---
GA: UA-7042909-2
---
# Threat Hunting
[TOC]
## OSINT & Recon
Attack infrastructure is often easy to identify, appearing like a shell of a legitimate server thus we will need to take additional steps with our infrastructure to increase the likelihood of blending in with real servers, and keep our adversaries (incident responders & blue teams) away - or face the consequences of burned infrastructure (as the following Twit demonstrates).
> [name=Remco Verhoef ([@remco_verhoef](https://twitter.com/remco_verhoef/status/1105593775026589696?ref_src=twsrc%5Etfw))] [time=March 12, 2019]
> Powershell Empire http(s) listeners have unique signature, can be used to search on [@censysio](https://twitter.com/censysio?ref_src=twsrc%5Etfw). Using \n newlines instead of \r\n, returning 200 instead of 404 and append extra spaces for non-existing urls. List of found servers added to gist. Redteaming? [https://gist.github.com/nl5887/230e10909c8369b9586db76f0b12a400](https://gist.github.com/nl5887/230e10909c8369b9586db76f0b12a400) [https://pic.twitter.com/t1eEdufNKt](https://pic.twitter.com/t1eEdufNKt)
In order to make our steps at obscuring our infrastructure as efficient as possible - a through understanding of the tools incident responders use while hunting for red team infrastructure is required. In the following sections - we'll cover various such methods, datasets commonly used and go over some additional premiers of when failing to properly obscure one infrastructure let to the burning of the infrastrucre (or even the whole operation).
### Techniques & Methods

* [Asset discovery](https://0xpatrik.com/asset-discovery/)
* [Port scanning](http://phrack.org/issues/51/11.html)
:::info
##### Nmap Network Scanning
* [Chapter 4.1. Introduction to Port Scanning](https://nmap.org/book/port-scanning.html#port-scanning-intro)
* [Chapter 5. Port Scanning Techniques and Algorithms](https://nmap.org/book/scan-methods.html)
:::
#### Fast Port Scanning
* [Masscan: the entire Internet in 3 minutes](https://blog.erratasec.com/2013/09/masscan-entire-internet-in-3-minutes.html)
:::info
> [masscan](https://github.com/robertdavidgraham/masscan)
> TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes.
:::
* :thought_balloon: Unicorn scan
{%pdf https://www.defcon.org/images/defcon-13/dc13-presentations/DC_13-Lee.pdf %}
* :thought_balloon: [SYNCookies](https://cr.yp.to/syncookies.html)
* :thought_balloon: ZMap: Fast Internet-Wide Scanning and its Security Applications
{%pdf https://zmap.io/paper.pdf %}
https://docs.google.com/presentation/d/1R-3eqlt31sL7_rj2f1_vGEqqb7hcx4vxX_L7E23lJVo/edit#slide=id.g3af0ae9b4b_3_306
> Up to the XSS chapter
>
{%youtube Qw1nNPiH_Go %}
{%speakerdeck 0xbharath/practical-recon-techniques-for-bug-hunters-and-pentesters %}
:::info
https://drive.google.com/open?id=1VpRT8dFyTaFpQa9jhehtmGaC7TqQniMSYbUdlHN6VrY
> Useful reference slide
:::
#### Service Fingerprinting
* [TLS Fingerprinting with JA3 and JA3S](https://engineering.salesforce.com/tls-fingerprinting-with-ja3-and-ja3s-247362855967)
:::info
{%youtube NI0Lmp0K1zc %}
:::
> :thought_balloon: [JA3](https://github.com/salesforce/ja3)
> JA3 is a standard for creating SSL client fingerprints in an easy to produce and shareable way.
