---
GA: UA-7042909-2
---
# Linux & IoT Malware
[TOC]
## General Linux Malware
### Overview
#### Modern Linux Malware Exposed
> The research on analysis and detection of malware has shown notable progresses over the years, but mainly related to malicious programs for Windows systems. However, the adoption of Linux-based machines (e.g. servers, desktops, IoT devices) is rapidly increasing, attracting the attention of malware writers. Linux malware pose new challenges going from their ability to target a broad choice of CPU architectures, to the study of malicious techniques different from the ones seen in the Windows world.
>
> In this presentation we propose the first automatic analysis pipeline to perform large-scale analysis of Linux malware. Our system tries to avoid, or limit, reverse engineering efforts usually performed manually. For example, some analysis modules, run as parallel jobs, are in charge of performing static analysis on the binary and its ELF header. On the other hand, the modules for dynamic analysis runs Linux samples in sandboxes for x86, ARM, MIPS or PPC architectures.
>
> The talk will be about what Linux reverse engineers should look for when dissecting Linux samples, anomalies that can arise from the ELF header, persistence and evasion strategies and how we get insights on malware interactions with the system. All these cases are recent and have been observed in the wild in the last year. Finally, we will explain how we built multi-architecture sandboxes by using kprobes and uprobes, a debugging facility integrated in the Linux kernel. The analysis infrastructure for Linux-based malware will be released as a free service. Moreover, the full dataset will be provided to researchers upon request.
>
{%pdf https://emanuelecozzi.net/docs/recon18_linux_malware.pdf %}
#### Linux code injection techniques
##### LD_PRELOAD
{%slideshare chimerawang/something-about-dynamic-linking %}
[Dynamic linker tricks: Using LD_PRELOAD to cheat, inject features and investigate programs](https://rafalcieslak.wordpress.com/2013/04/02/dynamic-linker-tricks-using-ld_preload-to-cheat-inject-features-and-investigate-programs/)
> Linux puts you in full control. This is not always seen from everyone’s perspective, but a power user loves to be in control. I’m going to show you a basic trick that lets you heavily influence the behavior of most applications, which is not only fun, but also, at times, useful.
>
##### ptrace
[Dynamically Inject a Shared Library Into a Running Process on Android/ARM](https://www.evilsocket.net/2015/05/01/dynamically-inject-a-shared-library-into-a-running-process-on-androidarm/)
> If you’re familiar with Windows runtime code injection you probably know the great API CreateRemoteThread which lets us force an arbitrary running process to call LoadLibrary and load a DLL into its address space, this technique called DLL Injection is often used to perform user space API hooking.
>
> Unfortunately there’s no CreateRemoteThread equivalent on Linux system, therefore we can only rely on ptrace and our brain :D
> This article will explain how to perform DLL Injection on Linux systems.
>
<br />
[Linux ptrace introduction AKA injecting into sshd for fun](https://blog.xpnsec.com/linux-process-injection-aka-injecting-into-sshd-for-fun/)
> If there is one thing I've come to appreciate over this past few weeks, it's just how much support you are provided from the Win32 API. That being said, I wanted to tackle some Linux process injection, with the aim of loading a shared object into another process address space without having to resort to LD_PRELOAD, or stopping the process.
>
> The goal I set myself was quite simple, could I recover plain text credentials from the sshd process using ptrace. Granted, this is a bit of an arbitrary goal, as there are many other ways to achieve the same result much more effectively (and with much less chance of SEGV), but I thought it would be cool to see this in action.
>
<br />
[linux-inject](https://github.com/gaffe23/linux-inject)
> Tool for injecting a shared object into a Linux process
> * Provides the Linux equivalent of using `CreateRemoteThread()` on Windows to inject a DLL into a running process
> * Performs injection using `ptrace()` rather than LD_PRELOAD, since the target process is already running at the time of injection
> * Supports x86, x86_64, and ARM
> * Does not require the target process to have been built with `-ldl` flag, because it loads the shared object using `__libc_dlopen_mode()` from libc rather than `dlopen()` from libdl
>
{%pdf https://github.com/gaffe23/linux-inject/raw/master/slides_BHArsenal2015.pdf %}
---
[Jugaad](https://github.com/aseemjakhar/jugaad)
> Thread Injection Kit. A notorious little attempt to create Windows CreateRemoteThread() equivalent on unix (\*nix) platform.
>
{%youtube a4fnqHrHKzY %}
:::spoiler Slides
{%pdf https://media.defcon.org/DEF%20CON%2019/DEF%20CON%2019%20presentations/DEF%20CON%2019%20-%20Jakhar-Jugaad-Linux-Thread-Injection.pdf %}
:::
###### GDB
[Process Injection with GDB](https://magisterquis.github.io/2018/03/11/process-injection-with-gdb.html)
> I set out to work out an easy way to inject into processes in Linux. There’s been quite a lot of experimentation with this already, usually using ptrace(2) or LD_PRELOAD, but I wanted something a little simpler and less error-prone, perhaps trading ease-of-use for flexibility and works-everywhere. Enter GDB and shared object files (i.e. libraries).
