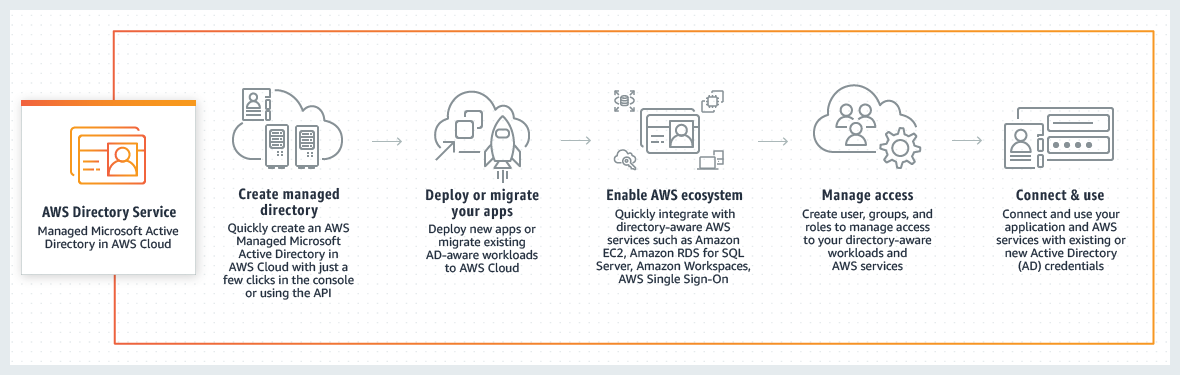
* [AWS Directory Service](https://aws.amazon.com/directoryservice/) enables your directory-aware workloads and AWS resources to use managed Active Directory (AD) in AWS