> * [Fingerprint Lists](https://github.com/salesforce/ja3/tree/master/lists)
> * [JA3 TLS Fingerprint database](https://github.com/trisulnsm/ja3prints)
* [Open Sourcing HASSH](https://engineering.salesforce.com/open-sourcing-hassh-abed3ae5044c)
:::info
{%pdf https://github.com/benjeems/Presentations/blob/master/BSides%202019%20%20-%20HASSH%20-%20a%20Profiling%20Method%20for%20SSH%20Clients%20and%20Servers.pdf %}
:::
> :thought_balloon: [HASSH](https://github.com/salesforce/hassh)
> HASSH is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be easily stored, searched and shared in the form of a small MD5 fingerprint.
> * [Fingerprints List](https://github.com/salesforce/hassh/tree/master/python/hasshGen)
:::info
#### OS Fingerprinting
* [Passive OS Fingerprinting](https://www.netresec.com/?page=Blog&month=2011-11&post=Passive-OS-Fingerprinting)
* [Remote OS detection via TCP/IP Stack FingerPrinting](http://phrack.org/issues/54/9.html#article)
* Chatter DHCP
{%pdf https://web.archive.org/web/20120222064258/http://myweb.cableone.net/xnih/download/Chatter-DHCP.pdf %}
* [TCP/IP Fingerprinting Methods Supported by Nmap](https://nmap.org/book/osdetect-methods.html)
* [p0f v3: passive fingerprinter](http://lcamtuf.coredump.cx/p0f3/README)
* OS Fingerpinting {%pdf https://web.archive.org/web/20090816152743fw_/http://myweb.cableone.net:80/xnih/download/OS%20Fingerprint.pdf %}
* SinFP
{%pdf https://www.metabrik.org/wp-content/uploads/2015/02/SinFP3EuSecWest-ekoparty-v1.1.pdf %}
:::
### Datasets
#### WHOIS
[What Does WhoIs Data have to do with Cybersecurity](https://www.domaintools.com/resources/blog/what-does-whois-data-have-to-do-with-cybersecurity)
> Whois data helps you understand who is behind nefarious domains and IPs, and helps you connect domains and IPs to each other and to their owners.
>
:::spoiler How WHOIS data ensures a safe and secure internet
> A detailed look at how public domain ownership data drives three essential cybersecurity workflows
{%pdf https://www.domaintools.com/content/Whois_Data_Ensures_Safe_Secure_Internet_White_Paper.pdf %}
:::
###### tags: TODO
Reverse WHOIS
#### Passive DNS Replication (PDNS)
[Passive DNS replication](http://techgenix.com/what-passive-dns/) is a technology which constructs zone replicas without cooperation from zone administrators, based on captured name server responses. The main idea behind passive DNS is as follows:
* Inter-server DNS messages are captured by sensors and forwarded to a collection point for analysis.
* After being processed, individual DNS records are stored in a database where they can be indexed and queried.
As such, passive DNS can help in answering the following questions:
* Where did this domain name point to in the past?
* What domain names are hosted by a given nameserver?
* What domain names point into a given IP network?
* What subdomains exist below a certain domain name?
{%pdf https://www.apricot.net/apricot2012/__data/assets/pdf_file/0017/45521/05-Merike-Kaeo-Passive-DNS.pdf %}
:::spoiler Open Passive DNS Providers
* [mnemonic.no](https://passivedns.mnemonic.no/)
* [PassiveTotal](https://community.riskiq.com)
* [Farsight](https://www.farsightsecurity.com/dnsdb-community-edition/)
> Limited access to the Farsight Security DNSDB.
> * 500 queries/month
> * up to 25 queries/hour with 256 results per query
> * Results up to 90 days old (instead of 9 years in the commercial version)
> * monthly renewal
:::
#### Additional Passive Datasets & Methods
:::success
* Reverse DNS
* [Web Crawls](https://www.riskiq.com/blog/analyst/whats-in-a-web-crawl/)
* Web Trackers
* Co-occurence/host-pairs
> 
* [Discovering Malicious Domains Using Co-Occurrences](https://umbrella.cisco.com/blog/2013/07/24/co-occurrences/)
* [Derived Host Pairs from Web Crawling](https://www.riskiq.com/blog/analyst/derived-host-pairs-from-web-crawling/)
> Simply put, host pairs are two domains (a parent and a child) that shared a connection observed from a crawl. The connection could range from a top-level redirect (HTTP 302) to something more complex like an iframe or script source reference. What makes this dataset powerful is the ability to understand relationships between hosts based on details from visiting the actual page.