##### ptrace-less
###### sys_process_vm_writev
:::spoiler Overview
{%gist hugsy/8703018%}
:::
<br />
[Injecting Code in Running Processes with Python and Ptrace](https://ancat.github.io/python/2019/01/01/python-ptrace.html)
:thought_balloon: Regardless of it's name - this article demonstrates using `sys_process_vm_writev`.
###### Direct /proc Manipulation
[Linux based inter-process code injection without ptrace(2)](https://blog.gdssecurity.com/labs/2017/9/5/linux-based-inter-process-code-injection-without-ptrace2.html)
> Using the default permission settings found in most major Linux distributions it is possible for a user to gain code injection in a process, without using ptrace. Since no syscalls are required using this method, it is possible to accomplish the code injection using a language as simple and ubiquitous as Bash. This allows execution of arbitrary native code, when only a standard Bash shell and coreutils are available. Using this technique, we will show that the noexec mount flag can be bypassed by crafting a payload which will execute a binary from memory.
>
<br />
[Linux based inter-process code injection without ptrace(2)](https://github.com/AonCyberLabs/Cexigua)
[dlinject.py](https://github.com/DavidBuchanan314/dlinject)
> Inject a shared library (i.e. arbitrary code) into a live linux process, without ptrace
>
##### Fileless
[Pure In-Memory (Shell)Code Injection In Linux Userland](https://blog.sektor7.net/#!res/2018/pure-in-memory-linux.md )
> Imagine yourself sitting in front of a blinking cursor, using a shell on a freshly compromised Linux server, and you want to move forward without leaving any traces behind. You need to run additional tools, but you don't want to upload anything to the machine. Or, you simply cannot run anything because the noexec option is set on mounted partitions. What options remain?
>
<br />
[Super-Stealthy Droppers](https://0x00sec.org/t/super-stealthy-droppers/3715)
> In this paper we are going to talk about how to use these functions to develop a super-stealthy dropper. You could consider it as a malware development tutorial… but you know that it is illegal to develop and also to deploy malware. This means that, this paper is only for educational purposes… because, after all, a malware analyst needs to know how malware developers do their stuff in order to identify it, neutralise it and do what is needed to keep systems safe.
>
<br />
[Execute ELF files on a machine without dropping an ELF](https://github.com/neonsea/fileless-elf-exec)
> This Python script generates interpreted code which creates the supplied ELF as a file in memory and executes it (without tmpfs). This makes it possible to execute binaries without leaving traces on the disk.
>
<br />
[Reflective SO Injection](https://github.com/infosecguerrilla/ReflectiveSOInjection)
> Reflective SO Injection was inspired by the concept of Reflective DLL Injection. It is virtually the same thing, but implemented to allow loading of SO (Shared Objects) on Linux. Currently only x86_64 is supported and it is only a prototype. The loader code was written by myself, but with the injection code I stole quite a bit of code from the linux-inject project since there is no sense in redoing what has already been done.
>
##### Misc
###### Adventures in systemd Injection
> Injecting into Linux processes is nothing new, but it's a great way to get malicious code running without an additional process.Libpcap is also nothing new, but it's a great way to have malware wait for something interesting.Systemd is somewhat new, but it's a great place to inject malware using libpcap.Or so I thought.This talk follows the speaker's journey trying to inject a libpcap-based tool into systemd.Along the way we'll see how to get a running process to load a library, hook functions the easy way, and dodge selinux.
<iframe src="https://docs.google.com/presentation/d/e/2PACX-1vRU08oNbbJQoZ5iuDGoKYuVGOzapZD3hrgz7SqlIeoH03K9UcziLgsIfVsOYUFyrX4P0bE9opx1z5t1/embed?start=false&loop=false&delayms=3000" frameborder="0" width="672" height="560" allowfullscreen="true" style="border:1px solid #CCC; border-width:1px; margin-bottom:5px; max-width: 100%;" mozallowfullscreen="true" webkitallowfullscreen="true"></iframe>
:::spoiler video
{%youtube PaBLBVb4eMY %}
:::
### Rootkits
- [ ] TODO: Find a good overview presentation
[A Poor Man's "Rootkit"](https://www.jakoblell.com/blog/2014/05/07/hacking-contest-rootkit/#toc-1)
> This blogpost shows how to install a simple rootkit with one single (but relatively long) line on a terminal. While the rootkit is not as capable and hard to detect as a full kernel rootkit, it is still able to hide itself, other files, running processes and even open TCP/UDP ports from the system administrator.
>
<br />
[Awesome Linux Rootkits](https://github.com/milabs/awesome-linux-rootkits)
#### LD_PRELOAD
[Hiding Linux processes for fun + profit](https://sysdig.com/blog/hiding-linux-processes-for-fun-and-profit/)
> The other day I was looking at the output of top on my machine, and I wondered: how hard would it be to hide specific processes and/or network connections from traditional monitoring tools like ps, top, lsof, …? I decided to kill a couple hours and try to hack together a solution. In this post, I’ll show you some of the answers I came up with, and some proof of concept code to implement this. I’ll also show that sysdig is not susceptible to my hack, and explain why.
