# **Analysis of Ayushman Card Application (Scam_App)**
When I returned from the exam, I noticed that someone had sent a random application in the WhatsApp group. This person had literally shared the app in all the groups. Later, I found out that their phone had been hacked. However, I was curious to see what was inside the 2MB application and how it worked.

Upon initial investigation, it flagged several viruses and trojans.


The next step was to analyze its source code.

`android.permission.RECEIVE_SMS, android.permission.SEND_SMS, and android.permission.READ_SMS:`
Hmm, that seems sus! Asking for permission to access SMS? That’s a classic red flag! Always be cautious with apps that request such permissions. Better safe than sorry!
`android:exported="true"`
This makes the activity accessible from outside the app, allowing me to use ADB in the terminal to run this app
The AndroidManifest file helps us understand the overall app permissions, which serves as the basic starting point for the attack.
After spending a few minutes, I found an interesting piece of code that constitutes the entire program logic.

`SILENTKILLER333`
Ah, this sweet code has the secret key not stored or obfuscated, making the developer seem careless. They should have at least stored it in a different parameter or obfuscated it to make it more difficult to access.
`Cipher.getInstance("DES") and SecretKeyFactory.getInstance("DES")` indicate that the encryption uses the **DES** algorithm, which requires a key to decrypt. We have the key, but where is the data we want to crack? It's like getting the answer without having the question.
Upon further investigation, I found the main activity in the code, which had a stored string
`public static final String store_num = EncryptionUtils.decrypt("eUlTC2MiOnL0JoptgyHQbg==");`
wrote a python3 code to decrypt the encrypted string

**I decrypted the string and obtained the attacker's number.**

*(+919279428165)*
I don't have much trust in Truecaller, as anyone can change their name on it. Rather, I have a private, better tool for scanning numbers that directly provides us with the name under which the number was registered.

Though I tried to contact him on Telegram, he has been offline for the last 7 hours

This hides the app icon and Sends a confirmation SMS ("Extreme Moderate App Installed!") to the phone number stored(the attacker number)

This snippet listens for incoming SMS messages, extracts potential OTPs or codes, and forwards them to a predefined number `(f2102a)`
## ***Tested the app on andriod emulator***
[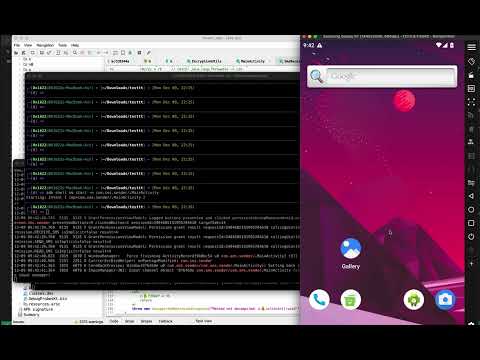](https://www.youtube.com/watch?v=Tp7syIqboF4)
I wrote the blog for the first time. Please ignore any grammatical mistakes, and feel free to DM me if you have any questions."
Contact me : [**Linkedin**](https://www.linkedin.com/in/shriram-dhumal/)
Discord - 0x1622