>
{%vimeo 224359261 %}
* (Reverse) Whois
:::
:::info
###### tags: TODO
:::spoiler
* Domain Categorization
* Domain Reputation
* IP Reputaion
:::
#### Internet-wide Scans
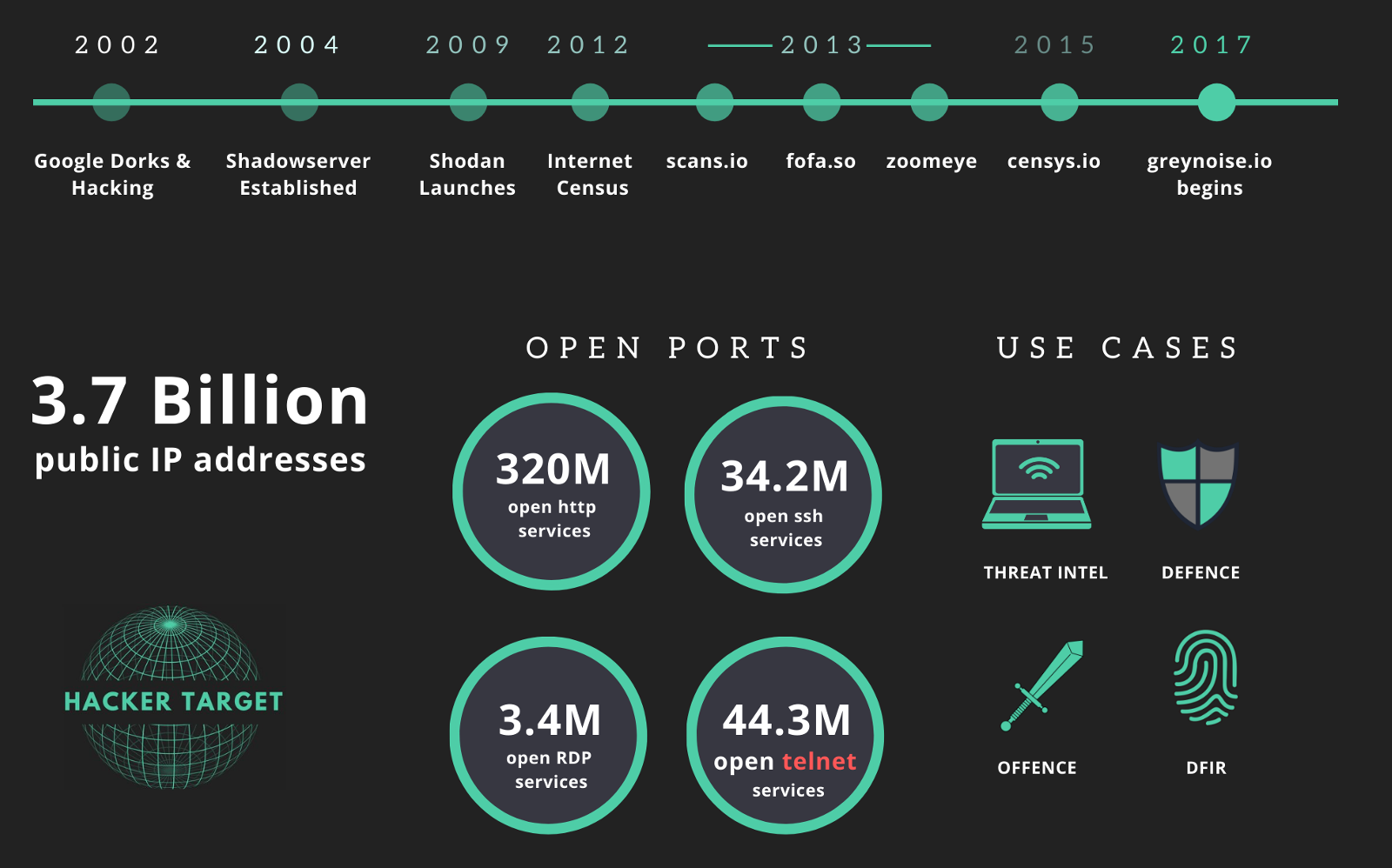
Mapping the Internt - an overview of internet-wide scanning
* [Mapping the Internet, One Device at a Time](https://duo.com/decipher/mapping-the-internet-one-device-at-a-time-part-one)
* [Mapping the Internet, Navigation](https://duo.com/decipher/mapping-the-internet-navigation-part-two)
* [Mapping the Internet, Who’s Who?](https://duo.com/decipher/mapping-the-internet-whos-who-part-three)
:::info
:::spoiler Brief History of Internet Wide Scanning
[Brief History of Internet Wide Scanning](https://hackertarget.com/remote-access-granted/)
> In the beginning, there were Google Dorks, as far back as 2002 security researchers discovered specific Google queries revealed Internet-connected devices. Seventeen years later, it is still possible to find thousands of unsecured remotely accessible security cameras and printers via simple Google searches.
>
> Now using search engines such as Shodan.io and Censys.io, it has become commonplace to passively discover open services (and devices) on the Internet.
>
:::
:::success
{%slideshare JamieOHare6/internetwide-scanning-jamie-ohare %}
:::spoiler Internet-wide scan data providers
* [Shodan](shodan.io)
> Shodan gathers information about all devices directly connected to the Internet. If a device is directly hooked up to the Internet then Shodan queries it for various publicly-available information. The types of devices that are indexed can vary tremendously: ranging from small desktops up to nuclear power plants and everything in between.
* [Shodan Tips](/kTkC5WGFSL2iGIABKzrSzw)
* [Censys](censys.io)
>
> A Search Engine Backed by Internet-Wide Scanning (Slides)
> {%pdf https://dadrian.io/srv/talks/censys-ccs.pdf %}