>
> The goal that I want to achieve is to deliberately hide a simple and malicious Python script (I’ll call it evil_script.py) that does some damage to my system, saturating CPU and network by sending UDP packets towards a poor victim
>
[Code](https://github.com/gianlucaborello/libprocesshider)
<br />
[Zombie Ant Farm: A Kit For Playing Hide and Seek with Linux EDRs](https://github.com/dsnezhkov/zombieant)
> EDR solutions have landed in Linux. With the ever increasing footprint of Linux machines deployed in data centers, offensive operators have to answer the call.
>
> In the first part of the talk we will share practical tips and techniques hackers can use to slide under the EDR radar, and expand post-exploitation capabilities.
>
> We will see how approved executables could be used as decoys to execute foreign functionality. We will walk through the process of using well known capabilities of the dynamic loader. We will take lessons from user-land root-kits in evasion choices.
>
> Part two will focus on weaponizing the capabilities. We will show how to create custom preloaders, and use mimicry to hide modular malware in memory. We will create a "Preloader-as-a-Service" capability of sorts by abstracting storage of modular malware from its executing cradles. This PaaS is free to you though!
>
{%youtube Ed-LTOZmCeA %}
:::spoiler Slides
{%pdf https://github.com/dsnezhkov/zombieant/raw/master/ZombieAntFarmPracticalTips.pdf %}
:::
##### Sample implementation
[JynxKit](https://github.com/chokepoint/jynxkit)
> JynxKit is an LD_PRELOAD userland rootkit for Linux systems with reverse connection SSL backdoor
>
:thought_balloon: JynxKit is one of the first LD_PRELOAD rootkit implementations, and a great example for learning how to implement such an enterprise
<br />
[Azazel](https://github.com/chokepoint/azazel)
> Azazel is a userland rootkit based off of the original LD_PRELOAD technique from Jynx rootkit. It is more robust and has additional features, and focuses heavily around anti-debugging and anti-detection.
>
:thought_balloon: Azazel is a full features LD_PRELOAD rootkit.
<br />
[bedevil - LD_PRELOAD Linux rootkit (x86 & ARM)](https://github.com/naworkcaj/bdvl)
:thought_balloon: bedevil is a modern take on a LD_PRELOAD rootkit.
#### LKMs
[(nearly) Complete Linux Loadable Kernel Modules](https://web.archive.org/web/20190911151525/http://www.ouah.org/LKM_HACKING.html)
> The use of Linux in server environments is growing from second to second. So hacking Linux becomes more interesting every day. One of the best techniques to attack a Linux system is using kernel code. Due to its feature called Loadable Kernel Modules (LKMs) it is possible to write code running in kernel space, which allows us to access very sensitive parts of the OS.
>
:::spoiler LKMs In-Depth
:::info
[Abuse of the Linux Kernel for Fun and Profit]( http://phrack.org/issues/50/5.html)
> Loadable modules are a very useful feature in linux, as they let you load device drivers on a as-needed basis. However, there is a bad side: they make kernel hacking almost TOO easy. What happens when you can no longer trust your own kernel...? This article describes a simple way kernel modules can be easily abused.
>
<br />
[Runtime Kernel KMEM Patching](https://web.archive.org/web/20020806064602/http://www.big.net.au/~silvio/runtime-kernel-kmem-patching.txt)
> This paper documents runtime (on the fly) kernel patching on a running system under Linux using direct access to kernel memory. The same algorithms may equally be applicable to other systems. Examples of kernel patching for use by an attacker is provided showing patching of kernel structures to remove a lkm's visibility to lsmod and even the addition of kernel code ala loadable kernel modules (lkm) to a running system without native lkm support in the kernel. Discussion of rebuilding the appropriate sections of the system symbol map (System.map) is provided and implemented.
>
<br />
[Linux on-the-fly kernel patching without LKM](http://phrack.org/issues/58/7.html)
> In this paper, we will discuss way of abusing the Linux kernel (syscalls mostly) without help of module support or System.map at all, so that we assume that the reader will have a clue about what LKM is, how a LKM is loaded into kernel etc.
>
> Imagine a scenario of a poor man which needs to change some interesting linux syscall and LKM support is not compiled in. Imagine he have got a box, he got root but the admin is so paranoid and he (or tripwire) don't poor man's patched sshd and that box have not gcc/lib/.h needed for compiling of his favourite LKM rootkit. So there are some solutions, step by step and as an appendix, a full-featured linux-ia32 rootkit, an example/tool, which implements all the techinques described here.
>
<br />
[Writing a Simple Linux Rootkit](https://web.archive.org/web/20160725125039/http://big-daddy.fr:80/repository/Documentation/Hacking/Security/Malware/Rootkits/writing-rootkit.txt)
<br />
[Magic Packets in Linux Kernel Land](http://www.drkns.net/kernel-who-does-magic/)
> This post covers the basics of writing a Loadable Kernel Module (LKM) that hooks Netfilter and listens for a magic packet. Upon receiving the packet, it spawns a hidden process on a listening port or a connect back port, without the kernel module appearing in the list of loaded modules. By hooking netfilter like this its not going to matter whether iptables rules drop or accept the packet - it's already too late.
>
<br />
:::
##### Sample implementation
* [EnyeLKM Rootkit](https://github.com/David-Reguera-Garcia-Dreg/enyelkm)
* [Reptile LKM Rootkit](https://github.com/f0rb1dd3n/Reptile)
#### Ramdisk
##### HORSEPILL
[Code](https://github.com/r00tkillah/HORSEPILL)
> [name=[@r00tkillah](https://twitter.com/r00tkillah)] What if we took the underlying technical elements of Linux containers and used them for evil? The result a new kind rootkit, which is even able to infect and persist in systems with UEFI secure boot enabled, thanks to the way almost every Linux system boots. This works without a malicious kernel module and therefore works when kernel module signing is used to prevent loading of unsigned kernel modules. The infected system has a nearly invisible backdoor that can be remote controlled via a covert network channel.
>
> Hope is not lost, however! Come to the talk and see how the risk can be eliminated/mitigated. While this may poke a stick in the eye of the current state of boot security, we can fix it!
>
{%youtube wyRRbow4-bc %}
:::spoiler Slides
{%pdf https://www.blackhat.com/docs/us-16/materials/us-16-Leibowitz-Horse-Pill-A-New-Type-Of-Linux-Rootkit.pdf %}
:::
### Backdoors
#### PAM
> [name=[Linux Pluggable Authentication Modules](http://www.linux-pam.org/)] PAM provides a way to develop programs that are independent of authentication scheme. These programs need "authentication modules" to be attached to them at run-time in order to work. Which authentication module is to be attached is dependent upon the local system setup and is at the discretion of the local system administrator.
>
[An Easy Guide to Linux-PAM](https://dzone.com/articles/linux-pam-easy-guide)
[Exfiltrating credentials via PAM backdoors & DNS requests](https://x-c3ll.github.io/posts/PAM-backdoor-DNS/)
:thought_balloon: Ignoring the DNS exfiltration (which is a cool, but unrelated idea, this article gives a very good overview of using PAM modules for post-exploitation)
> Probably one of the most well-known post-explotation techniques used in pentests, and in Red Team operations, is to drop a backdoor in the PAM ecosystem in order to collect valid credentials. The credentials catched by our backdoor will help us to perform easily the lateral movement between machines. We can achieve this though different options.
>
##### PAM Backdooring Approaches
* [Explicitly adding PAM backdoor](https://github.com/mthbernardes/sshLooterC)
* [In-depth overview of this approach](https://mthbernardes.github.io/persistence/2018/02/10/stealing-ssh-credentials-another-approach.html)
* [Dynamically loading a Backdoored PAM](https://github.com/eurialo/pambd)
* [Patching pam_unix.so](https://github.com/zephrax/linux-pam-backdoor)
#### Backdooring SSH
### Linux Anti-Malware & Forensics
#### Chkrootkit
> First chkrootkit release was 1997 and it was written by Klaus (CERT.br team) and the presenter. Chkrootkit is a suite of POSIX shell scripts and some tools written in ANSI C, and runs like a charm in virtually all Unix environment without dependencies. It can detect several rootkits, malicious activity (some APTs included) and can do post mortem forensic analysis to detect kernel module activities and related indicators of compromise. This tool currently detects ~70 known Rootkits, Worms and many malicious activities. This talk will discuss the features and methods used to detect rootkits and malware in general, the limitations and potential options to improve it
>
{%youtube F5jTv1wviIw %}
[Get it here](http://www.chkrootkit.org/)
#### OSSec
> [name=Daniel Cid] OSSEC HIDS is a self-contained system for Host-based intrusion detection. It performs log extraction, integrity checking and health monitoring. All this information is correlated and analyzed by a single engine, creating a very powerful detection tool.
>
<br />
{%slideshare jczucco/implementing-ossec %}
[Get it here](https://www.ossec.net/)
#### Forensics
### Notable Threats
:::spoiler Snakso.A
[HTTP iFrame Injecting Linux Rootkit](https://www.crowdstrike.com/blog/http-iframe-injecting-linux-rootkit/)
> [...], A previously unknown Linux rootkit was posted to the Full Disclosure mailing list by an anonymous victim. The rootkit was discovered on a web server that added an unknown iframe into any HTTP response sent by the web server.
>
> The victim has recovered the rootkit kernel module file and attached it to the mailing list post, asking for any information on this threat. Until today, nobody has replied on this email thread. CrowdStrike has performed a brief static analysis of the kernel module in question, and these are our results.
> * The rootkit at hand seems to be the next step in iframe injecting cyber crime operations, driving traffic to exploit kits. It could also be used in a Waterhole attack to conduct a targeted attack against a a specific target audience without leaving much forensic trail.
> * It appears that this is not a modification of a publicly available rootkit. It seems that this is contract work of an intermediate programmer with no extensive kernel experience.
> * Based on the Tools, Techniques, and Procedures employed and some background information we cannot publicly disclose, a Russia-based attacker is likely.