> :thought_balloon: A Search Engine Backed by Internet-Wide Scanning (censys.io whitepaper)
> {%pdf https://jhalderm.com/pub/papers/censys-ccs15.pdf %}
* [ZoomEye](https://www.zoomeye.org/)
> ZoomEye is a Cyberspace Search Engine recording information of devices, websites, services and components etc.
>
> ZoomEye has two powerful detection engines Xmap and Wmap aiming at devices and websites in the cyberspace. It can be used to identify all the services and components through 24/7 continuous detection. Therefore it is easier for researchers to understand the component coverage and the damage scope of vulnerabilities.
* [Fofa](https://fofa.so/)
> FOFA is a cyberspace search engine. It can help users quickly match network assets and speed up the follow-up work process. For example, vulnerability vulnerability scope analysis, application distribution statistics, application popularity ranking statistics, and the like.
* [ONYPHE](https://www.onyphe.io/)
> ONYPHE is a search engine for open-source and cyber threat intelligence data collected by crawling various sources available on the Internet or by listening to Internet background noise. ONYPHE does correlate this information with data gathered by performing active Internet scanning for connected devices. It then normalizes information and make it available via an API and its search language.
* [BinaryEdge](https://app.binaryedge.io)
> Cybersecurity/Data Science company that focuses its effort on acquiring, analyzing and classifying internet wide data which includes -
> * Internet-wide scans for ~200 ports
> * Honeypot/Sensor network monitoring
> * Dataleaks monitoring
> * DHT monitoring
> * SSL certificates & DNS enumeration
* [scans.io](https://scans.io)
> The Internet-Wide Scan Data Repository is a public archive of research datasets that describe the hosts and sites on the Internet. The repository contains raw data from censys.io, Rapid7 Project Sonar and other 3rd parties.