>
:::
:::spoiler Ebury
* https://www.welivesecurity.com/2014/02/21/an-in-depth-analysis-of-linuxebury/
* https://plog.sesse.net/blog/tech/2011-11-15-21-44_ebury_a_new_ssh_trojan.html
* https://www.cert-bund.de/ebury-faq
* https://isc.sans.edu/diary/SSHD+rootkit+in+the+wild/15229
:::
:::spoiler Chaos
* https://gosecure.net/2018/02/14/chaos-stolen-backdoor-rising/
:::
## Webserver Malware
[Introduction to Website Parasites](http://blog.unmaskparasites.com/2010/04/14/introduction-to-website-parasites/)
> Wikipedia defines Parasitism as a “type of symbiotic relationship between organisms of different species in which one, the parasite, benefits from a prolonged, close association with the other, the host, which is harmed.”
>
> This definition perfectly describes relationships between hackers and legitimate websites. As it often happens in real life, the host (legitimate website and its owner) may be completely unaware of parasites until the harmful effect becomes obvious (e.g. drops in traffic, lost search engine rankings, site gets blacklisted, etc. ). And it doesn’t matter how big or small your site is and how malicious the hack is – this is the sort of relationships where parasites (hackers) always win and legitimate websites always lose.
>
> As a webmaster, you can be more effective at detecting and mitigating parasitic activities if you know how hackers can benefit from your site .
Types of website parasitism
>
> * Parasitism on existing site traffic
> * Parasitism on search traffic
> * Parasitism on sites search engine ranking (Black-hat SEO)
> * Parasitism on server resources
### Backdoors
Presented here are some examples of implants allowing an attacker to backdoor a webserver, by abusing/hiding in the httpd proccess. This list isn't exustive, but does aim to present as wide as possible range of different ways to backdoor a wide range of httpds.
* [Apache Module Backdoor - mod_rootme](https://github.com/sajith/mod-rootme)
> Essentially, it’s an Apache module that you drop onto a box and load into Apache. Once done, you can send an appropriate request, via the given client or netcat, (essentially “GET root”), and it will drop you to a root shell on the box. Pretty nifty, right?
>
> Apache normally runs one root process, which spawns several other non-root processes, to handle requests. What mod_rootme does is when it loads, it takes advantage of the fact that it’s root for a moment, and spawns a second root Apache process (easy enough to detect for a wary sysadmin). This second Apache process just waits for an appropriate request, and spawns the shell. There’s also a hook that listens to all incoming traffic in place, waiting for the appropriate time to activate the shell. All in all pretty cool, but as noted, it’s reasonably detectable.
>
:::spoiler Additional Examples
:::info
* [Modern apache httpd backdoor module](https://www.tarlogic.com/en/blog/backdoors-modulos-apache/) - Supporting log hiding & Socks5 tunnelling
* [Backdooring Apache by injecting a backdoor at runtime](https://x-c3ll.github.io/posts/parasite-web-server-process/)
:::
* [Backdooring IIS Using an ISAPI Filter](http://esec-lab.sogeti.com/posts/2011/02/02/iis-backdoor.html)
#### PHP Backdoors
* [PHP Extension Backdoor](https://www.tarlogic.com/en/blog/backdoors-php-extensions/)
> Web servers exposed to the Internet are a traditional entry point during penetration tests and Red Team exercises. Ensuring the persistence in these perimeter actives is crucial for keeping a pivot in order to penetrate target networks. There are plenty of techniques aimed at achieving persistence. In fact, it is very common to combine them. In this particular occasion, we start a series of posts where we explain how to create backdoors (PHP extensions) in XAMP stack (OS / Apache / MySQL / PHP) and how to use them in your own penetration tests. Let’s start with backdoors in the form of PHP extensions.
>
:::spoiler Improving PHP extensions as a persistence method
:::info
> [name=[@TheXC3ll's Doomsday Vault](https://x-c3ll.github.io/posts/PHP-extension-backdoor/)]
> As Red Team we tend to use different persistence methodsin the case of a server situated in the perimeter a PHP extension is a great election.
> This is an advanced article discussing how to:
> * Reduce the tracks
> * Hooking PHP functions to extract useful info from a Red Team perspective
> * Interception of GET/POST parameters
>
:::
* [PHP OPCache Backdoor](https://gosecure.net/2016/04/27/binary-webshell-through-opcache-in-php-7/)
> In this article, we will be looking at a new exploitation technique using the default OPcache engine from PHP 7. Using this attack vector, we can bypass certain hardening techniques that disallow the file write access in the web directory. This could be used by an attacker to execute his own malicious code in a hardened environment.
>
* :thought_balloon: [Some notes on detection](https://www.gosecure.net/blog/2016/05/26/detecting-hidden-backdoors-in-php-opcache/)
#### Webshells
> [name=[MITRE ATT&CK T1100 - Webshell](https://attack.mitre.org/techniques/T1100/)]
> A Web shell is a Web script that is placed on an openly accessible Web server to allow an adversary to use the Web server as a gateway into a network. A Web shell may provide a set of functions to execute or a command-line interface on the system that hosts the Web server. In addition to a server-side script, a Web shell may have a client interface program that is used to talk to the Web server.
>
> Web shells may serve as Redundant Access or as a persistence mechanism in case an adversary's primary access methods are detected and removed.
>
:::spoiler US-Cert Advisory
:::info
[Compromised Web Servers and Web Shells - Threat Awareness and Guidance](https://www.us-cert.gov/ncas/alerts/TA15-314A)
> This alert describes the frequent use of web shells as an exploitation vector. Web shells can be used to obtain unauthorized access and can lead to wider network compromise. This alert outlines the threat and provides prevention, detection, and mitigation strategies.
>
:::
:thought_balloon: [Webshell && Backdoor Collection](https://github.com/xl7dev/WebShell) (don't use in production)
> A collection of multiple, mainly web application oriented, webshells & backdoors
>
:::spoiler PHP Webshell obfuscation
[PHP Backdoor Obfuscation Techniques](https://vexatioustendencies.com/php-backdoor-obfuscation-techniques/)
> When an attacker leaves behind malicious PHP after a successful compromise, they typically make some attempt to obfuscate their code. While the title of this post is “PHP Backdoor Obfuscation Techniques”, these methods are also used to obfuscate other code as well, sometimes even in a poor attempt to protect legitimate code from reverse engineering and modification. I’ve been working in an environment with a large number of LAMP servers for several years now, and I’ve seen a lot of malicious PHP. Here are some of the more common (and a few less common) obfuscation techniques I’ve seen.
:::
### Notable Threats
:::spoiler [pseudo-]Darkleech/Chapro.A
A notorious family of malware that plagued linux servers from 2012 till 2016, taking control of infected servers in order to serve webinjects to site visitors or turn the infected servers into exploit kit proxies. This innovative malware family introduced and popularized a significant number of techniques for attacking web servers, seldom seen in the wild even come 2020.
1. [First sighting in the wild](http://blog.unmaskparasites.com/2012/08/13/rfi-server-wide-iframe-injections/)
> This summer I come across some clearly infected servers where I can’t figure out how exactly the hack works and what should be done to clean them up and to protect other servers from similar hacks. So I decided to share my information about the issue and hope someone could shed some light on it.
2. [A realization - Malicious Apache Module Injects Iframes](http://blog.unmaskparasites.com/2012/09/10/malicious-apache-module-injects-iframes/) - This malware would later be called Darkleech
> It’s a follow up to my post about server-wide iframe injection attack where I asked for any information about that tricky hack. Thanks to [...] administrators of infected servers I have some new information about it. Now I know how it works and what is infected, but still have no idea how hackers break into servers, so your input is welcome.
>
:::spoiler Additional Analysis
* [Malicious Apache module used for content injection: Linux/Chapro.A](https://www.welivesecurity.com/2012/12/18/malicious-apache-module-used-for-content-injection-linuxchapro-a/)
> The malicious Apache module we have analyzed is detected by ESET as Linux/Chapro.A. the primary purpose of which is to inject malicious content into web pages served up by the compromised server (as diagrammed on the right where an iframe is injected, but it could be malicious JavaScript or something else).
>
* [Possible Darkleech source code](https://pastebin.com/raw/6wWVsstj) - circa 2012
:::
3. The Home Campaign
* [Some wider context by Arstechnica](https://arstechnica.com/information-technology/2013/04/exclusive-ongoing-malware-attack-targeting-apache-hijacks-20000-sites/)
> Tens of thousands of websites, some operated by The Los Angeles Times, Seagate, and other reputable companies, have recently come under the spell of "Darkleech," a mysterious exploitation toolkit that exposes visitors to potent malware attacks.
>
> The ongoing attacks, estimated to have infected 20,000 websites in the past few weeks alone, are significant because of their success in targeting Apache, by far the Internet's most popular Web server software. Once it takes hold, Darkleech injects invisible code into webpages, which in turn surreptitiously opens a connection that exposes visitors to malicious third-party websites, researchers said. Although the attacks have been active since at least August, no one has been able to positively identify the weakness attackers are using to commandeer the Apache-based machines. Vulnerabilities in Plesk, Cpanel, or other software used to administer websites is one possibility, but researchers aren't ruling out the possibility of password cracking, social engineering, or attacks that exploit unknown bugs in frequently used applications and OSes.
* Remeditation effort - [The Evil Came Back: Darkleech's Apache Malware Module: Recent Infection, Reversing, Prevention & Source Details](https://blog.malwaremustdie.org/2013/03/the-evil-came-back-darkleechs-apache.html)
* Technical details - [The Home Campaign: overstaying its welcome](https://www.welivesecurity.com/2013/07/02/the-home-campaign-overstaying-its-welcome/)
> The Home Campaign is a malware campaign that uses a modified variant of Darkleech to direct visitors to the Blackhole exploit kit. We want to give a better idea of the size and extent of this campaign.
4. [Darkleech + Bitly.com = Insightful Statistics](https://blog.sucuri.net/2014/02/darkleech-bitly-com-insightful-statistics.html)
> This post is about how hackers abuse popular web services and how this helps security researchers obtain interesting statistics about malware attacks.
5. Pseudo-Darkleech
During 2015 the group behind Darkleech swirthed tactics to infecting PHP files instead of infecting the httpd itself.
* [WordPress Malware Causes Psuedo-Darkleech Infection](https://blog.sucuri.net/2015/03/pseudo-darkleech-server-root-infection.html)
> [...] Sometimes the malware was hard to reproduce, but on some sites it was reproducible on every load. What was even stranger is that we saw this on IIS servers (with PHP support) too. We had not heard of Darkleech infecting IIS web servers.