:::
:::info
[GreyNoise](https://greynoise.io/blog/2018/2/1/what-is-greynoise)
> GreyNoise Intelligence knows. The security company has found a way to collect omnidirectional Internet-wide IPv4 scan traffic and present researchers with the IPs that are targeting them specifically — thus creating a rock-solid negative ground truth of what everybody should expect to see when looking at their logs.
>
> {%slideshare andrewwantsyou/the-background-noise-of-the-internet %}
> [GreyNoise Visualizer](https://viz.greynoise.io)
:::spoiler Even more Internet-wide scanning...
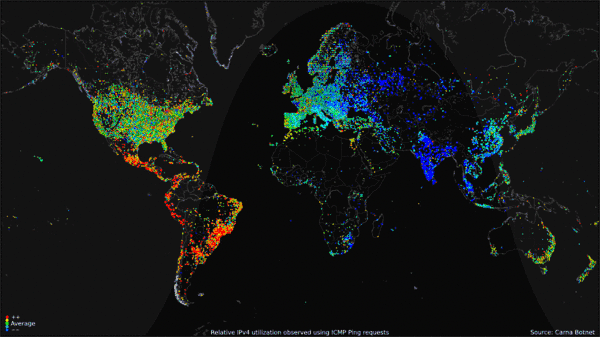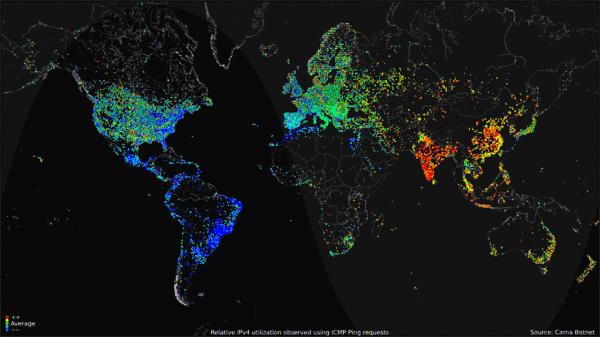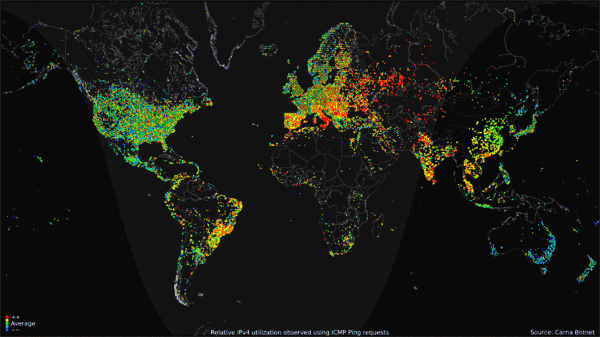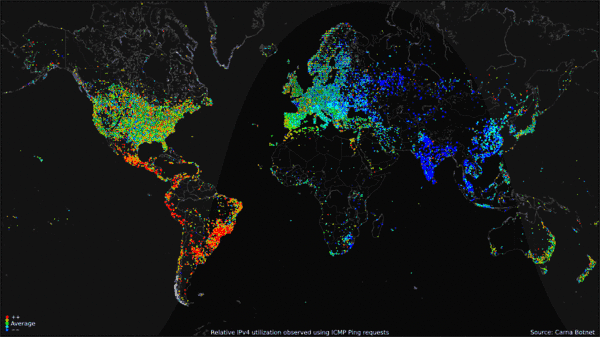
The Carna Botnet/[Internet Census 2012](http://census2012.sourceforge.net/paper.html)
> 
>
> While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
>
> All data gathered during our research is released into the public domain for further study.