* [Website Malware – Evolution of Pseudo Darkleech](https://blog.sucuri.net/2015/12/evolution-of-pseudo-darkleech.html)
* [Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond](https://unit42.paloaltonetworks.com/unit42-campaign-evolution-darkleech-to-pseudo-darkleech-and-beyond/)
* [Campaign Evolution: pseudo-Darkleech in 2016](https://researchcenter.paloaltonetworks.com/2016/12/unit42-campaign-evolution-pseudo-darkleech-2016/)
:::
:::spoiler Cdorked.A
:::
## IoT
{%youtube Qs4OcQNOM34 %}
{%slideshare mazlan1/internet-of-things-iot-we-are-at-the-tip-of-an-iceberg %}
:::spoiler
:::info
{%slideshare ValaAfshar/internet-of-thingsslideshare %}
{%slideshare PascalBodin/iot-and-connected-devices-an-overview %}
:::
### Security
{%slideshare narudomr/iot-security-81762130 %}
{%slideshare CableLabs/the-state-of-iot-security-keynote-by-shawn-henry-at-informed-iot-security %}
{%slideshare bz98/hacktivity-2016-the-real-risks-of-the-iot-securitynightmare-hacking-ip-cameras-through-the-cloud %}
{%speakerdeck duosec/internet-of-fails-where-iot-has-gone-wrong-and-how-were-making-it-right %}
{%slideshare MenderOTA/linux-iot-botnet-wars-and-the-lack-of-basic-security-hardening-oscon-2018 %}
{%slideshare BiagioBotticelli/iot-honeypots-state-of-the-art %}
https://embedi.com/blog/reflecting-upon-owasp-top-10-iot-vulnerabilities/
https://securelist.com/honeypots-and-the-internet-of-things/78751/
https://securelist.com/new-trends-in-the-world-of-iot-threats/87991/
https://www.owasp.org/index.php/OWASP_Internet_of_Things_Project
### Malware
:::spoiler Carna
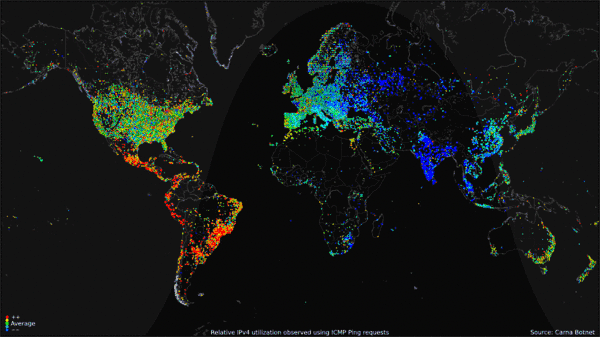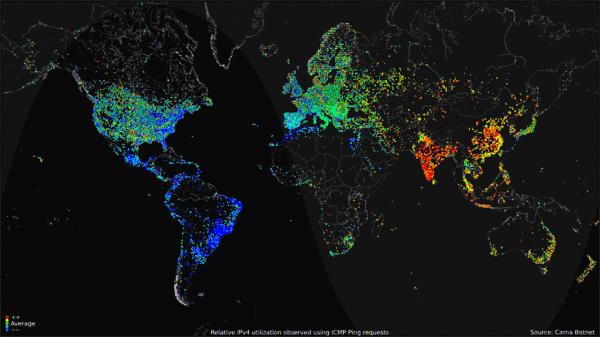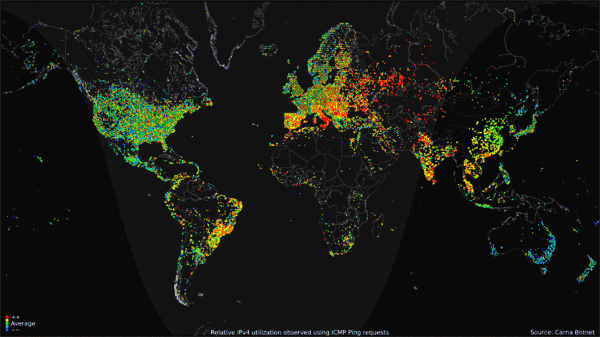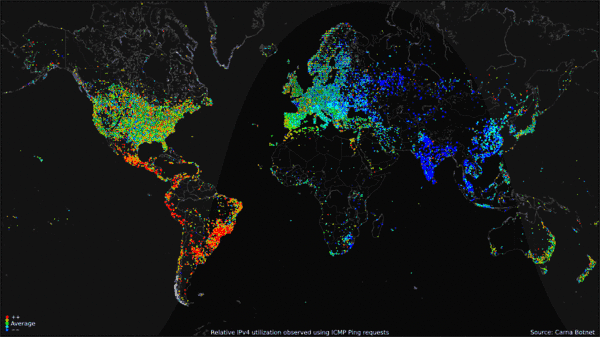
The Carna Botnet/[Internet Census 2012](http://census2012.sourceforge.net/paper.html)
> 
>
> While playing around with the Nmap Scripting Engine (NSE) we discovered an amazing number of open embedded devices on the Internet. Many of them are based on Linux and allow login to standard BusyBox with empty or default credentials. We used these devices to build a distributed port scanner to scan all IPv4 addresses. These scans include service probes for the most common ports, ICMP ping, reverse DNS and SYN scans. We analyzed some of the data to get an estimation of the IP address usage.
>
> All data gathered during our research is released into the public domain for further study.
:::
:::spoiler SYNful Knock
* https://www.fireeye.com/blog/threat-research/2015/09/synful_knock_-_acis.html
* https://www.fireeye.com/blog/threat-research/2015/09/synful_knock_-_acis0.html
:::
:::spoiler Mirai
https://www.incapsula.com/blog/malware-analysis-mirai-ddos-botnet.html
*
https://www.fortinet.com/blog/threat-research/omg--mirai-based-bot-turns-iot-devices-into-proxy-servers.html
*
(*) https://www.slideshare.net/MSbluehat/bluehat-v17-disrupting-the-mirai-botnet
:::spoiler BrickerBot
https://ghostbin.com/paste/q2vq2
*
(*) https://archive.fo/RTVpt (mod_plain.py)
:::
:::spoiler VPNFilter
* https://blog.talosintelligence.com/2018/05/VPNFilter.html
* https://blog.talosintelligence.com/2018/06/vpnfilter-update.html
* https://blog.talosintelligence.com/2018/09/vpnfilter-part-3.html
* https://blog.rapid7.com/2018/06/07/vpnfilter-potential-reach/
:::
:::spoiler Mikrotik Malware
https://blog.netlab.360.com/7500-mikrotik-routers-are-forwarding-owners-traffic-to-the-attackers-how-is-yours-en/
:::
:::spoiler Torii
https://blog.avast.com/new-torii-botnet-threat-research
:::
:::spoiler QBot
:::
### Exploitation
{%speakerdeck v33ru/iot-security-beginners-guide %}
https://github.com/threat9/routersploit
https://github.com/firmadyne/firmadyne
https://p16.praetorian.com/blog/getting-started-with-damn-vulnerable-router-firmware-dvrf-v0.1
http://blog.exploitlab.net/2018/01/dvar-damn-vulnerable-arm-router.html
:::spoiler Notable Exploits
:::warning
- [ ] TODO: What makes an exploit notable enough to be here..?
:::info
* [(Mis)fortune Cookie](http://mis.fortunecook.ie/)
* [GoAhead HTTPd LD_PRELOAD RCE](https://www.elttam.com.au/blog/goahead/)
* [XiongMai uc-httpd](https://github.com/bitfu/uc-httpd-1.0.0-buffer-overflow-exploit)
* [GPON Routers](https://www.vpnmentor.com/blog/critical-vulnerability-gpon-router/)
#### Mikrotik
* [Chimay Red RCE](https://github.com/BigNerd95/Chimay-Red)
*
Asus Routers
*
http://sploit.tech/2018/01/16/ASUS-part-I.html
*
http://sploit.tech/2018/01/16/ASUS-part-II.html
*
https://www.securityartwork.es/2018/01/25/some-vulnerability-in-asus-routers/
*
Tenda Routers
*
https://www.fidusinfosec.com/remote-code-execution-cve-2018-5767/
*
https://www.fidusinfosec.com/tenda-ac15-unauthenticated-telnetd-start-cve-2018-5770/
*
https://www.fidusinfosec.com/tenda-ac15-hard-coded-accounts-cve-2018-5768/
*
TP-Link Routers
*
https://www.fidusinfosec.com/tp-link-remote-code-execution-cve-2017-13772/
*
https://www.fidusinfosec.com/a-curious-case-of-code-reuse-tplink-cve-2017-13772-v2/
*
D-Link
*
https://www.fidusinfosec.com/dlink-dcs-5030l-remote-code-execution-cve-2017-17020/
*
https://blogs.securiteam.com/index.php/archives/3364
*
https://pierrekim.github.io/blog/2017-09-08-dlink-850l-mydlink-cloud-0days-vulnerabilities.html
*
Generic DVRs
*
https://ipvm.com/reports/security-exploits
*
https://github.com/mcw0/PoC
*
https://github.com/mcw0/PoC/blob/master/Avtech_Undocumented_API_and_RCE.txt
*
https://github.com/mcw0/PoC/blob/master/TVT_and_OEM_IPC_NVR_DVR_RCE_Backdoor_and_Information_Disclosure.txt
*
https://github.com/ezelf/CVE-2018-9995_dvr_credentials
*
Generic IP Camera
*
https://pierrekim.github.io/blog/2017-03-08-camera-goahead-0day.html
*
LG NAS - https://www.vpnmentor.com/blog/critical-vulnerability-found-majority-lg-nas-devices/
*
QNAP NAS
*
https://www.coresecurity.com/advisories/qnap-qcenter-virtual-appliance-multiple-vulnerabilities
*
*
JAWS
*
https://www.pentestpartners.com/security-blog/pwning-cctv-cameras/
*
NUUO
*
https://www.tenable.com/security/research/tra-2018-25
*
Asustor NAS
*
https://blog.securityevaluators.com/unauthenticated-remote-code-execution-in-asustor-as-602t-
Tenda
https://blog.securityevaluators.com/tenda-ac1900-vulnerabilities-discovered-and-exploited-e8e26aa0bc68
:::