An Internet-Wide View of Internet-Wide Scanning
> While it is widely known that port scanning is widespread,neither the scanning landscape nor the defensive reactionsof network operators have been measured at Internet scale. In this work, we analyze data from a large network tele-scope to study scanning activity from the past year, un-covering large horizontal scan operations and identifyingbroad patterns in scanning behavior. We present an analy-sis of who is scanning, what services are being targeted,and the impact of new scanners on the overall landscape.We also analyze the scanning behavior triggered by recentvulnerabilities in Linksys routers, OpenSSL, and NTP.We empirically analyze the defensive behaviors that orga-nizations employ against scanning, shedding light on whodetects scanning behavior, which networks blacklist scan-ning, and how scan recipients respond to scans conductedby researchers. We conclude with recommendations forinstitutions performing scans and with implications ofrecent changes in scanning behavior for researchers andnetwork operators.
>
> {%pdf https://jhalderm.com/pub/papers/scanning-sec14.pdf %}
:::
#### Threat Intelligence & Hunting Adversary Infrastructure
Scan't Touch This - Proactively Detect Adversaries Beyond Your Environment
> An overview of using netwrok scan data from a variety of sources to proactively detect adversary infrastructure. Includes some examples.
>
> {%pdf https://github.com/aaronst/talks/blob/master/scanttouchthis.pdf %}
:::info
:::spoiler Search engines useful for threat hunting
* [Spyse](https://spyse.com/)
> A search engine for "pentesters and cyber security specialists" that allows easily correlate WHOIS, DNS, ASN, SSL and IP scan data.
* [Netcraft](https://toolbar.netcraft.com/search/)
> A search engine that generates a detailed report meant to gauge the trustworthiness of a wb site and includes hosting history, "risk score", bill of components, SSL details and misconfigurations, etc.
:::
:::success
##### Primer - Hunting for Cobalt Strike Team Servers
An overview of using scans.io data, and a web server bug adding an extraneous space to the response for tracking historic Cobalt Strike "team server" deployments.
[Identifying Cobalt Strike team servers in the wild](https://blog.fox-it.com/2019/02/26/identifying-cobalt-strike-team-servers-in-the-wild/)
> 
>
[CobaltStrike data with passiveSSL](https://www.alexanderjaeger.de/cobaltstrike-data-with-passivessl/)
> A follow up post showing adding additional context using VirusTotal PDNS & CIRCL Passive SSL
:::spoiler Additional primers
##### Primer - CitizenLab vs. NSO
An outstanding primer on using OSINT to discover and pivot on C&C infrastructure
* [The Million Dollar Dissident](https://citizenlab.ca/2016/08/million-dollar-dissident-iphone-zero-day-nso-group-uae/)
* [Amnesty International Among Targets of NSO-powered Campaign](https://www.amnesty.org/en/latest/research/2018/08/amnesty-international-among-targets-of-nso-powered-campaign/)
* [HIDE AND SEEK](https://citizenlab.ca/2018/09/hide-and-seek-tracking-nso-groups-pegasus-spyware-to-operations-in-45-countries/ )
##### Primer - Darkleech & Bit.ly
[Darkleech + Bitly.com = Insightful Statistics](https://blog.sucuri.net/2014/02/darkleech-bitly-com-insightful-statistics.html)
> A post is about how hackers abuse popular web services and how this helps security researchers obtain interesting statistics about malware attacks.
>
> :thought_balloon: [Working With the Darkleech Bitly Data](http://blog.unmaskparasites.com/2014/02/10/working-with-the-darkleech-bitly-data
* https://www.carbonblack.com/blog/threat-analysis-active-c2-discovery-using-protocol-emulation-part2-winnti-4-0/
* https://www.fireeye.com/blog/threat-research/2020/07/scandalous-external-detection-using-network-scan-data-and-automation.html
* https://community.riskiq.com/article/5fe2da7f, https://community.riskiq.com/article/56fa1b2f
* https://zetalytics.com/pdfs/2019-07_two_min_proton_pivots.pdf
:::